
A deeply entrenched and technologically evolving malicious browser extension campaign, known as ‘GhostPoster,’ has successfully infiltrated the digital infrastructure of Chrome, Firefox, and Edge, amassing an alarming aggregate of 840,000 installations. Despite initial public disclosures, the threat actors behind this operation have demonstrated remarkable resilience and adaptability, refining their obfuscation and payload delivery mechanisms to maintain operational efficacy. This persistent campaign underscores the escalating sophistication of client-side attacks and presents significant challenges to platform security, user data privacy, and the integrity of online commerce.
The Genesis and Initial Vector of the GhostPoster Threat
The ‘GhostPoster’ campaign first drew the attention of cybersecurity researchers several months prior, when initial investigations uncovered a network of malicious extensions designed to surreptitiously inject harmful JavaScript code into users’ browsing environments. At its inception, the primary innovation observed was the cunning concealment of this malicious code within the seemingly innocuous pixel data of extension logo images. This technique allowed the extensions to bypass conventional static analysis tools employed by browser extension marketplaces, which often scrutinize manifest files and direct script injections but may overlook code embedded within non-executable assets.
This initial method provided a deceptive layer of legitimacy, enabling these extensions to blend in with legitimate offerings within the vast repositories of browser add-ons. Once installed, these seemingly benign tools, often advertised as utility-enhancing or media-downloading applications, would activate their hidden payload. The embedded JavaScript, once extracted and executed, established a covert backdoor, initiating a multi-pronged attack strategy aimed at monitoring user activity and exploiting digital revenue streams.
Dissecting the Malicious Payload and Its Broad Impact

The core functionality of the ‘GhostPoster’ malware revolves around a heavily obfuscated payload, dynamically fetched from external command-and-control servers post-installation. This modular approach allows the threat actors to update their malicious directives without requiring new extension submissions, further enhancing the longevity and adaptability of their campaign. The primary objectives of this sophisticated payload are multifaceted:
-
Comprehensive Browsing Activity Tracking: The extensions are designed to meticulously monitor and collect extensive data on victims’ online activities. This includes visited URLs, search queries, interaction patterns on various websites, and potentially sensitive information entered into web forms. Such data can be leveraged for targeted advertising, identity profiling, or sold on illicit dark web markets, posing severe privacy risks to affected individuals. The sheer volume of data collected from 840,000 users represents a goldmine for malicious actors, enabling granular insights into user behavior and preferences.
-
Affiliate Link Hijacking on E-commerce Platforms: A significant economic driver for the ‘GhostPoster’ campaign is the systematic hijacking of affiliate links. When a user navigates to a major e-commerce platform or clicks on a legitimate affiliate link, the malware intercepts and rewrites the link, replacing the legitimate affiliate ID with one controlled by the threat actors. This ensures that any subsequent purchases made by the victim generate commission for the malicious operators, effectively siphoning revenue from legitimate affiliate marketers and the e-commerce ecosystem. The scale of this operation, with hundreds of thousands of installs, suggests a potentially massive financial gain for the perpetrators.
-
Invisible Iframe Injection for Ad and Click Fraud: Beyond affiliate hijacking, the malware engages in sophisticated ad fraud and click fraud. It achieves this by injecting invisible iframes into visited web pages. These iframes load advertisements in the background, often outside the user’s view, generating fraudulent impressions and clicks. This artificially inflates advertising metrics, defrauding advertisers who pay for genuine engagement and corrupting the integrity of the digital advertising supply chain. The use of invisible iframes is a particularly insidious tactic as it operates silently, leaving no visible trace for the user, making detection challenging without specialized monitoring tools.
The Evolution of Evasion: A New Technical Frontier
Recent intelligence from browser security platforms reveals that the ‘GhostPoster’ campaign is not merely persistent but has undergone a significant technical evolution, demonstrating a clear commitment to advanced evasion and anti-detection strategies. A notable variant, identified within an extension ostensibly designed for "Instagram Downloader" functionality, showcases a heightened level of sophistication.

