A sophisticated social engineering campaign is currently leveraging fabricated Windows system crash screens to manipulate individuals within the European hospitality sector into inadvertently compromising their own computer systems. This operation, identified by cybersecurity researchers, involves highly convincing phishing lures that direct victims to meticulously crafted fake websites, ultimately coercing them into executing malicious code under the guise of system recovery. The incident underscores a critical evolution in attacker tactics, blending advanced visual deception with psychological manipulation to bypass traditional security measures and establish persistent unauthorized access.
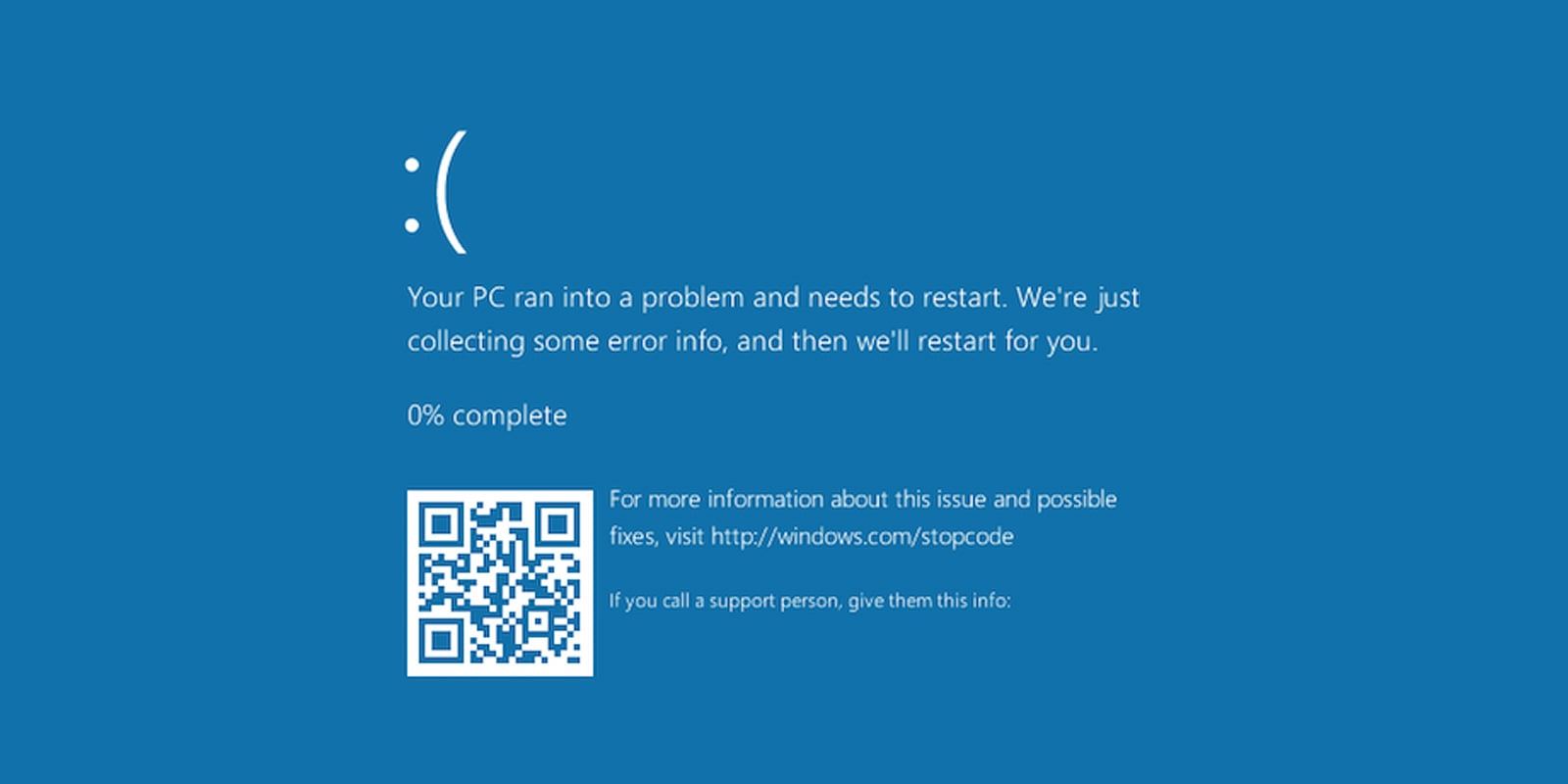
The landscape of cyber threats continuously evolves, with adversaries refining their methods to exploit human psychology alongside technical vulnerabilities. One such insidious tactic is "ClickFix" social engineering, a strategy that hinges on creating a sense of urgency or technical distress to prompt users into taking self-destructive actions. In this particular manifestation, threat actors deploy web pages designed to mimic critical system failures, such as the infamous Windows Blue Screen of Death (BSOD), a diagnostic display indicating a fatal operating system error. Unlike genuine BSODs, which typically offer no user interaction beyond a reboot, these fraudulent screens present seemingly helpful, yet entirely malicious, "fixes" that instruct users to manually input and execute harmful commands.
