
A recently identified cyberattack campaign demonstrates a significant escalation in evasion tactics, intricately combining social engineering with the exploitation of legitimate Windows enterprise features. This multi-stage offensive, dubbed an evolution of the "ClickFix" methodology, employs deceptive CAPTCHA challenges to manipulate users into executing a command that, through a signed Microsoft Application Virtualization (App-V) script, discreetly injects the Amatera information-stealing malware into target systems. The innovative use of a trusted Microsoft component as a proxy for malicious PowerShell execution underscores a growing trend among threat actors to "live off the land" (LOTL), leveraging native system tools to mask their activities and circumvent conventional security defenses.
The intricacies of this campaign reveal a meticulously planned operation designed for stealth and persistence. Microsoft Application Virtualization (App-V) is a robust enterprise feature integral to modern Windows environments, enabling organizations to deploy applications in isolated virtual environments. This virtualization minimizes conflicts, streamlines software management, and ensures application integrity without requiring full installation on the host system. Ironically, the very trust and utility inherent in such enterprise solutions are being weaponized by adversaries. While prior instances of App-V script abuse for antivirus evasion have been documented, this marks the inaugural observation of its integration within a ClickFix attack chain to deliver an information stealer, signaling a dangerous pivot in attack methodology.
The initial vector of this sophisticated attack capitalizes on human psychology and user trust. The campaign commences with a fraudulent CAPTCHA verification page, a seemingly innocuous security measure designed to differentiate human users from automated bots. However, in this malicious iteration, the fake CAPTCHA serves as a social engineering lure. Victims are prompted with instructions to manually copy and paste a specific command into the Windows Run dialog box and execute it. This seemingly simple action, often perceived as a benign step to "verify" access, becomes the critical entry point for the entire infection chain. The "ClickFix" moniker itself highlights this reliance on user interaction, where a user’s manual action directly facilitates the compromise. This initial stage bypasses many automated defenses that look for drive-by downloads or malicious attachments, as the user is actively participating in the initial payload execution.

The command that victims are tricked into executing is not a standalone malicious script but rather an abuse of the legitimate SyncAppvPublishingServer.vbs App-V script. This script is a standard component within the App-V framework, typically responsible for publishing and managing virtualized enterprise applications across a network. By invoking this legitimate script, attackers leverage a signed Microsoft component, lending an air of legitimacy to the subsequent actions. The script is executed via wscript.exe, another trusted Windows binary, which then proxies the execution of PowerShell. This layering of legitimate processes to hide malicious activity is a hallmark of sophisticated LOTL attacks, making detection challenging for security solutions that primarily focus on identifying known malicious executables or anomalous process creations. The use of signed binaries further complicates matters, as these are inherently trusted by the operating system and many security products.
A critical aspect of this initial stage involves advanced anti-analysis techniques. Before proceeding with the full infection, the malware loader performs a series of checks to ascertain whether it is operating within a genuine user environment or a sandbox analysis machine. These checks include verifying that the user manually executed the command, confirming the expected execution order, and ensuring the clipboard contents remain unaltered. Such measures are designed to detect automated analysis environments, which often simulate user interaction or clear clipboard data. If an analysis environment is detected, the execution chain is silently stalled, typically through infinite loops or extended waits. This tactic not only prevents security researchers from quickly obtaining the final payload but also wastes valuable automated analysis resources, allowing the threat actors to preserve their methods and infrastructure for longer. This level of sophistication highlights the attackers’ intent to evade detection and maintain a low profile, reserving their full capabilities for actual targets.
Upon successful evasion of analysis environments, the malware proceeds to retrieve configuration data from an unconventional source: a publicly accessible Google Calendar file. This file contains base64-encoded configuration values embedded within a specific event entry. The use of public, legitimate services for command-and-control (C2) or configuration retrieval is an increasingly common tactic among advanced persistent threats (APTs) and sophisticated cybercriminal groups. Such methods allow attackers to blend their malicious network traffic with legitimate internet traffic, making it exceedingly difficult for network defenders to distinguish between benign and malicious communications. Furthermore, these services are rarely blocked by corporate firewalls, providing a reliable and low-profile channel for attackers to communicate with their infected hosts.

