
A sophisticated cyberattack is reportedly behind the alleged compromise of a vast database linked to WIRED magazine, exposing more than 2.3 million subscriber entries, according to claims from a malicious actor who has also issued a stark warning of impending data releases affecting numerous other Condé Nast publications, potentially impacting tens of millions more individuals. This incident underscores the persistent and evolving threats faced by media conglomerates in safeguarding sensitive user information and highlights critical questions regarding corporate cybersecurity posture and vulnerability response mechanisms.
The purported breach, publicly revealed on December 20 by an individual operating under the alias "Lovely" on prominent dark web forums, involves a dataset containing subscriber information for WIRED. The threat actor not only disseminated the alleged WIRED data but simultaneously announced intentions to progressively disclose an additional 40 million records associated with other high-profile Condé Nast brands in the coming weeks. This aggressive posture, coupled with the sheer volume of data involved, signals a significant potential crisis for one of the world’s leading publishing houses.
The leaked WIRED database, which has been analyzed by independent security researchers, reportedly comprises 2,366,576 records, encompassing 2,366,574 unique email addresses. The timestamps associated with these entries span a remarkably broad period, from April 26, 1996, extending curiously into the future until September 9, 2025. This latter date might indicate subscription expiration dates, system-generated placeholders, or other internal data management artifacts, rather than actual future account activity. Initial verification efforts have corroborated the authenticity of a sample of these records, lending credence to the hacker’s assertions.

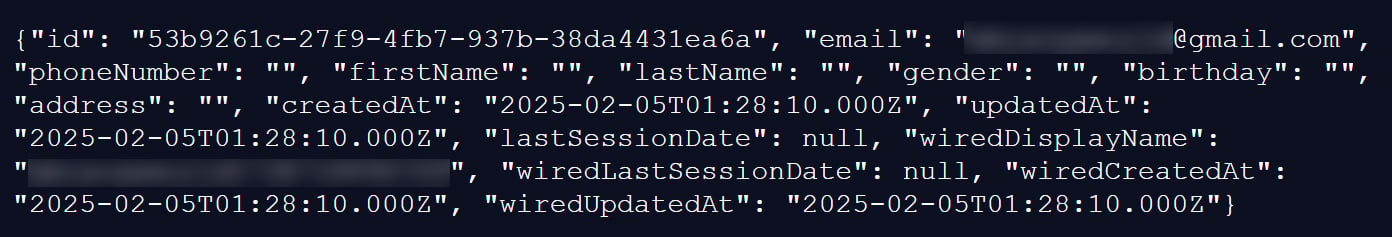
Each record within the exposed dataset typically includes a unique internal subscriber identifier, an email address, and often, various optional personal details. While a substantial portion of these optional fields remain blank, a significant subset contains more granular information. Approximately 12.01% of the records, equating to 284,196 entries, include both a first and last name. Physical addresses are present in 8.21% of records (194,361 entries), while birthdays appear in 2.84% (67,223 records), and phone numbers in 1.37% (32,438 records). A smaller, yet critically vulnerable, group of 1,529 records (0.06%) contains a comprehensive profile, featuring full name, birth date, phone number, physical address, and gender. Beyond these personal identifiers, the records also capture technical data such as account creation and update timestamps, last session information, a display username, and WIRED-specific account activity dates, providing a detailed digital footprint for affected individuals.
The threat actor’s public statements accuse Condé Nast of profound negligence regarding user data security. "Lovely" claims that the publishing giant repeatedly ignored vulnerability reports and exhibited a lack of commitment to addressing security flaws. The hacker alleged that it took an entire month of persistent communication to prompt the company to rectify identified vulnerabilities on its websites, a period during which, according to the threat actor, their patience wore thin, ultimately leading to the decision to leak the data. This narrative, if accurate, paints a concerning picture of an organization potentially struggling with its cybersecurity response protocols or its engagement with external security researchers.
The dissemination of the compromised data occurred across various underground hacking forums, where access was monetized through the sites’ internal credit systems. The initial offering price for the WIRED database was approximately $2.30 in forum credits, a relatively low sum that suggests a primary motivation beyond direct financial gain from this specific dataset, perhaps aiming for reputational damage or to leverage a broader extortion attempt. The public warning of subsequent leaks targeting other Condé Nast properties, including The New Yorker, Epicurious, SELF, Vogue, Allure, Vanity Fair, Glamour, Men’s Journal, Architectural Digest, Golf Digest, Teen Vogue, Style.com, and Condé Nast Traveler, amplifies the potential scope of this incident from a localized breach to a systemic vulnerability affecting the entire corporate digital infrastructure.

