Cloud solutions aggregator Pax8 recently confirmed an incident where an internal spreadsheet containing sensitive business and Microsoft licensing data pertinent to approximately 1,800 Managed Service Provider (MSP) partners was mistakenly distributed to a limited number of its UK-based partners, raising significant concerns about competitive intelligence and cybersecurity vulnerabilities within the IT channel. This unintentional exposure underscores the complex challenges inherent in safeguarding confidential information across intricate digital supply chains, even in the absence of directly identifiable personal data.
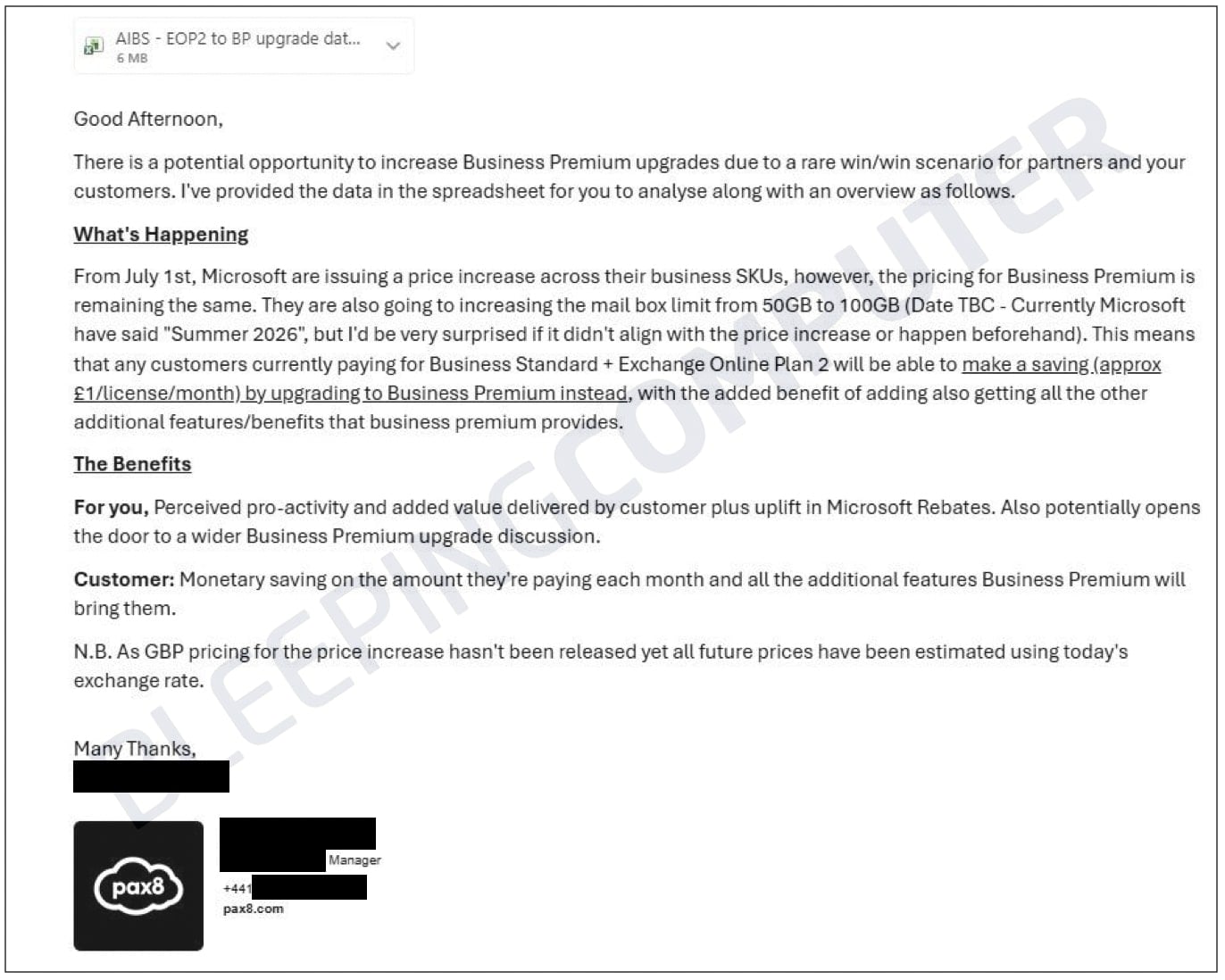