In the subsequent stages of the attack, the infection chain further deepens its stealth. A 32-bit hidden PowerShell process is spawned through the Windows Management Instrumentation (WMI) framework. WMI is a powerful component for managing Windows systems, offering extensive capabilities for querying system information and performing administrative tasks. Its legitimate nature makes its abuse particularly effective, as WMI activity is often whitelisted or goes uninspected by security tools. Within this hidden PowerShell process, multiple embedded payloads are decrypted and loaded directly into memory, a technique that minimizes forensic artifacts on disk and makes detection by file-based antivirus solutions more challenging.
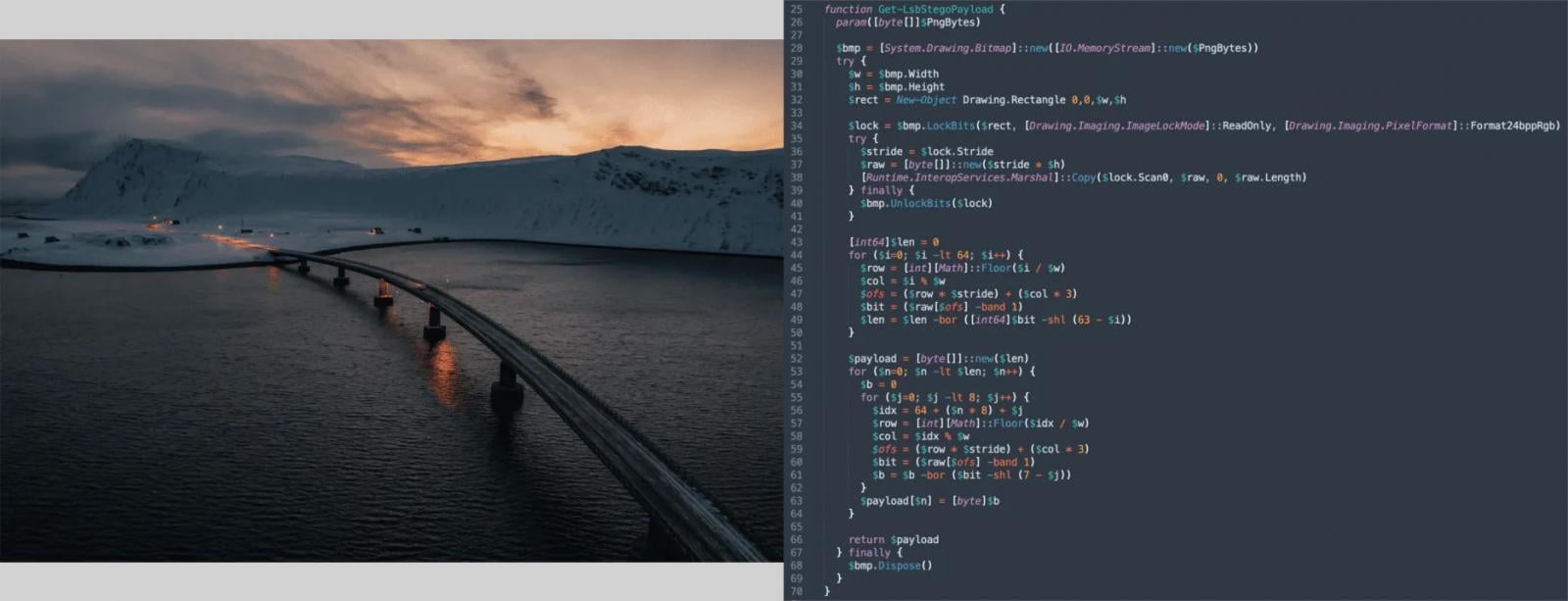
The method of payload delivery reaches a new level of sophistication through the employment of steganography. An encrypted PowerShell payload is cleverly embedded within seemingly innocuous PNG images, which are then hosted on public Content Delivery Networks (CDNs). The use of CDNs further enhances the resilience and global reach of the attack infrastructure, providing high availability for the malicious images. The payload data is extracted using Least Significant Bit (LSB) steganography, a technique where data is hidden in the least significant bits of the image’s pixel data, causing minimal or imperceptible changes to the image itself. Once extracted, the data undergoes a multi-step process of decryption, GZip decompression, and execution, all performed entirely in memory. This "fileless" approach, combined with steganography, represents a formidable challenge for traditional security tools, as there are no malicious files written to disk that can be easily scanned or quarantined.
