A prominent collective of cyber threat actors, identifying themselves as "Scattered Lapsus$ Hunters," has publicly asserted a significant compromise of the cybersecurity entity Resecurity, purporting to have exfiltrated extensive internal data. Resecurity, however, unequivocally refutes these allegations, contending that the alleged breach was merely an interaction with a meticulously designed honeypot, purposefully deployed to surveil and gather intelligence on the perpetrators. This incident highlights the increasingly complex cat-and-mouse game between sophisticated cyber attackers and advanced defensive strategies employed by cybersecurity firms.
The Allegations from "Scattered Lapsus$ Hunters"
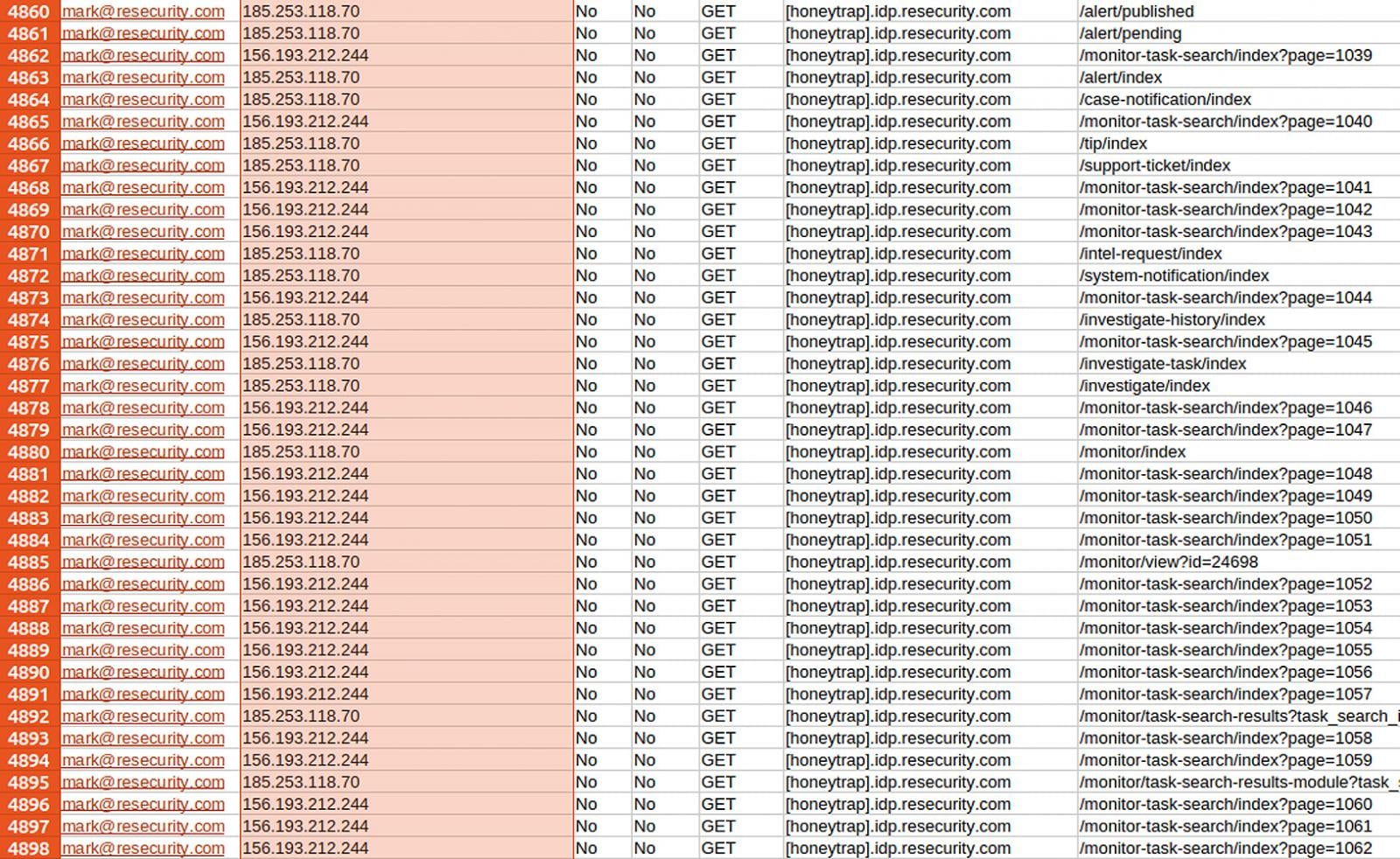
