
A novel Malware-as-a-Service (MaaS) offering, dubbed ‘Stanley,’ has surfaced within illicit cybercrime communities, promising threat actors the ability to bypass stringent security reviews and successfully publish malicious extensions to the Google Chrome Web Store. This development marks a concerning escalation in the ongoing battle against platform-based malware, as it democratizes access to sophisticated phishing capabilities, enabling even less technically proficient attackers to launch highly deceptive campaigns against a broad user base across multiple Chromium-based browsers.

The proliferation of Malware-as-a-Service platforms represents a significant shift in the cybercrime landscape, lowering the barrier to entry for individuals seeking to engage in illicit activities. These services provide pre-built tools, infrastructure, and often technical support, allowing customers to deploy sophisticated attacks without needing extensive technical expertise. In this context, ‘Stanley’ distinguishes itself by specifically targeting browser extensions, a vector increasingly exploited due to their privileged access to user browsing data, integration with web applications, and potential for extensive reach. Browser extensions, while offering immense utility and customization, also present a unique security challenge. They operate within the user’s browsing environment, capable of reading and modifying web content, intercepting network requests, and interacting with operating system features depending on their granted permissions. This inherent capability makes them an attractive target for malicious actors aiming to compromise user accounts, exfiltrate sensitive data, or inject advertising.
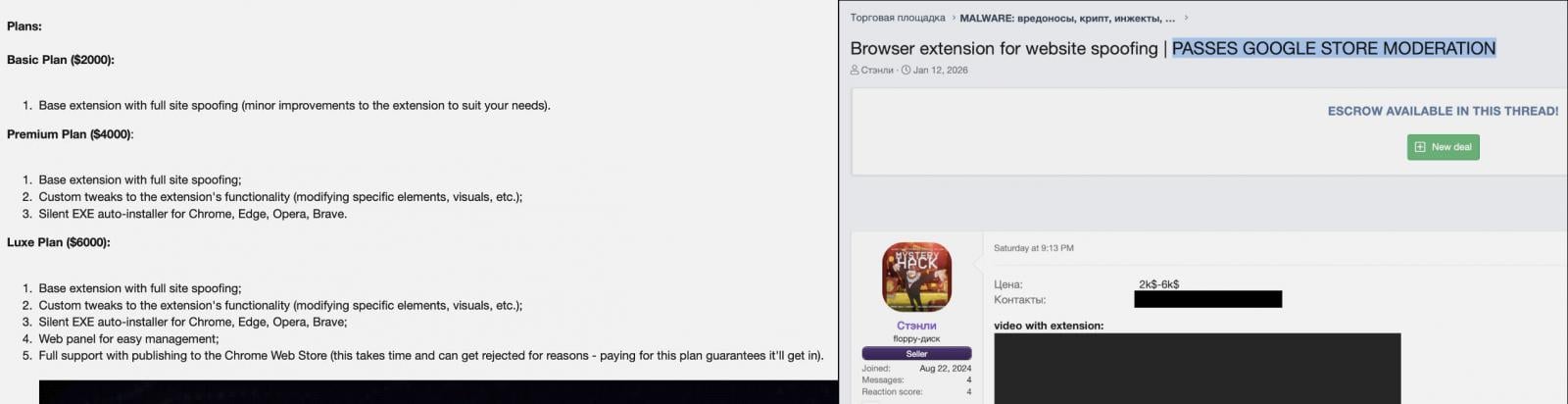
The ‘Stanley’ MaaS, named by researchers at Varonis after the alias of its primary developer, is advertised as a comprehensive solution for deploying phishing attacks through seemingly legitimate browser extensions. Its core modus operandi involves intercepting user navigation and dynamically overlaying legitimate webpages with a full-screen iframe containing attacker-controlled phishing content. Crucially, the browser’s address bar remains unchanged, continuing to display the legitimate domain, a technique designed to circumvent a primary indicator of phishing attempts for unsuspecting users. This subtle yet highly effective deception makes it exceptionally difficult for victims to discern the fraudulent nature of the displayed content, significantly increasing the likelihood of successful credential harvesting or other malicious interactions.

Beyond its primary phishing mechanism, ‘Stanley’ boasts a range of features designed to maximize the efficacy and persistence of its malicious operations. The service explicitly advertises silent auto-installation capabilities across leading Chromium-based browsers, including Google Chrome, Microsoft Edge, and Brave. This implies sophisticated distribution methods, potentially leveraging drive-by downloads, social engineering tactics, or even supply chain compromises, to install extensions without explicit user interaction or knowledge. Furthermore, the MaaS promises support for custom tweaks, indicating a degree of flexibility for operators to tailor their attacks to specific targets or exploit particular vulnerabilities. Such customization options enhance the adaptability of the malware, allowing threat actors to craft more convincing phishing lures or integrate with other malicious functionalities.
The commercialization model for ‘Stanley’ underscores the growing maturity of the cybercrime economy. It operates on a tiered subscription basis, with varying levels of access and functionality commensurate with the price point. The most premium offering, the "Luxe Plan," provides not only access to the malicious extension framework but also a dedicated web panel for command and control and, most critically, full support for publishing the malicious extension to the Chrome Web Store. This latter claim is particularly alarming, as it directly challenges the efficacy of Google’s review processes and suggests either a sophisticated method of evading detection or potentially exploiting systemic weaknesses within the platform’s vetting mechanisms. If true, it represents a direct threat to the integrity and trustworthiness of one of the world’s largest repositories of browser add-ons.