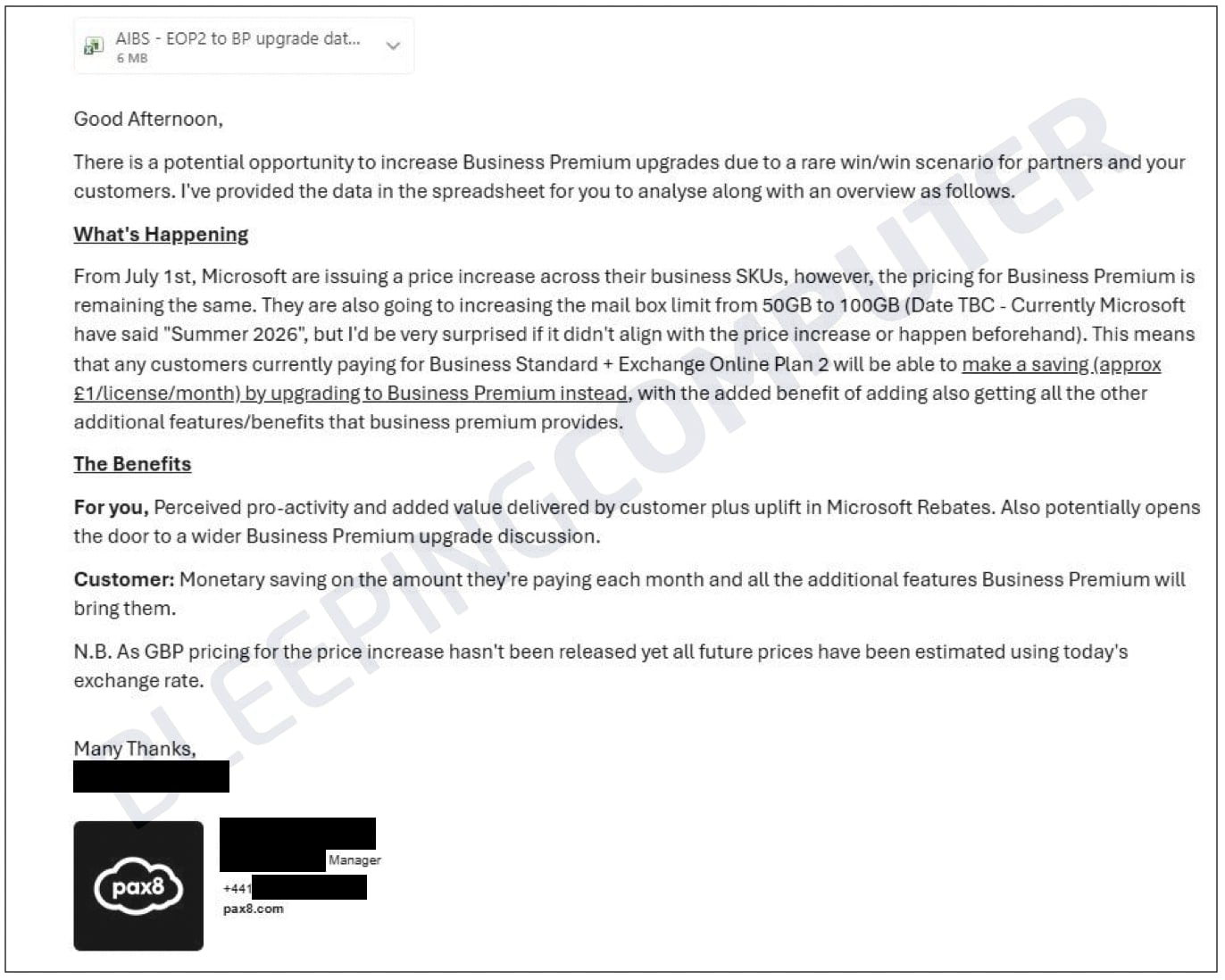
The incident, which transpired on January 13, 2026, involved an email originating from an EMEA-based strategic account manager. The message, provocatively titled "Potential Business Premium Upgrade Tactic to Save Money," was dispatched to fewer than 40 recipients within the United Kingdom. Attached to this email was a CSV file containing what Pax8 describes as internal business information, specifically detailing MSP customer portfolios and critical Microsoft licensing specifics. While the immediate recipient pool was small, the ramifications are extensive, impacting a substantial segment of Pax8’s partner ecosystem.