The Modus Operandi of ClickFix Social Engineering
ClickFix attacks are fundamentally rooted in deception, presenting a fabricated problem alongside an immediate, seemingly simple solution. These deceptive online interfaces can manifest in various forms: spurious error messages, counterfeit security warnings, deceptive CAPTCHA challenges, or even bogus software update prompts. The common thread is their design to induce panic or a desire for quick resolution, leading unsuspecting users to follow attacker-provided instructions. Victims, often lacking deep technical expertise or operating under pressure, are thus tricked into executing harmful commands—typically PowerShell or shell scripts—on their own machines, effectively becoming unwitting accomplices in their own compromise. This self-inflicted infection bypasses many automated security layers, making it a particularly potent vector.
The PHALT#BLYX Campaign: A Detailed Examination
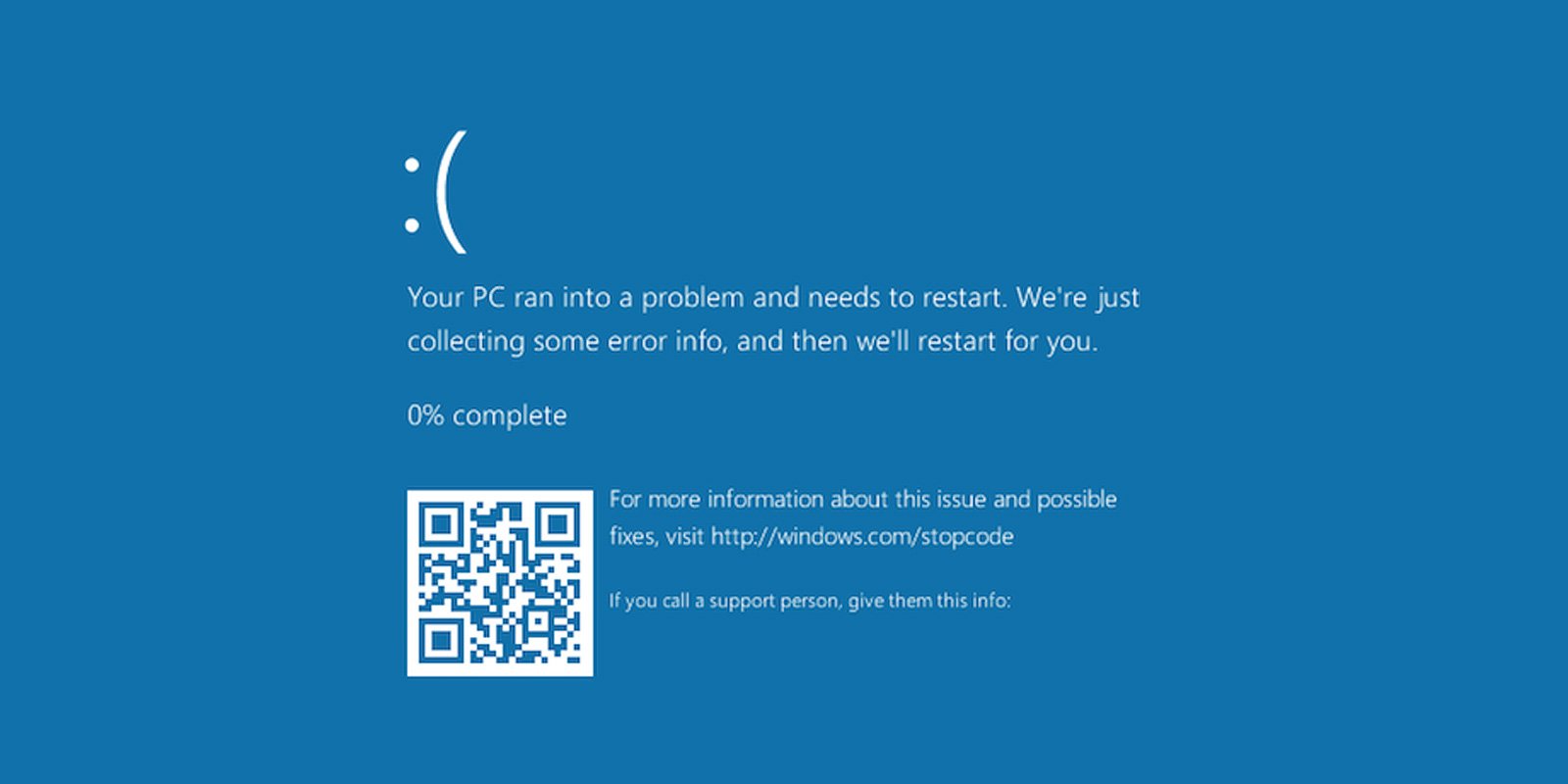