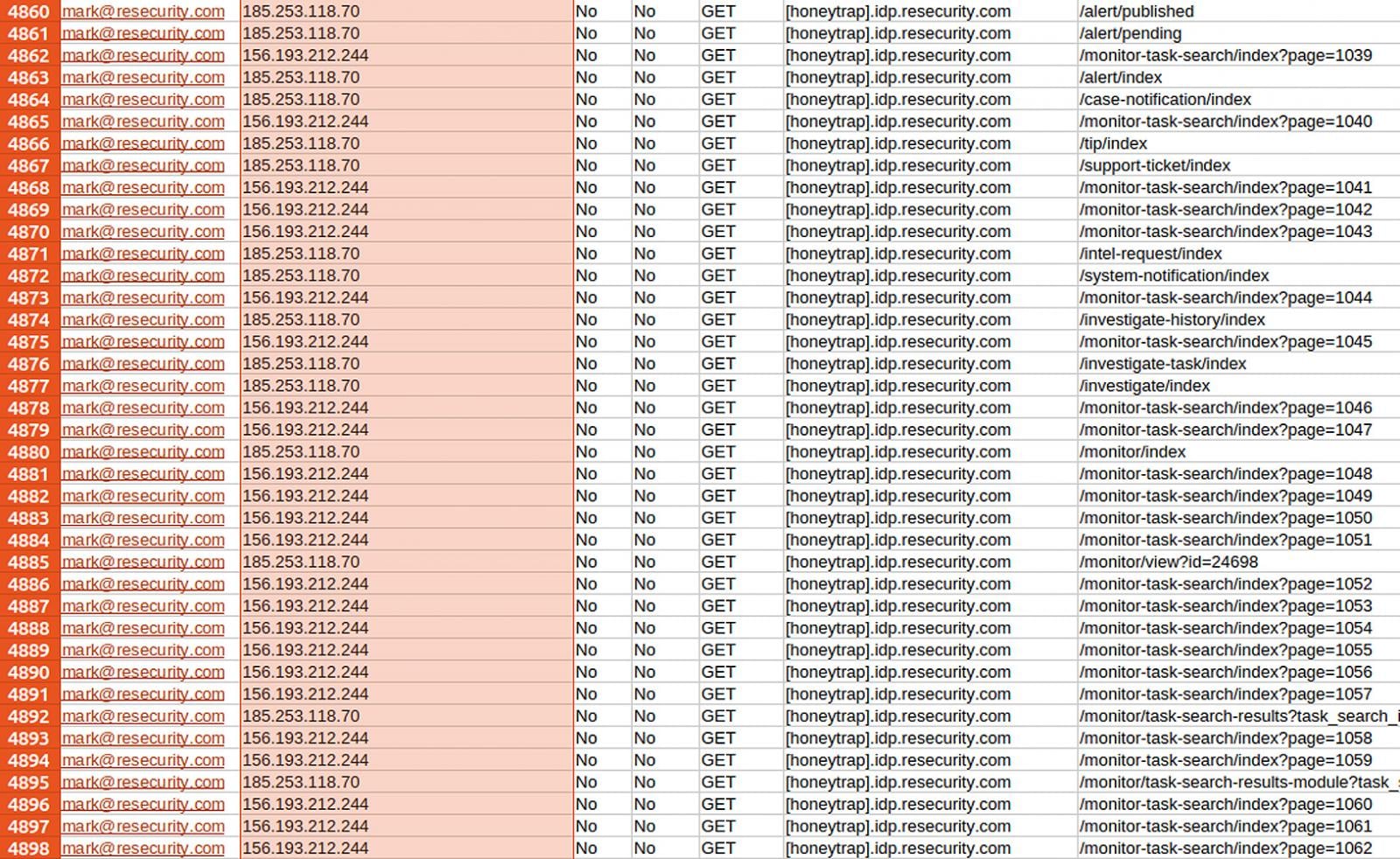
On a recent date, a group self-identifying as "Scattered Lapsus$ Hunters" (SLH) disseminated claims across various online channels, including Telegram, detailing what they described as a comprehensive infiltration of Resecurity’s operational infrastructure. The group presented screenshots as ostensible evidence of their access, purporting to demonstrate control over internal communication platforms, exfiltrated employee dossiers, proprietary threat intelligence reports, and detailed client lists. Their public statements declared "full access to REsecurity systems," asserting the theft of "all internal chats and logs," "full employee data," "threat intel related reports," and a "complete client list with details."
