Urgent Cybersecurity Alert: CISA Elevates HPE OneView Flaw to Actively Exploited Status, Mandating Immediate Remediation
The United States Cybersecurity and Infrastructure Security Agency (CISA) has issued a critical warning, identifying a maximum-severity vulnerability within Hewlett Packard Enterprise (HPE) OneView software, designated CVE-2025-37164, as actively exploited…
OpenAI Elevates AI-Powered Coding with the Phased Introduction of GPT-5.2 Codex-Max
OpenAI is progressively deploying an advanced iteration of its specialized coding model, designated GPT-5.2 Codex-Max, to a segment of its premium user base, marking a significant evolution in AI-assisted software…
The Evolving Dichotomy: Are Generative AI Injection Flaws Inherently Vulnerabilities or Systemic Design Constraints?
The discourse surrounding the security posture of advanced generative artificial intelligence platforms has intensified, ignited by a recent disagreement between a cybersecurity expert and a leading technology vendor. This escalating…
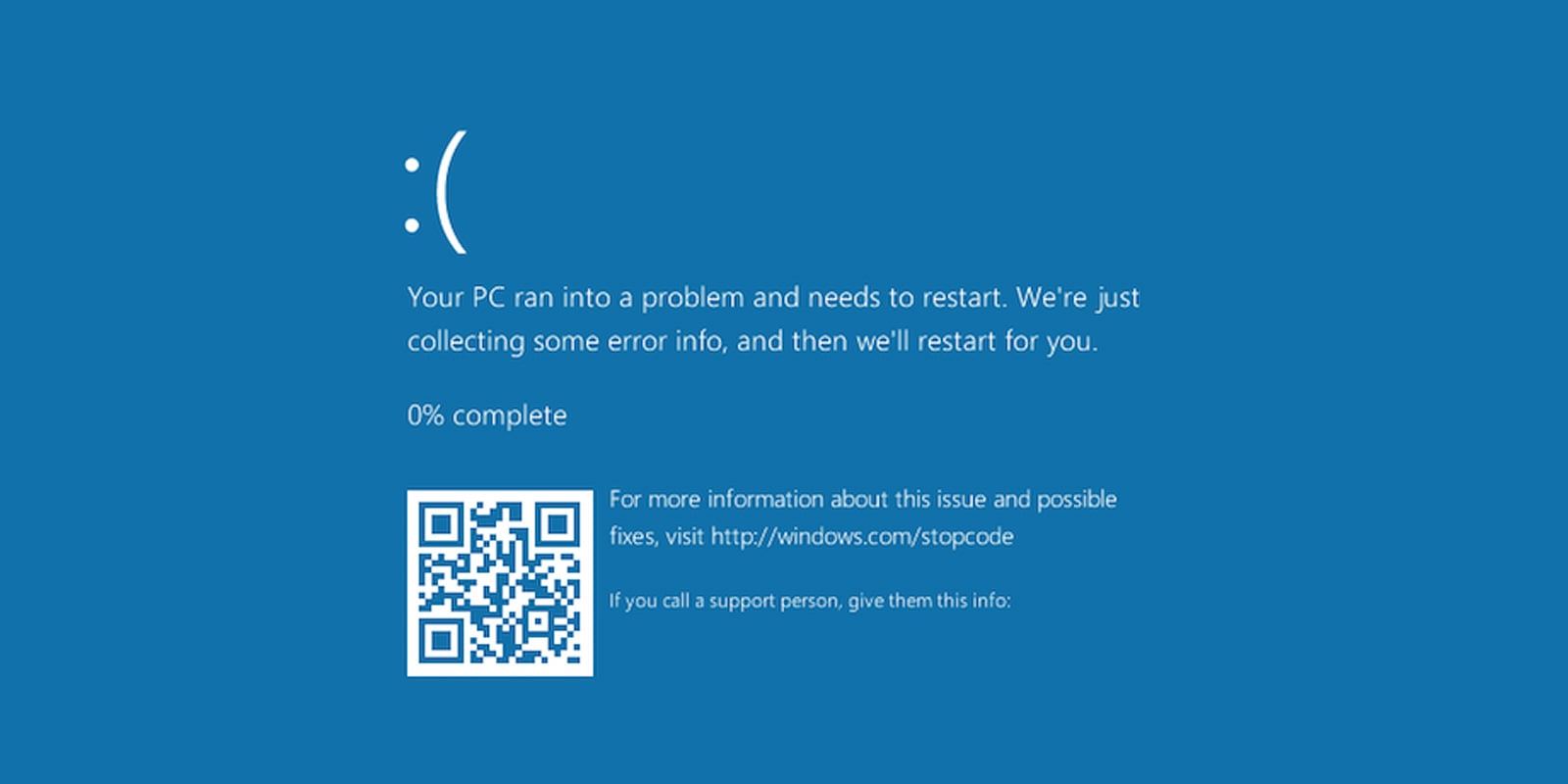
Deceptive System Crashes: How Advanced ClickFix Operations Target Hospitality with Malicious Prompts
A sophisticated social engineering campaign is currently leveraging fabricated Windows system crash screens to manipulate individuals within the European hospitality sector into inadvertently compromising their own computer systems. This operation,…
Enterprise Cloud Storage Under Siege: Sophisticated Credential Theft Fuels Widespread Data Exfiltration Campaigns
A recent surge in illicit activities by an advanced cybercriminal collective underscores a pervasive vulnerability within enterprise cloud file-sharing ecosystems, leading to the unauthorized acquisition and subsequent commercialization of sensitive…
Third-Party E-Commerce Platform Breach Compromises Customer Data Across Multiple Global Brands, Including Ledger
A significant cybersecurity incident impacting Global-e, a prominent third-party e-commerce solutions provider, has led to the unauthorized disclosure of personal identification details belonging to customers of various online retailers, including…
Trust Wallet Breach Linked to Shai-Hulud NPM Campaign, Exposing Software Supply Chain Vulnerabilities and Crypto Ecosystem Risks
A recent security incident impacting Trust Wallet, resulting in the theft of approximately $8.5 million from over 2,500 cryptocurrency wallets, is now believed to be a direct consequence of or…
Google Accelerates Visual AI Frontier with New High-Efficiency Image Generation Model
Google is poised to significantly advance the accessibility and speed of artificial intelligence in image generation with the impending release of its "Nano Banana 2 Flash" model. This new iteration,…
Cybersecurity Firm Resecurity Alleges Strategic Deception Amidst Hacker Breach Claims
A prominent collective of cyber threat actors, identifying themselves as "Scattered Lapsus$ Hunters," has publicly asserted a significant compromise of the cybersecurity entity Resecurity, purporting to have exfiltrated extensive internal…
Pervasive Threat: Over 10,000 Fortinet Firewalls Remain Susceptible to Long-Standing 2FA Bypass Vulnerability Amid Active Exploitation Campaigns
Thousands of network security appliances from Fortinet, specifically FortiGate firewalls, continue to operate with a critical, five-year-old two-factor authentication (2FA) bypass vulnerability, exposing organizations to persistent and actively observed exploitation…