A recent campaign, designated "PHALT#BLYX" by security analysts, exemplifies the sophisticated nature of these ClickFix operations. First detected in December, this particular iteration began with highly targeted phishing emails. These messages meticulously impersonated legitimate communications from Booking.com, a prominent online travel agency, and were specifically directed at entities within the European hospitality industry. The emails typically claimed a significant refund amount related to a canceled hotel reservation, a tactic carefully chosen to generate a strong sense of urgency and compel immediate action from the recipient, often a hotel staff member responsible for bookings or financial transactions. The substantial monetary value attached to the "refund" serves as a powerful psychological trigger, overriding caution and encouraging swift engagement with the provided link.
Upon clicking the embedded link, victims are redirected to a fraudulent website. Cybersecurity researchers have characterized this site, hosted on a domain such as ‘low-house[.]com,’ as a "high-fidelity clone" of the authentic Booking.com portal. The meticulous replication extends to every visual detail: official branding, precise color palettes, corporate logos, and font styles are all faithfully reproduced. To an untrained eye, or indeed, to any user not actively scrutinizing the URL and security certificates, the counterfeit site appears indistinguishable from its legitimate counterpart. This level of graphical authenticity is crucial for maintaining the illusion and sustaining the victim’s trust through the initial stages of the attack.
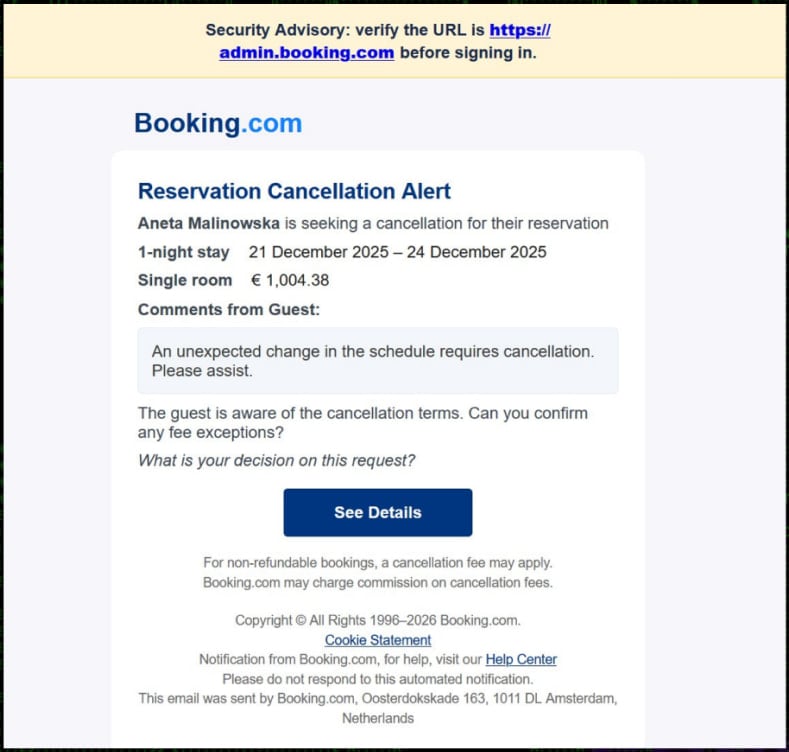
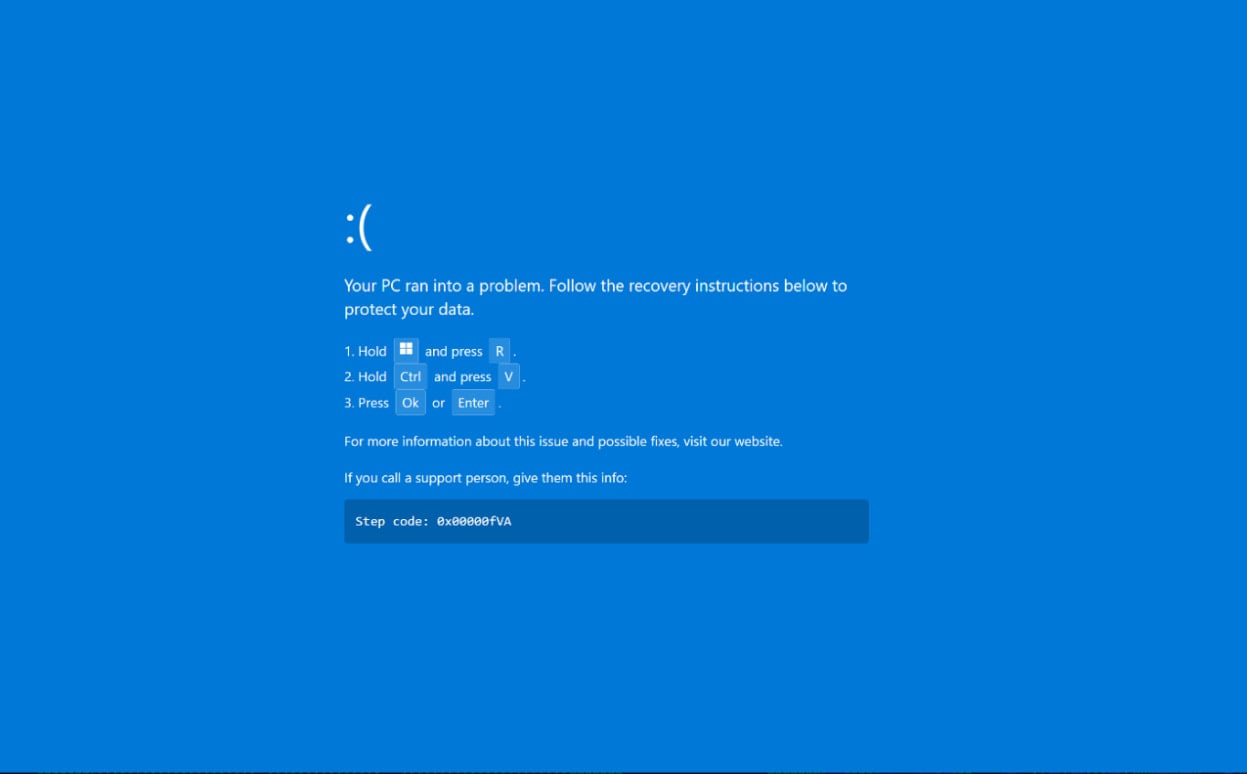
Once on the cloned site, malicious JavaScript embedded within the page orchestrates the next phase of the deception. Initially, a benign-looking "Loading is taking too long" error message is displayed, accompanied by a button prompting the user to "refresh the page." This serves as an initial test of the victim’s willingness to interact with the deceptive interface. However, the seemingly innocuous "refresh" button triggers a more aggressive maneuver: the browser enters full-screen mode, and the entire display is replaced by a convincing, yet entirely fake, Windows BSOD crash screen. This simulated system failure marks the core of the ClickFix social engineering attack.