Pax8, a formidable force in the cloud commerce landscape, boasts a global footprint that includes over 47,000 partners across 18 countries and a workforce exceeding 1,700 employees. The company’s impressive trajectory recently saw it surpass $2 billion in annual revenue, with particularly robust expansion observed throughout Europe. This rapid growth and extensive network underscore the gravity of any operational misstep, as a breach in their systems or processes can cascade through a vast network of dependent businesses. Their position as a pivotal intermediary, connecting vendors like Microsoft with thousands of MSPs, places a high premium on data integrity and secure operational practices.

Upon analysis by affected MSPs, the inadvertently distributed CSV file revealed a wealth of granular detail. It reportedly contained more than 56,000 individual entries, encompassing critical data points such as customer organization names, specific Microsoft Stock Keeping Units (SKUs), precise license counts for various Microsoft products, and crucial New Commerce Experience (NCE) renewal dates. This level of detail, traditionally visible only to the managing MSP and Pax8 itself, constitutes highly sensitive commercial intelligence. One partner in Canada was also identified among the affected entities, though the primary impact was concentrated in the UK.
Immediately following the transmission of the erroneous email, the sender initiated an attempted message recall. This was swiftly followed by a subsequent communication to recipients, explicitly requesting the deletion of the original email and its attachment, acknowledging the prior transmission as an error. In their follow-up notice, Pax8 assured partners that the file did not contain personally identifiable information (PII). However, they conceded that the file did include "limited internal business information reflective of your Pax8 pricing and some Microsoft program management," which could inadvertently reveal MSP pricing structures and client portfolios.
Pax8’s communication to its partners outlined a series of immediate actions taken to mitigate the incident. These included directly contacting each recipient to request and confirm deletion and non-forwarding of the email and attachment, conducting one-on-one follow-up calls to reinforce these directives, and launching an internal review to ascertain the root cause and implement preventative measures. The company reiterated its commitment to protecting partner-confidential information, though the incident itself highlights a lapse in these protective protocols.
The implications of such a data exposure extend far beyond the immediate technical fix. For Pax8, the incident poses a significant challenge to its reputation and the trust it has meticulously built with its extensive partner network. In a highly competitive market, the perception of security and reliability is paramount. A breach of confidential partner data, even if accidental and lacking PII, can erode confidence and potentially lead to partners reevaluating their reliance on the platform.

From a competitive standpoint, the leaked dataset represents an invaluable trove of intelligence. Rival cloud distributors or competing MSPs could potentially leverage this information to gain an unfair advantage. Knowing an organization’s specific Microsoft product usage, the scale of their deployments, their current licensing costs, and, crucially, their NCE renewal dates, provides a powerful arsenal for targeted sales and poaching strategies. Competitors could time their outreach to coincide with renewal cycles, offering seemingly tailored solutions or more aggressive pricing, thereby undermining existing MSP-client relationships and Pax8’s distribution agreements. The exposure of internal pricing models, even if generalized, further compounds this competitive threat.
Perhaps the most alarming implication stems from the potential exploitation by malicious actors. Industry sources have reportedly indicated that threat actors are actively seeking to acquire copies of the exposed dataset from affected MSPs. This signals a clear and present danger that the information could be weaponized for sophisticated cyberattacks. The dataset functions as a high-quality targeting list, enabling cybercriminals to craft highly credible phishing campaigns, business email compromise (BEC) schemes, or even direct extortion attempts.
