A widespread digital disruption has recently ensnared countless individuals worldwide, as malicious actors exploited vulnerabilities within Zendesk-powered customer support platforms to orchestrate an unprecedented global spam campaign. This sophisticated abuse of legitimate infrastructure has inundated inboxes with a deluge of unwanted communications, raising alarms across the cybersecurity landscape. Commencing on January 18th, the coordinated assault leveraged the inherent functionalities of these widely adopted customer relationship management (CRM) systems, transforming them into conduits for an overwhelming volume of unsolicited messages that circumvented conventional email security measures.
The core mechanism of this large-scale incident centers on what industry experts term "relay spam," a method where attackers exploit open or loosely configured systems to send messages on behalf of a third party. In this instance, the vulnerability resided in the default or chosen configurations of numerous corporate Zendesk instances, which permit unauthenticated users to submit support tickets. When a support ticket is created, Zendesk’s automated system dispatches a confirmation email to the address provided by the user. By programmatically generating a vast number of fake support requests, attackers were able to input a multitude of target email addresses, triggering the legitimate Zendesk systems to send unsolicited "confirmation" emails to unsuspecting recipients. This effectively transformed these enterprise-grade customer service portals into involuntary mass-mailing platforms, a stark illustration of how seemingly benign features can be repurposed for nefarious ends.

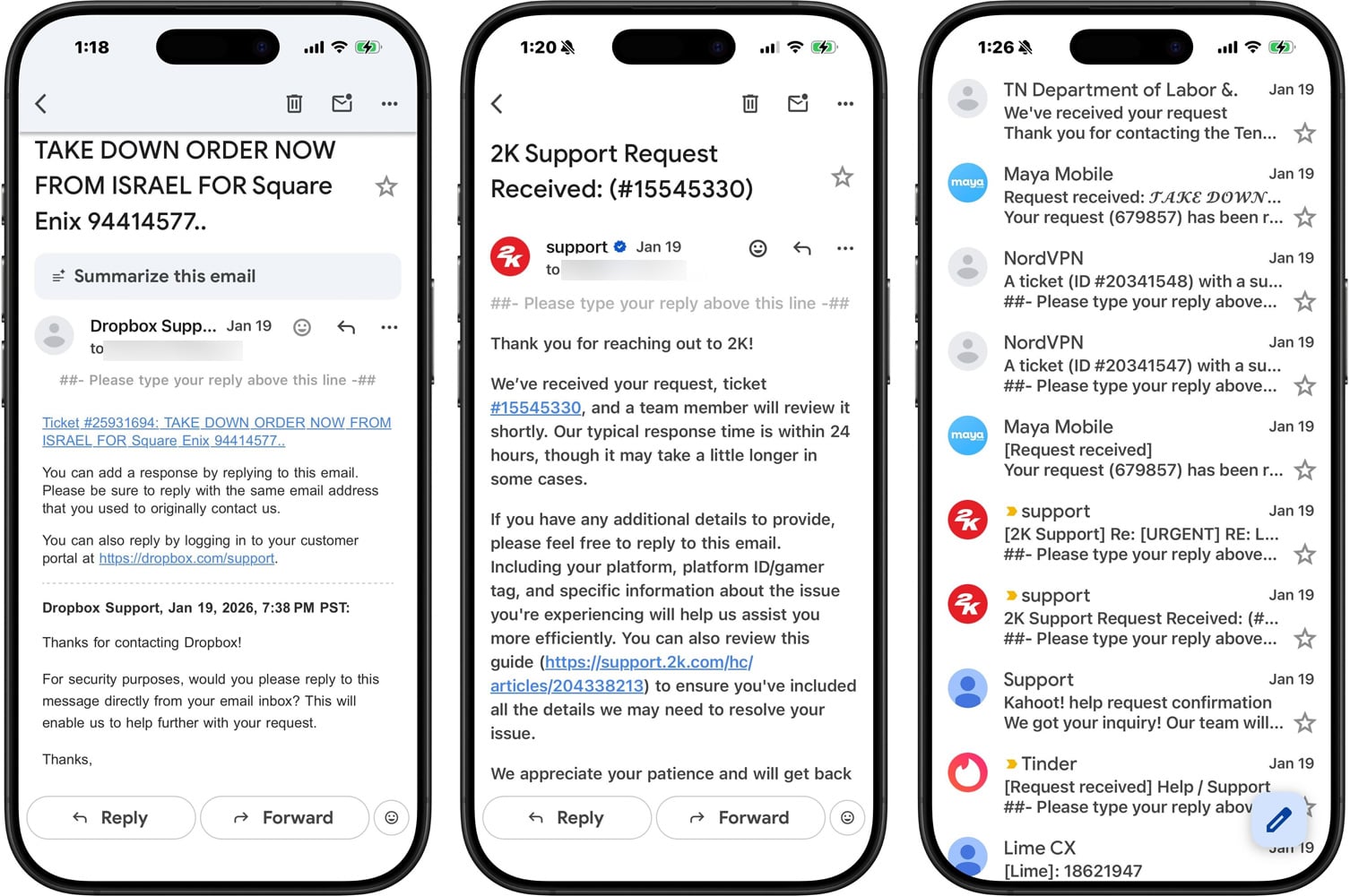
The sheer volume of emails received by victims has been a defining characteristic of this campaign, with reports indicating hundreds of messages flooding personal and professional inboxes within short periods. Unlike typical phishing attempts designed to steal credentials or malware distribution efforts, the initial analysis suggests these emails do not contain direct malicious links or overtly deceptive content aimed at immediate financial gain. Instead, their content often featured bizarre, nonsensical, or provocatively worded subject lines, frequently utilizing Unicode characters to render text in bold or decorative styles, often in multiple languages. Subjects ranged from simulated law enforcement inquiries and corporate takedown notices to offers of digital currency or urgent pleas for help, creating a chaotic and disorienting experience for recipients. This pattern has led some analysts to categorize the activity as "trolling," or a form of digital harassment designed purely to annoy and disrupt, rather than to execute a direct cybercrime. However, the potential for such a campaign to serve as a precursor or distraction for more targeted attacks cannot be dismissed.
The global reach of this incident is underscored by the diverse array of organizations whose Zendesk instances were observed being exploited. A comprehensive list of affected entities included prominent names in technology, gaming, and even government sectors. Noteworthy examples encompassed digital communication giants like Discord, popular dating applications such as Tinder, and leading video game developers including Riot Games and CD Projekt (associated with 2k.com). Furthermore, critical infrastructure and service providers, such as Maya Mobile and NordVPN, were impacted, alongside government departments like the Tennessee Department of Labor and Department of Revenue. The breadth of these organizations, spanning entertainment, telecommunications, and public services, highlights the pervasive integration of Zendesk across various industries and underscores the potential for widespread disruption when a common platform is compromised. This diverse targeting suggests either an indiscriminate approach by the attackers, leveraging any vulnerable instance they could find, or a strategic effort to maximize visibility and impact across different user demographics.
A critical aspect of this spam wave’s efficacy lies in its ability to bypass conventional email security filters. Because the automated confirmation emails originate from legitimate, trusted domains associated with reputable companies, standard spam detection algorithms often fail to flag them as malicious. This inherent legitimacy grants the messages an unprecedented level of access to user inboxes, making them far more intrusive and difficult to mitigate than typical unsolicited commercial email. For individual users, the experience is not merely an annoyance but can also evoke genuine concern, particularly given the alarming or official-sounding nature of some subject lines. The lack of readily identifiable malicious links or attachments, while initially reassuring, simultaneously makes the emails harder to categorize and thus, harder for automated systems to block effectively without risking the suppression of legitimate communications.