The moniker "Scattered Lapsus$ Hunters" is indicative of alleged affiliations with, or inspiration drawn from, several notorious cybercriminal entities, including ShinyHunters, Lapsus$, and the financially motivated Scattered Spider group. These groups are known for their varied tactics, ranging from data exfiltration and extortion to highly effective social engineering campaigns. The attackers specifically cited an image depicting what appeared to be a Mattermost collaboration instance, showcasing dialogues between Resecurity personnel and representatives from Pastebin concerning the removal of malicious content. This purported evidence aimed to lend credibility to their claims of deep internal access.
The motivation behind this alleged attack, according to SLH, was retaliatory. They asserted that Resecurity employees had engaged in persistent social engineering attempts, masquerading as prospective buyers during the sale of a purported Vietnamese financial system database. The threat actors claimed these individuals sought free data samples and additional proprietary information, prompting their alleged retaliatory strike against the cybersecurity firm. This narrative introduces an element of digital counter-espionage, suggesting a prior engagement between the two parties that escalated into the current public dispute. It is worth noting that a spokesperson associated with ShinyHunters subsequently disavowed any involvement in this specific activity, despite the SLH group’s broader claim of overlap with ShinyHunters.

Resecurity’s Counter-Narrative: The Honeypot Strategy
In stark contrast to the attackers’ assertions, Resecurity has presented a detailed counter-narrative, positing that the alleged breach was, in fact, a carefully orchestrated cyber deception operation. The firm maintains that the systems accessed by SLH were not part of its legitimate production environment but rather an elaborate honeypot specifically engineered to attract, monitor, and gather intelligence on threat actors.
Following inquiries regarding the breach claims, Resecurity directed attention to a previously published report dated December 24, outlining their proactive defense strategy. According to this report, Resecurity’s Digital Forensics and Incident Response (DFIR) team first detected suspicious reconnaissance activities targeting their publicly exposed systems as early as November 21. Early indicators allowed the firm to log multiple suspicious IP addresses, tracing origins to regions such as Egypt and identifying the use of privacy-enhancing services like Mullvad VPN.
Responding to these initial probes, Resecurity initiated an active defense maneuver: the deployment of a "honeypot" account within an isolated, controlled environment. This setup was designed to appear authentic, allowing the threat actors to log in and interact with systems containing meticulously crafted, fake datasets. The objective was clear: observe and analyze the attackers’ tactics, techniques, and procedures (TTPs) without jeopardizing genuine corporate assets or sensitive client information.
The Sophistication of Cyber Deception

A honeypot represents a critical component of modern cyber defense, acting as a decoy system deliberately exposed to the internet. Its primary purpose is to lure and entrap attackers, enabling security professionals to study their methodologies, identify their tools, and collect intelligence on their operational infrastructure. Honeypots can range from low-interaction systems, which simulate basic services, to high-interaction environments, which offer a full operating system for attackers to explore, providing richer data on their post-exploitation behavior.