This advanced variant departs from the earlier method of embedding JavaScript solely in an icon image. Instead, it strategically relocates the core malicious staging logic into the extension’s background script. This move is critical because background scripts operate persistently and with elevated privileges within the browser environment, providing a more stable and less detectable execution context for malicious operations.
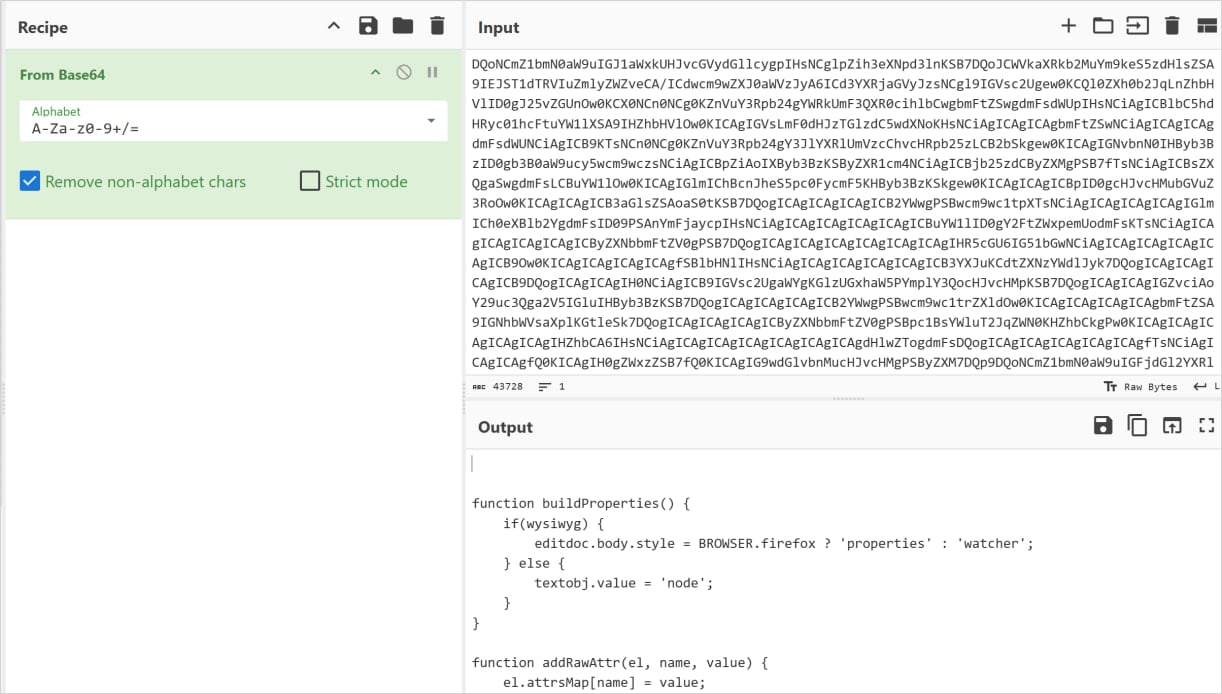
Furthermore, the payload concealment mechanism has been upgraded. Rather than relying on simple icon images, the new variant utilizes a bundled image file as a more elaborate covert container for its payload. At runtime, the background script initiates a sophisticated decoding process: it scans the raw byte data of this bundled image file for a specific, predefined delimiter (e.g., >>>>). Upon locating this marker, it extracts the hidden, encrypted data, stores it temporarily in the extension’s local storage, and then performs a Base64 decoding operation. The final step involves executing the decoded content as JavaScript.