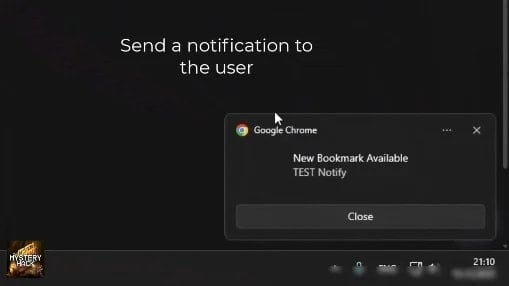
From a technical perspective, ‘Stanley’ employs a straightforward approach to implementing well-established attack techniques. Researchers note that while its code may appear "rough" in places, featuring elements such as Russian comments, empty catch blocks, and inconsistent error handling, its effectiveness lies in its distribution model rather than groundbreaking technical sophistication. The malicious extensions perform persistent command-and-control (C2) polling every ten seconds, ensuring continuous communication with the attacker’s infrastructure. This persistence is further bolstered by a backup domain rotation mechanism, designed to provide resilience against takedown attempts by rapidly switching to alternative C2 servers if the primary ones are compromised or blocked. Operators leveraging ‘Stanley’s’ control panel gain granular control over their campaigns, enabling them to activate or deactivate hijacking rules on demand, or even push custom notifications directly to victims’ browsers. These notifications can serve as an aggressive secondary lure, directing users to specific phishing pages or prompting immediate action, thereby intensifying the phishing process. Moreover, the service supports IP-based victim identification, facilitating geographic targeting and enabling operators to correlate activities across different sessions and devices, which can be invaluable for profiling targets and refining attack strategies.
The implications of a service like ‘Stanley’ are far-reaching, impacting users, platform providers, and the broader cybersecurity ecosystem. For users, the primary risk is a significant increase in successful phishing attacks. The deceptive nature of the iframe overlay, combined with the apparent legitimacy of the browser’s address bar, makes these attacks particularly dangerous. Victims are far more likely to input credentials, personal information, or financial details into what they perceive as a trusted website, leading to widespread account compromise, financial fraud, and identity theft. The silent auto-installation feature further exacerbates this risk, as users may be compromised without even realizing they have installed a malicious extension.
.jpg)
For Google and other browser vendors, ‘Stanley’ represents a direct challenge to the security and integrity of their extension ecosystems. The claim of guaranteed publication to the Chrome Web Store, if substantiated, underscores a critical vulnerability in their review processes. Maintaining user trust in official app stores is paramount, and any perception that malicious software can easily bypass security checks can erode that trust, leading users to become more hesitant about adopting useful extensions or, conversely, making them complacent about potential threats. This necessitates a continuous arms race, where platform providers must invest heavily in advanced automated and manual review processes, behavioral analysis, and threat intelligence sharing to identify and mitigate such threats rapidly. The detection of malicious extensions often relies on a combination of static code analysis, dynamic execution analysis, and user reporting. Services like ‘Stanley’ are designed to evade these layers, often by dynamically loading malicious payloads post-installation or by employing obfuscation techniques.
From the perspective of the cybersecurity industry, ‘Stanley’ highlights the ongoing commoditization of cybercrime tools and the need for more sophisticated detection and prevention mechanisms. While its technical implementation may not be groundbreaking, its business model and promise of platform bypass are. This trend empowers a wider range of threat actors, including those with limited technical skills, to execute effective attacks. This necessitates a multi-layered security approach for organizations, including robust endpoint detection and response (EDR) solutions, advanced threat intelligence feeds, and comprehensive security awareness training for employees. The focus must shift beyond merely identifying known malware signatures to detecting anomalous behaviors and indicators of compromise within the browsing environment.
Recent reports from cybersecurity firms like Symantec and LayerX have consistently highlighted the persistent challenge of malicious extensions slipping through the cracks of official app stores. These incidents underscore that ‘Stanley’ is not an isolated phenomenon but rather a symptom of a broader, ongoing vulnerability. The constant cat-and-mouse game between threat actors and platform defenders means that even the most rigorous review processes can be circumvented. Therefore, mitigating the risks posed by services like ‘Stanley’ requires a concerted effort from all stakeholders. Users are advised to exercise extreme caution when installing any browser extension, regardless of its apparent legitimacy. Best practices include installing only the absolute minimum number of extensions required, meticulously reading user reviews, verifying the publisher’s trustworthiness and reputation, and carefully reviewing the permissions requested by each extension. Enterprise environments should consider implementing strict policies regarding extension installation, potentially utilizing whitelisting approaches and continuous monitoring of browser activity.
In conclusion, the emergence of the ‘Stanley’ MaaS signifies a concerning evolution in the landscape of cyber threats, particularly those targeting browser extensions. Its promise of guaranteed publication to the Chrome Web Store, coupled with its highly deceptive phishing mechanism, represents a direct and potent threat to user security and platform integrity. While its technical underpinnings may not be revolutionary, its accessibility and strategic focus on circumventing security measures make it a formidable tool for cybercriminals. Addressing this threat demands continuous innovation in security technologies, heightened vigilance from users, and an unwavering commitment from platform providers to fortify their defenses against an ever-adapting adversary. The ongoing challenge underscores the critical need for a collaborative approach to cybersecurity, where intelligence sharing and proactive threat mitigation remain paramount.







