A sophisticated campaign leveraging deceptive browser extensions has been uncovered, systematically targeting critical enterprise resource planning (ERP) and human resources (HR) platforms to illicitly acquire sensitive authentication tokens and impede vital security functions within corporate environments. Recent analysis has illuminated a series of ostensibly benign Chrome browser extensions that, once installed, execute a multi-pronged attack strategy designed for persistent access and disruption, posing a significant risk to organizational data integrity and operational continuity.
The proliferation of browser extensions, designed to augment functionality and streamline workflows, has introduced a nuanced vector for cyber adversaries seeking to infiltrate corporate networks. While many extensions offer genuine utility, the inherent permissions they often require can be exploited, transforming a productivity tool into a formidable espionage or sabotage instrument. In this latest observed campaign, threat actors capitalized on the ubiquitous nature of such add-ons, crafting seemingly legitimate applications for platforms like Workday, NetSuite, and SAP SuccessFactors. These platforms, central to managing a company’s workforce, financial operations, and supply chain, represent highly valuable targets due to the vast repositories of sensitive data they control, including employee personal identifiable information (PII), financial records, intellectual property, and critical operational data.
Security researchers identified five distinct Chrome extensions implicated in this coordinated operation, collectively amassing over 2,300 installations before their detection and subsequent removal from the Chrome Web Store. Despite appearing under different publisher names and branding, a forensic examination revealed striking commonalities in their underlying code structures, API endpoint patterns, and targeted enterprise platforms. This homogeneity strongly suggests a singular, organized threat actor or group orchestrating the campaign, demonstrating a strategic focus on high-value corporate assets rather than broad, indiscriminate attacks. The relatively modest number of installations belies the potential impact, as compromise of even a single enterprise account on these critical platforms can yield catastrophic consequences, ranging from large-scale data breaches to the facilitation of ransomware deployment or significant financial fraud.
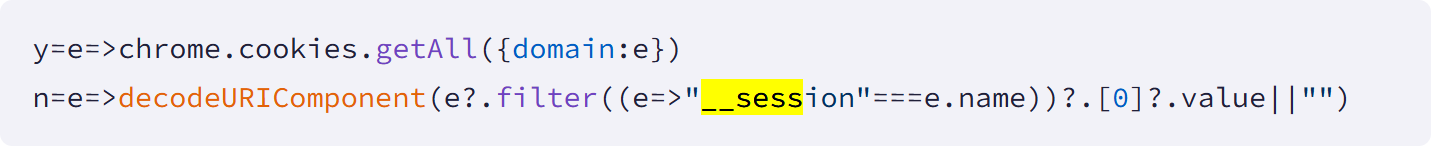
The modus operandi of these malicious extensions involved three primary attack vectors, each meticulously designed to achieve specific objectives within the targeted enterprise infrastructure. The first and most prevalent technique involved the continuous exfiltration of authentication cookies to remote command-and-control (C2) servers. Specifically, the extensions were engineered to identify and extract session cookies—often named "__session"—which contain active login tokens for the targeted platforms. These tokens effectively represent an authenticated user session, granting access without requiring a username, password, or multi-factor authentication (MFA) credentials. The extensions performed this exfiltration every 60 seconds, ensuring that attackers maintained persistent access even if the legitimate user logged out and subsequently re-authenticated. This constant harvesting of session data provides adversaries with a resilient backdoor, circumventing many traditional security controls and making detection challenging.
The second sophisticated tactic employed was the manipulation of the Document Object Model (DOM) to obstruct access to critical security administration pages within the targeted platforms. Two of the identified extensions, specifically "Tool Access 11" and "Data By Cloud 2," were found to detect specific page titles associated with security and incident response functions in Workday. Upon detecting these pages, the extensions would either erase their content, rendering them blank and unusable, or redirect administrators away from these essential management interfaces. "Tool Access 11" was observed targeting 44 distinct administrative pages, encompassing crucial functions such as authentication policies, security proxy configurations, IP range management, and session controls. "Data By Cloud 2" exhibited an even broader scope, obstructing access to 56 pages, including those related to password management, account deactivation, two-factor authentication device controls, and security audit logs. This deliberate impairment of security administration functions serves a dual purpose: it hinders an organization’s ability to detect and respond to ongoing security incidents, and it allows the attackers to operate with reduced risk of discovery or remediation, effectively blinding security teams to their activities.