This staged execution flow represents a significant leap in anti-analysis capabilities. As security researchers have noted, this methodology promotes "longer dormancy, modularity, and resilience against both static and behavioral detection mechanisms." Longer dormancy means the malicious code can remain inactive for a period after installation, evading initial scrutiny by automated systems that might flag immediate suspicious activity. Modularity allows the threat actors to easily update or swap out payload components. Most importantly, resilience against static analysis is achieved by separating the executable code from the initial extension package, while behavioral detection is thwarted by the delayed and layered execution process, which appears benign during initial phases.
Scale, Longevity, and Platform Vulnerabilities
The sheer scale of 840,000 installations across multiple browser platforms underscores the profound impact and operational success of the ‘GhostPoster’ campaign. This figure represents a significant user base, translating into substantial potential for data exfiltration and illicit financial gains. The campaign’s longevity is equally concerning; some of these malicious extensions have been active in browser add-on stores since as early as 2020. This extended operational period indicates a sustained ability to bypass the security protocols and review processes of major browser vendors for years.
The campaign’s progression, reportedly originating on Microsoft Edge before expanding to Firefox and Chrome, highlights a systemic vulnerability within the browser extension ecosystem. While browser developers invest heavily in security, the sheer volume of extensions submitted daily, coupled with the ever-evolving tactics of malicious actors, creates a perpetual cat-and-mouse game. The ability of these extensions to remain undetected for such prolonged periods, despite their widespread deployment and clear malicious intent, raises critical questions about the efficacy of current automated and manual review processes.

Browser Ecosystem Security Challenges and the Path Forward
The ‘GhostPoster’ campaign serves as a stark reminder of the inherent challenges in securing open-ended software distribution platforms like browser extension stores. The rapid development and deployment of new extensions, often by anonymous or transient entities, make comprehensive vetting a monumental task. Traditional signature-based detection methods are frequently outmaneuvered by polymorphic code and novel obfuscation techniques.
To combat such sophisticated threats, browser vendors must continue to enhance their security frameworks by integrating advanced behavioral analysis, machine learning algorithms capable of detecting anomalous execution patterns, and more rigorous code auditing. Collaborative intelligence sharing among security researchers and platform providers is also paramount to rapidly identify and remediate emerging threats.
For organizations and individual users, proactive security measures are indispensable. Implementing stringent policies regarding browser extension usage, regularly reviewing installed extensions, and exercising extreme caution when installing new add-ons from unknown developers are critical steps. Enterprises should consider deploying browser security platforms that offer real-time monitoring and threat intelligence specifically tailored to client-side vulnerabilities. Education on the risks associated with seemingly innocuous extensions and the deceptive tactics employed by threat actors is also vital for fostering a more secure online environment.
Remediation Efforts and Lingering Risks
Following the latest disclosures, browser vendors have initiated rapid response measures. The identified malicious extensions have reportedly been removed from Mozilla’s Firefox Add-ons store and Microsoft’s Edge Add-ons store. Google has also confirmed the removal of these extensions from the Chrome Web Store. While this swift action prevents new installations, a significant residual risk persists for users who have already installed these extensions. Unless actively removed by the user, the malware may continue to operate, posing ongoing threats to privacy and security.
Users are strongly advised to review their installed browser extensions immediately and remove any identified as part of the ‘GhostPoster’ campaign. Furthermore, a comprehensive security scan of their systems is recommended to detect and neutralize any residual components or backdoors that might have been established by the malware.
Conclusion
The ‘GhostPoster’ browser extension campaign represents a formidable and evolving threat within the digital landscape. Its ability to achieve widespread distribution, maintain long-term persistence, and adapt its evasion tactics underscores the continuous need for vigilance and innovation in cybersecurity. As threat actors refine their methodologies, particularly through advanced concealment and staged execution, the onus falls on browser vendors, security researchers, and end-users alike to collaborate in building a more resilient and secure online ecosystem. The ongoing battle against sophisticated client-side malware demands not just reactive removal, but a proactive and adaptive defense strategy capable of anticipating and neutralizing threats before they can inflict widespread harm.