Independent validation of the leaked data has been swift. Beyond initial checks confirming sample records, experts from Hudson Rock, a cybersecurity intelligence firm, verified the dataset’s authenticity by cross-referencing it with credentials previously compromised through infostealer malware logs. This method, which compares leaked records against a vast repository of confirmed compromised credentials, provides a robust confirmation of the data’s legitimacy without direct interaction with the victim organization. Consequently, the exposed data has been integrated into "Have I Been Pwned," a widely recognized platform enabling individuals to ascertain if their email addresses have been compromised in data breaches, empowering affected users to take proactive security measures.
A notable dimension of this incident involves the threat actor’s initial interaction with DataBreaches.net, a reputable platform specializing in data breach reporting and responsible disclosure. "Lovely" reportedly contacted Dissent Doe of DataBreaches.net in late November, presenting as a security researcher seeking assistance in responsibly disclosing vulnerabilities to Condé Nast. The individual initially claimed to have downloaded only a minimal number of records for proof, including those belonging to DataBreaches.net and a WIRED employee. This overture aligns with standard responsible disclosure practices, where security researchers identify flaws and report them to organizations before publicizing them, allowing time for remediation.
However, the narrative quickly shifted. After an alleged lack of response from Condé Nast, "Lovely" informed Dissent Doe that the entire database had been exfiltrated, and a public leak was imminent. This turn of events led DataBreaches.net to conclude that they had been deliberately misled and exploited by a malicious actor who masqueraded as a white-hat researcher to further their own agenda. Dissent Doe publicly expressed regret for being "played" and cautioned against trusting "Lovely" or engaging in any financial transactions with them, underscoring the ethical complexities and potential for deception inherent in interactions with anonymous threat actors.
The implications of such a widespread data exposure are multifaceted, impacting both individuals and the corporate entity. For affected subscribers, the primary risks include heightened susceptibility to phishing, spear-phishing, and social engineering attacks. Threat actors can leverage exposed email addresses, names, and publication affiliations to craft highly convincing fraudulent communications, increasing the likelihood of victims divulging further sensitive information or falling prey to malware. For those with more complete profiles, the risk escalates to potential identity theft, financial fraud, and targeted harassment. The mere inclusion of an email address in a breached database also contributes to the proliferation of spam and unwanted solicitations.
For Condé Nast, the ramifications extend beyond the immediate operational challenge of addressing a security incident. The reputational damage to WIRED and its sister publications, brands built on trust and journalistic integrity, could be substantial. Such a breach can erode reader confidence, potentially leading to subscriber churn and adverse impacts on advertising revenue. Furthermore, the company faces potential legal liabilities, including class-action lawsuits from affected individuals, and significant regulatory fines under data protection frameworks such as GDPR (General Data Protection Regulation) or CCPA (California Consumer Privacy Act), depending on the residency of the affected individuals and the nature of the data involved. The ongoing silence from Condé Nast regarding the alleged breach adds to the uncertainty, potentially exacerbating public concern and regulatory scrutiny.
This incident is not isolated but rather indicative of a broader trend within the media and publishing sector, where vast repositories of subscriber data become attractive targets for cybercriminals. Media companies, increasingly reliant on digital platforms for content delivery and audience engagement, often manage complex IT infrastructures with numerous third-party integrations, each representing a potential vulnerability point. The value of subscriber data—for targeted advertising, market intelligence, or direct malicious exploitation—continues to drive these attacks. Organizations must prioritize robust web application security, comprehensive vulnerability management programs, and stringent access controls to protect these critical assets.
As of the current reporting, Condé Nast has not issued a public statement acknowledging or denying the alleged breach, nor has it responded to inquiries regarding the incident. This lack of immediate confirmation, while common in the early stages of a suspected breach as organizations conduct internal investigations, can contribute to public anxiety and fuel speculation. Best practices in incident response emphasize transparent communication, though balancing this with the need for accurate information and legal considerations remains a complex challenge for affected entities.
Looking ahead, this event serves as a critical reminder for both consumers and organizations. Individuals whose data may have been compromised are strongly advised to change passwords for their WIRED and other Condé Nast accounts, enable multi-factor authentication wherever possible, and remain highly vigilant against suspicious emails, messages, or phone calls. Monitoring credit reports and financial statements for unusual activity is also a prudent step. For Condé Nast and other media enterprises, the imperative is clear: invest proactively in advanced cybersecurity defenses, cultivate a culture of security awareness across the organization, establish clear and efficient vulnerability disclosure programs, and develop robust, transparent incident response plans to mitigate the impact of inevitable future cyber threats. The digital landscape demands continuous vigilance and adaptation to protect the integrity of data and the trust of millions of users.