Consider the scenario: a threat actor, armed with knowledge of an organization’s specific Microsoft SKUs and NCE renewal dates, could impersonate Pax8 or the client’s managing MSP during a critical licensing period. Phishing emails could appear exceptionally legitimate, discussing specific license upgrades, renewal confirmations, or payment adjustments, making them far more difficult for recipients to discern as malicious. This heightened credibility drastically increases the likelihood of a successful compromise, potentially leading to financial fraud, ransomware deployment, or broader network infiltration. The fact that the data also identifies which MSP manages which client environment creates a perfect blueprint for supply chain attacks, targeting the MSP as a gateway to multiple client networks.
The incident also sheds light on the broader challenges of data governance and operational security within large, rapidly expanding organizations. While Pax8’s growth is commendable, it simultaneously amplifies the complexity of managing internal data flows and preventing human error. The mistaken distribution of a sensitive spreadsheet points to potential weaknesses in several areas: employee training on data handling protocols, access controls for sensitive internal documents, and automated systems designed to prevent the unauthorized or incorrect transmission of confidential information. The reliance on manual processes for distributing such critical data, rather than secure, controlled platforms, appears to be a significant vulnerability.
Pax8’s immediate response, including recall attempts and direct partner communication, is a standard protocol in such incidents. However, the effectiveness of a recall, particularly via email, is often limited, as recipients may have already opened, downloaded, or forwarded the attachment. The request for confirmation of deletion, while well-intentioned, relies heavily on the goodwill and diligence of recipients, offering no absolute guarantee of data eradication. The absence of PII, while a relief, does not diminish the strategic and financial value of the exposed business intelligence.
This event serves as a stark reminder of the interconnected nature of modern cloud ecosystems and the cascading risks associated with supply chain vulnerabilities. MSPs rely heavily on distributors like Pax8 for efficient access to vendor products and services. A breach at the distributor level can therefore expose thousands of downstream businesses to various forms of exploitation, highlighting the need for robust security postures not just at the end-user level, but throughout the entire digital supply chain.
For MSPs, this incident necessitates a heightened state of vigilance. They must reinforce internal cybersecurity training, particularly regarding phishing and social engineering attacks that leverage specific business context. Diversifying their distributor relationships, where feasible, could also be considered as a risk mitigation strategy. Furthermore, MSPs should proactively engage with their clients to explain the broader risks associated with such supply chain exposures and ensure robust security measures are in place at the client level.
Looking ahead, Pax8 faces the imperative of conducting a thorough and transparent internal review to identify and rectify the systemic weaknesses that permitted this exposure. This must extend beyond mere procedural adjustments to include technological enhancements for data access control, secure information sharing, and advanced email security gateways. Implementing data loss prevention (DLP) solutions and mandating secure, audited channels for the distribution of sensitive internal data will be crucial. Rebuilding partner trust will depend not only on their swift actions but also on their demonstrable commitment to preventing future occurrences through robust security and governance frameworks.

The regulatory landscape surrounding data breaches is also evolving. While PII was not directly involved, the exposure of commercially sensitive information pertaining to thousands of businesses could still attract scrutiny from data protection authorities, particularly concerning the adequacy of security measures for confidential business data. The incident underscores that "data breach" encompasses more than just personal information; any unauthorized disclosure of sensitive business intelligence carries significant consequences.
In conclusion, the inadvertent data exposure by Pax8, though limited in its immediate recipient pool, carries profound implications for competitive dynamics, cybersecurity risk, and trust within the cloud IT channel. It highlights the critical importance of rigorous data governance, robust operational security, and continuous employee training in an era where digital supply chains are increasingly complex and vulnerable. As the digital economy continues its expansion, the responsibility to safeguard all forms of sensitive data, whether personal or commercial, becomes an ever more pressing imperative for all participants in the ecosystem.