The Deceptive BSOD and Malware Deployment
The fake BSOD screen is engineered to replicate the visual aesthetics of a genuine Windows crash, but with a critical difference: it provides interactive "recovery" instructions. The screen directs the user to open the Windows Run dialog box and then to press ‘CTRL+V’. This action pastes a pre-copied malicious command, which the attackers have surreptitiously loaded onto the user’s clipboard through the malicious JavaScript. Following this, the user is instructed to press the ‘OK’ button or ‘Enter’ on their keyboard, thereby executing the command. This crucial step represents the moment of self-inflicted infection.
It is imperative to distinguish this deceptive interaction from a true BSOD. Authentic Windows crash screens are diagnostic in nature, displaying an error code and a notification about system reboot, but they never offer interactive recovery instructions or prompt users to execute commands. However, the contextual pressure on hospitality staff, combined with a potential lack of deep technical understanding regarding system crashes, makes them particularly vulnerable to overlooking these critical discrepancies. The urgency instilled by the initial phishing email’s financial claim further compounds this vulnerability, creating an environment where quick, seemingly logical actions are prioritized over careful scrutiny.
The execution of the provided command initiates a complex multi-stage payload delivery. A PowerShell command is invoked, which serves a dual purpose. Ostensibly, it opens a decoy Booking.com administration page, maintaining the illusion of a legitimate transaction resolution. Concurrently, in the background, this script surreptitiously downloads a malicious .NET project file (identified as ‘v.proj’). Crucially, the PowerShell script then leverages a legitimate Windows component, ‘MSBuild.exe’ (Microsoft Build Engine), to compile and execute this downloaded project. The use of ‘MSBuild.exe’ is a classic "living off the land" (LOTL) technique, where attackers utilize pre-existing, trusted system tools to perform malicious actions, thereby evading detection by traditional security solutions that might flag unknown executables.
Once compiled and executed, the primary malware payload, identified as DCRAT (DarkCrystal Remote Access Trojan), begins its operations. The initial actions of the malware include adding exclusions to Windows Defender, a common tactic to prevent detection and removal. It then triggers User Account Control (UAC) prompts, attempting to gain elevated administrative privileges on the compromised system. To ensure persistence, the malware downloads its main loader using the Background Intelligent Transfer Service (BITS), another legitimate Windows component often abused by threat actors for covert data transfer. Finally, it establishes a persistent presence by dropping a .url file into the Windows Startup folder, ensuring that the malware executes every time the system boots.
The DCRAT Payload and its Capabilities
DCRAT is a potent remote access Trojan known for its comprehensive capabilities. For stealth, the malware (staxs.exe) is injected into a legitimate Windows process, ‘aspnet_compiler.exe,’ using a technique known as process hollowing, where the code of a legitimate process is replaced with malicious code while maintaining its original identity. This allows the malware to execute directly in memory, making it harder for endpoint security solutions to detect its presence.
Upon establishing its initial connection with a command-and-control (C2) server, the malware transmits a detailed system fingerprint, providing the attackers with comprehensive information about the compromised device. Following this initial reconnaissance, DCRAT awaits further instructions from the C2 server. Its feature set is extensive, including remote desktop functionality for full graphical access, keylogging capabilities to capture sensitive user input, the ability to open a reverse shell for direct command-line control, and the capacity for in-memory execution of additional payloads. In the specific instance observed by researchers, the attackers deployed a cryptocurrency miner, leveraging the compromised system’s resources for illicit coin generation. However, with the established remote access, the threat actors possess a significant foothold on the target’s network, enabling them to pursue further objectives such as lateral movement to other devices, data exfiltration, and potentially the compromise of broader organizational systems.
Broader Implications and Risk Analysis
The PHALT#BLYX campaign highlights several critical facets of the contemporary cyber threat landscape. The deliberate targeting of the hospitality sector is strategic. This industry is characterized by high transaction volumes, a diverse workforce with varying technical proficiencies, a heavy reliance on online booking platforms, and the handling of sensitive customer financial and personal data. Staff, particularly those in customer-facing or reservation roles, are frequently under pressure to resolve disputes or address customer queries promptly, making them more susceptible to social engineering tactics that exploit urgency and perceived authority.
