
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued a stringent directive to federal government entities, compelling them to swiftly implement patches for a high-severity remote code execution (RCE) vulnerability within the Gogs self-hosted Git service, a flaw identified as being actively exploited in sophisticated zero-day attacks. This imperative underscores the escalating threat landscape faced by critical infrastructure and governmental systems, with CISA leveraging its authority to enforce rapid response to vulnerabilities deemed a significant risk to national security.
Gogs, an open-source, lightweight Git service written in Go, presents itself as a viable alternative to more comprehensive platforms like GitLab or GitHub Enterprise. Its appeal often lies in its simplicity, minimal resource footprint, and ease of self-hosting, making it a popular choice for smaller development teams, internal projects, or specific environments requiring a localized code management solution. However, its design, when coupled with internet exposure—a common configuration for remote collaboration—renders it a prime target for malicious actors seeking to compromise software development pipelines or gain initial access to enterprise networks.
The vulnerability at the heart of CISA’s urgent mandate is tracked as CVE-2025-8110. This critical flaw resides within the PutContents API, a function designed to facilitate content updates within repositories. Technically, it is a path traversal weakness that sophisticated attackers have leveraged to circumvent existing security measures. Specifically, this vulnerability allows authenticated threat actors to bypass protections that were implemented to address a preceding RCE bug, CVE-2024-55947. The bypass mechanism hinges on the abuse of symbolic links, enabling an attacker to manipulate file paths and overwrite arbitrary files located outside the intended boundaries of a repository.
The attack vector is particularly insidious. Malicious actors initiate the compromise by creating specially crafted repositories containing symbolic links. These symlinks are not benign; they are strategically configured to point to sensitive system files located elsewhere on the server. Once the malicious repository is established, the attackers then utilize the PutContents API, not to write data within the repository, but to transmit data through these forged symlinks. This allows them to effectively overwrite target files anywhere on the file system, bypassing normal access controls and file-writing restrictions. A prime target for such an overwrite is critical Git configuration files, particularly the sshCommand setting. By altering this specific configuration, threat actors can inject and execute arbitrary commands on the compromised server, achieving full remote code execution capabilities. This level of control grants attackers the ability to exfiltrate data, deploy further malware, establish persistent backdoors, or pivot deeper into the network.

The discovery of CVE-2025-8110 was attributed to Wiz Research, a cybersecurity firm that uncovered the flaw during an investigation into a malware infection affecting one of their client’s internet-facing Gogs servers in July of the previous year (2025, assuming the CVE and CISA directive timeline). Wiz Research promptly reported the vulnerability to the Gogs maintainers on July 17. Disturbingly, the acknowledgment from the Gogs development team did not arrive until three months later, on October 30. This considerable delay in acknowledging a critical vulnerability, especially one actively exploited, highlights a significant challenge in open-source project security: the often-limited resources and voluntary nature of maintainers can lead to slower response times compared to commercial software vendors. Patches for CVE-2025-8110 were subsequently released in late 2025, specifically designed to introduce symlink-aware path validation across all file-write entry points within the Gogs application.
However, the threat landscape had already shifted. According to a detailed disclosure timeline shared by Wiz Research, a second, more aggressive wave of attacks targeting this very vulnerability as a zero-day was observed on November 1, 2025. This indicates that even as the vendor was preparing a fix, threat actors were intensifying their exploitation efforts, underscoring the urgency and real-world impact of the flaw. The existence of a "second wave" suggests either a broader deployment of the exploit by the initial attackers or the entry of new threat groups into the fray, leveraging information about the vulnerability’s existence.