The final stage of the PowerShell execution chain involves decrypting and launching native shellcode, which subsequently maps and executes the Amatera infostealer. Amatera, once active on the compromised host, establishes a connection to a hardcoded IP address. This connection serves as its primary command-and-control channel, allowing it to retrieve endpoint mappings and await additional binary payloads delivered via HTTP POST requests. The modular nature of Amatera, capable of receiving further instructions and payloads, indicates its adaptability and potential for evolving its malicious capabilities post-infection.
.jpg)
Analysis of Amatera malware classifies it as a standard information stealer, primarily designed to exfiltrate sensitive data. Its core capabilities include the collection of browser data, saved credentials, financial information, and potentially other confidential files from infected systems. Based on code overlaps and forensic analysis, Amatera is believed to be a rebranded and significantly enhanced version of the ACR infostealer. Proofpoint researchers have previously detailed its continuous development and increasing sophistication, signifying an active and dedicated threat actor group behind its evolution. The availability of Amatera as malware-as-a-service (MaaS) further underscores its professional development and widespread deployment potential, making it accessible to a broader range of cybercriminals. The operators of Amatera have historically deployed it using various ClickFix methods, demonstrating a consistent reliance on social engineering to achieve initial compromise.
The implications of this evolving threat landscape are profound for organizations of all sizes. The combination of social engineering, living-off-the-land techniques, sophisticated anti-analysis measures, and advanced payload obfuscation like steganography represents a significant challenge to conventional cybersecurity postures. To defend against such multifaceted attacks, a comprehensive and layered security strategy is imperative.
BlackPoint Cyber researchers, who initially uncovered this campaign, propose several critical mitigation strategies. Restricting access to the Windows Run dialog via Group Policy can significantly curtail the initial vector, preventing users from easily executing arbitrary commands. Removing App-V components when they are not explicitly needed within an environment reduces the attack surface by eliminating a potential LOTL binary. Enabling comprehensive PowerShell logging is crucial, as it provides forensic visibility into script execution, even when legitimate tools are being abused. Furthermore, vigilant monitoring of outbound network connections for discrepancies between the HTTP Host header or TLS Server Name Indication (SNI) and the actual destination IP address can help detect C2 communications disguised as legitimate traffic.
Beyond these specific recommendations, organizations should implement a broader set of cybersecurity best practices. Robust endpoint detection and response (EDR) solutions are vital for identifying anomalous process behavior and detecting in-memory attacks that bypass traditional antivirus. Application whitelisting can prevent unauthorized executables and scripts from running, even if they leverage legitimate binaries. Network segmentation limits the lateral movement of malware within an infected network, containing potential breaches. Regular user education and awareness training are paramount to combat social engineering tactics, empowering employees to recognize and report suspicious requests. Finally, integrating up-to-date threat intelligence into security operations can provide early warnings and indicators of compromise related to emerging threats like Amatera.
The continuous evolution of sophisticated cyberattacks, exemplified by this ClickFix campaign leveraging App-V scripts and steganography, underscores an ongoing arms race between threat actors and cybersecurity defenders. Attackers will undoubtedly continue to explore novel ways to abuse trusted system components, refine their social engineering tactics, and employ advanced obfuscation techniques to bypass security controls. Organizations must adopt a proactive, adaptive, and defense-in-depth approach, continuously reassessing their security posture, investing in advanced detection capabilities, and fostering a culture of cybersecurity awareness to effectively counter these escalating threats. The future outlook suggests a continued emphasis on "living off the land" and supply chain attacks, making vigilance and robust security architectures more critical than ever.