The effectiveness of the fake BSOD and urgent phishing emails underscores the enduring power of social engineering. Stress, a lack of specialized technical knowledge, ingrained trust in established brands, and the fear of financial loss or reputational damage are all powerful psychological levers that attackers skillfully manipulate. When presented with a seemingly critical system error and a straightforward "fix" from a seemingly legitimate source, individuals are prone to bypass their inherent skepticism.
Furthermore, the utilization of legitimate system tools like MSBuild.exe and BITS for compilation and data transfer represents a sophisticated "living off the land" (LOTL) approach. This technique is highly effective at evading signature-based detection mechanisms, as the malicious actions are performed by trusted executables. It forces defensive strategies to evolve towards behavioral analysis and anomaly detection, which are inherently more complex to implement and maintain.
The compromise of a hospitality entity carries significant downstream risks. Beyond the direct financial impact of a cryptocurrency miner or data theft, there is the potential for supply chain implications. A compromised hotel system could inadvertently become a vector for attacks against guests, payment processors, or other partners in the travel ecosystem, leading to a cascading effect of security incidents. This campaign serves as a stark reminder of the evolving nature of cyber threats and the continuous need for vigilance.
Mitigation Strategies and Defensive Measures
Addressing sophisticated campaigns like PHALT#BLYX requires a multi-layered and proactive security posture.
- Comprehensive Employee Training: Continuous, targeted cybersecurity awareness training is paramount. All staff, especially those in roles handling reservations, customer service, or finance, must be educated on identifying sophisticated phishing attempts. This includes scrutinizing email sender details, carefully inspecting URLs for anomalies (even on high-fidelity clones), and understanding the legitimate behavior of operating system warnings versus deceptive ones. Training should emphasize that genuine BSODs do not prompt user interaction for recovery.
- Robust Email Security: Implementing advanced email filtering solutions that leverage DMARC, SPF, and DKIM authentication protocols can help detect and block spoofed emails. Gateway security should also incorporate sandboxing and URL rewriting to neutralize malicious links before they reach end-users.
- Endpoint Detection and Response (EDR): EDR solutions are critical for detecting and responding to post-compromise activities. These systems can identify anomalous process behavior, such as MSBuild.exe compiling unfamiliar projects or aspnet_compiler.exe exhibiting unusual network activity, even if the initial malware execution bypasses traditional antivirus.
- Application Control and Whitelisting: Implementing strict application whitelisting policies can prevent the execution of unauthorized programs. While challenging to manage, this can significantly limit the ability of attackers to run malicious scripts or compile unapproved projects using legitimate tools.
- Behavioral Monitoring: Network and endpoint behavioral monitoring systems can detect deviations from normal operational patterns. Unusual network connections to command-and-control servers, bulk data transfers, or the unexpected initiation of cryptocurrency mining processes can trigger alerts.
- Multi-Factor Authentication (MFA): Implementing MFA across all critical systems and accounts significantly reduces the impact of credential theft, even if an attacker manages to capture usernames and passwords through keylogging or other means.
- Regular Security Audits and Penetration Testing: Proactive security assessments can identify weaknesses in an organization’s defenses before attackers exploit them. This includes testing the efficacy of employee awareness training through simulated phishing campaigns.
- Incident Response Planning: A well-defined and regularly practiced incident response plan is crucial for minimizing the impact of a successful attack. This plan should cover detection, containment, eradication, recovery, and post-incident analysis.
- Threat Intelligence Sharing: Active participation in threat intelligence sharing initiatives within the hospitality sector can provide organizations with early warnings about emerging threats and specific attack indicators, enabling proactive defensive measures.
In conclusion, the PHALT#BLYX campaign serves as a critical reminder that cyber adversaries are continuously innovating, blending technical sophistication with psychological manipulation to achieve their objectives. The use of highly convincing fake BSODs to trick users into self-executing malware represents a significant challenge for organizational security. Only through a combination of vigilant employee education, robust technical controls, and proactive incident preparedness can organizations effectively defend against such evolving and insidious threats.