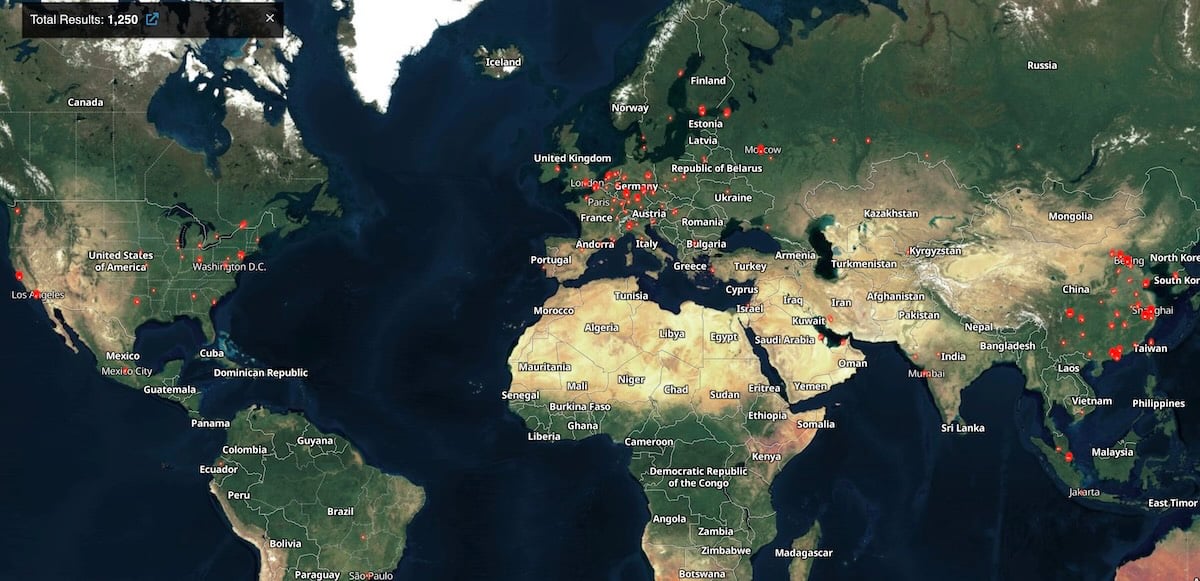
During their investigative campaigns, Wiz researchers identified a startling number of vulnerable Gogs instances exposed to the public internet. Their findings, leveraging internet scanning services like Shodan, revealed over 1,400 Gogs servers openly accessible online, with approximately 1,250 of these instances remaining exposed at the time of the CISA directive. Even more alarming was the discovery that more than 700 of these internet-exposed instances exhibited clear signs of compromise, signifying a widespread and successful exploitation campaign. The sheer volume of compromised servers underscores the critical importance of secure configuration, rigorous patching, and continuous monitoring for self-hosted applications, especially those managing sensitive intellectual property like source code. The image depicting internet-exposed Gogs instances from Shodan serves as a stark visual reminder of the extensive attack surface.
In response to the confirmed active exploitation and the widespread exposure, CISA officially acknowledged Wiz’s findings and formally added CVE-2025-8110 to its authoritative Known Exploited Vulnerabilities (KEV) Catalog on January 12, 2026. This action is not merely an advisory; it triggers a binding operational directive (BOD 22-01) for all Federal Civilian Executive Branch (FCEB) agencies. These non-military U.S. executive branch agencies, which include critical departments such as Energy, Justice, Homeland Security, and State, are now mandated to patch all affected systems within an exceptionally tight timeframe of three weeks, setting a deadline of February 2, 2026.

CISA’s rationale for this urgent directive is clear and unequivocal: "This type of vulnerability is a frequent attack vector for malicious cyber actors and poses significant risks to the federal enterprise." The agency explicitly warned that FCEB agencies must apply vendor-provided mitigations, adhere to applicable BOD 22-01 guidance for cloud services, or, if no effective mitigations are available, discontinue the use of the product entirely. This strong stance reflects the severity of RCE vulnerabilities, particularly those actively exploited, which offer adversaries a direct path to system control and potential network compromise.
Beyond immediate patching, CISA and cybersecurity experts recommend several crucial mitigation strategies to reduce the attack surface for Gogs users. The foremost recommendation is to immediately disable the default open-registration setting, a common misconfiguration in many self-hosted applications that allows any user to create an account, thereby providing an easy entry point for authenticated attackers. Furthermore, limiting server access through robust network controls, such as implementing a Virtual Private Network (VPN) or an IP allow list, can drastically reduce exposure to unauthorized entities. These measures ensure that only trusted users or networks can even attempt to access the Gogs instance, forming a critical layer of defense.
For administrators suspecting compromise, CISA and Wiz Research provided specific Indicators of Compromise (IoCs). These include monitoring for suspicious usage patterns of the PutContents API, which would indicate attempts to write data to unintended locations. Additionally, administrators should actively search for the presence of newly created repositories exhibiting random, eight-character names, particularly those created during the two identified attack waves (July and November 2025). These anomalous repositories are likely artifacts of the attackers’ initial foothold and exploit chain. Regular log analysis, file integrity monitoring, and network traffic inspection are indispensable tools for detecting such indicators.
The broader implications of this incident extend beyond the immediate threat to Gogs users. It underscores the pervasive challenges in securing the software supply chain, where vulnerabilities in development tools can cascade into widespread compromise. The incident highlights the delicate balance between the agility and community benefits of open-source software and the imperative for robust security practices, including timely vulnerability disclosure and patching by maintainers. Government agencies, in particular, must navigate the complexities of adopting diverse software solutions while adhering to stringent cybersecurity mandates.
CISA’s proactive stance, through its KEV catalog and binding directives, represents a critical component of the national cybersecurity strategy. By focusing on vulnerabilities known to be actively exploited, the agency ensures that federal resources are prioritized to address the most immediate and dangerous threats. This shift towards a more threat-informed and proactive security posture is essential in an environment where state-sponsored actors and sophisticated criminal groups continually seek to exploit any weakness in critical systems. The incident serves as a stark reminder that even seemingly niche or lightweight applications, when exposed to the internet, can become high-value targets, demanding the same rigorous security scrutiny as any mission-critical enterprise system. The ongoing battle against zero-day exploits necessitates continuous vigilance, rapid response, and a collaborative effort between security researchers, software developers, and government bodies to fortify digital defenses against an ever-evolving adversary landscape.