In the wake of the incident, several affected companies promptly issued communications to their user bases, acknowledging the situation and providing guidance. Dropbox and 2K, for instance, responded to inquiries, reassuring recipients that their accounts had not been compromised and advising them to disregard the unsolicited emails. These statements typically clarified that their systems permit ticket submission without prior email verification to facilitate ease of access for customer support and feedback. They emphasized that no sensitive account actions or data processing occurs without authenticated, direct instruction from the account holder. This public communication strategy aims to mitigate user panic and reinforce trust, while simultaneously highlighting the inherent tension between user accessibility and stringent security protocols in modern customer service platforms. The delicate balance required to provide frictionless support while safeguarding against abuse remains a persistent challenge for digital service providers.
Zendesk, as the platform provider, has also responded to the widespread abuse. The company announced the implementation of new safety features designed to detect and curb "relay spam" more effectively. These enhancements reportedly include heightened monitoring capabilities and the introduction of rate limits, which are intended to identify unusual activity patterns and halt such campaigns more swiftly. This proactive stance underscores the platform’s commitment to maintaining the integrity and security of its services. Furthermore, it was revealed that Zendesk had previously issued an advisory to its customers in December, warning about this specific type of "relay spam" and offering preventative recommendations. These recommendations included restricting ticket creation to only verified users and eliminating flexible placeholders that could be exploited to manipulate email addresses or subject lines. The incident therefore highlights a critical gap between platform-level warnings and their comprehensive implementation by individual customer organizations, revealing the shared responsibility in maintaining a secure digital ecosystem.
The implications of this Zendesk spam wave extend beyond immediate user annoyance and corporate inconvenience. From a broader cybersecurity perspective, it serves as a powerful reminder of the vulnerabilities inherent in interconnected digital infrastructures and the evolving tactics of malicious actors. The shift from direct malicious payload delivery to leveraging legitimate systems for mass nuisance campaigns signifies a tactical evolution. This type of attack can erode user trust in automated communications, making it harder for legitimate service providers to communicate effectively with their customers. Furthermore, it places a significant burden on the incident response teams of affected companies, diverting resources from other critical security functions.

For organizations utilizing Zendesk or similar customer service platforms, the incident underscores the imperative of reviewing and hardening their security configurations. Restricting ticket creation to verified users, for example, involves implementing a mechanism where users must confirm their email address before a ticket is formally lodged. While this adds a minor step for legitimate users, it significantly raises the barrier for automated spam campaigns. Similarly, the removal of flexible placeholders ensures that attackers cannot inject arbitrary content or recipient information into automated email templates. Beyond these specific recommendations, a holistic approach to platform security is crucial, encompassing regular security audits, robust access controls, multi-factor authentication for support agents, and continuous monitoring for unusual activity patterns.
Looking ahead, this event is likely to prompt a re-evaluation of default security settings and best practices across the SaaS industry. Platform providers like Zendesk face the ongoing challenge of balancing functionality and ease of use with robust security measures. The incident also highlights the concept of "supply chain" attacks in a broader sense, where vulnerabilities in a widely used third-party service can have cascading effects across numerous organizations. As digital interactions become increasingly central to business operations, the security posture of every component in the service delivery chain becomes critical. The ongoing cat-and-mouse game between cyber defenders and attackers will undoubtedly continue to evolve, with future threats potentially leveraging even more sophisticated methods to exploit the trusted channels of legitimate communication platforms. User education remains paramount, empowering individuals to critically assess all incoming communications, even those appearing to originate from trusted sources.