Resecurity’s strategy involved populating its honeypot with sophisticated synthetic datasets designed to mirror real-world business information convincingly. This included over 28,000 synthetic consumer records and more than 190,000 synthetic payment transaction records, all generated using formats consistent with Stripe’s official API. The use of synthetic data is crucial; it not only enhances the believability of the decoy environment but also allows defenders to observe precisely what types of data attackers prioritize and attempt to exfiltrate, providing invaluable insights into their objectives. Had the honeypot contained only empty files, an astute attacker might quickly identify it as a trap. The presence of seemingly legitimate, voluminous data makes the deception far more effective.
The firm detailed that the threat actors initiated attempts to automate data exfiltration in December, generating in excess of 188,000 requests between December 12 and December 24. This automated activity, often facilitated through large numbers of residential proxy IP addresses, provided Resecurity with a rich stream of telemetry. During this period, the firm meticulously collected data on the attacker’s TTPs and their underlying infrastructure.
Operational Security Failures and Law Enforcement Collaboration
A key outcome of Resecurity’s monitoring was the identification of several operational security (OPSEC) failures on the part of the attackers. Due to intermittent proxy connection failures, the threat actors’ true IP addresses were briefly exposed on multiple occasions. Such lapses are invaluable for intelligence gathering, allowing defenders to pinpoint the attacker’s origin or infrastructure more accurately. Resecurity reported this critical intelligence to law enforcement agencies.
Further observation of the attackers’ behavior led Resecurity to introduce additional fake datasets into the honeypot, a tactic designed to elicit further interaction and expose more of the attackers’ methods. This iterative process resulted in more OPSEC failures, further narrowing down the potential infrastructure used by the threat actors. Resecurity subsequently identified servers employed to automate the attack via residential proxies and shared this refined intelligence with law enforcement. The firm explicitly stated, "Once the actor was located using available network intelligence and timestamps, a foreign law enforcement organization, a partner of Resecurity, issued a subpoena request regarding the threat actor." This indicates a tangible progression from digital defense to potential legal repercussions for the cybercriminals.
Implications and Future Outlook
This incident underscores several critical aspects of contemporary cybersecurity. Firstly, it highlights the escalating sophistication of defensive strategies, where active deception, rather than mere perimeter defense, is becoming a viable and effective tactic. Honeypots, particularly those employing synthetic data, offer a proactive means to gather threat intelligence, understand attacker methodologies, and even contribute to attribution efforts.
Secondly, the public dispute itself becomes a form of psychological warfare. For the "Scattered Lapsus$ Hunters," claiming a breach of a cybersecurity firm could bolster their reputation among the cybercriminal underworld and potentially attract new affiliates or customers for stolen data. Conversely, Resecurity’s counter-narrative, if fully substantiated, would significantly damage the attackers’ credibility and validate the effectiveness of advanced defensive measures. The veracity of each claim remains subject to independent verification, a challenge inherent in these high-stakes digital confrontations.
Thirdly, the collaboration with law enforcement signifies a critical pathway for translating cyber intelligence into real-world action. The ability to track, identify, and attribute attackers, even through transient OPSEC failures, strengthens the deterrent against cybercrime. This partnership is crucial for closing the loop from detection and analysis to investigation and prosecution.
As of the latest updates, the threat actors have not provided further definitive evidence to counter Resecurity’s honeypot claim, merely issuing a subsequent Telegram post stating, "Nice damage control Resecurity. More information coming soon!" This suggests an ongoing digital skirmish, with both sides likely preparing their next moves in this intricate game of cyber chess. The incident serves as a powerful reminder of the dynamic and evolving landscape of cyber warfare, where deception, intelligence gathering, and attribution are increasingly central to both offensive and defensive operations. Organizations are continually seeking to move beyond reactive security postures, embracing proactive strategies like honeypots to turn the tables on their adversaries, transforming potential breaches into invaluable intelligence-gathering opportunities.