The most advanced and insidious technique was implemented by the "Software Access" extension, which facilitated bidirectional cookie manipulation. Beyond merely stealing session tokens, this extension possessed the capability to receive stolen cookies from the attacker’s C2 server and inject them directly into the victim’s browser. This two-way exchange of cookies grants attackers an unprecedented level of control, enabling immediate session hijacking without the need for traditional authentication credentials. By setting arbitrary authentication cookies, the adversaries could effectively impersonate any user whose session tokens they possessed, gaining direct access to sensitive enterprise platforms. This method bypasses not only usernames and passwords but also multi-factor authentication mechanisms, representing a significant escalation in attack sophistication and impact. The ability to inject cookies means attackers can sustain compromised sessions or even initiate new ones under a victim’s identity at will, greatly expanding the scope of potential misuse.
The threat actors behind this campaign demonstrated a clear understanding of enterprise operational dynamics, strategically marketing their malicious extensions as productivity enhancers or security tools. Listings on the Chrome Web Store promoted these extensions with language suggesting streamlined workflows, enhanced security controls, or simplified access to "premium tools" for Workday, NetSuite, and other platforms. For instance, "Data By Cloud 2," which had approximately 1,000 installations, was advertised as a dashboard providing bulk management tools and expedited access for users managing multiple enterprise accounts. "Tool Access 11" was deceptively presented as a security-focused add-on designed to restrict access to sensitive administrative features, falsely claiming to prevent account compromise by limiting user interactions with "special tools." This deceptive marketing leveraged the legitimate need within enterprises for efficiency and security, luring unsuspecting users into installing the compromised applications. Crucially, none of these extensions disclosed their true malicious functionalities—cookie extraction, credential exfiltration, or the blocking of security administration pages—in their descriptions or privacy policies, maintaining a veneer of legitimacy.
The implications of such credential-stealing campaigns are profound and far-reaching for affected organizations. The compromise of HR and ERP platforms can lead to extensive data breaches involving highly sensitive employee PII, financial records, payroll data, and proprietary business information. This data can be sold on dark web marketplaces, used for identity theft, or leveraged in subsequent phishing and social engineering attacks. Furthermore, stolen credentials provide an initial access vector that can be exploited for deploying ransomware across the corporate network, initiating financial fraud, or disrupting critical business operations. The obstruction of security management pages further exacerbates these risks by hindering incident response efforts, potentially allowing attackers to maintain persistence and expand their foothold undetected for extended periods. Organizations impacted by these extensions face significant reputational damage, potential regulatory fines under data protection laws like GDPR or CCPA, and substantial costs associated with incident response, forensic investigations, and system remediation.
In light of this evolving threat, organizations must adopt a proactive and multi-layered approach to cybersecurity. Enhanced vigilance regarding browser extensions is paramount; employees should be educated on the risks associated with installing unverified or suspicious extensions, particularly those requesting broad permissions. Security teams should implement strict policies governing the use of browser extensions within the enterprise environment, potentially whitelisting only approved and thoroughly vetted add-ons. Technical controls, such as advanced endpoint detection and response (EDR) solutions that monitor browser activity and network traffic for anomalous behavior, are crucial for detecting exfiltration attempts or DOM manipulation. Furthermore, the principles of Zero Trust should be applied to all enterprise access, ensuring that every access request, regardless of origin, is continuously verified and authenticated, thereby reducing the impact of compromised session tokens. Regular security audits of third-party integrations and robust incident response plans are also essential to mitigate the fallout from successful attacks.
The ongoing battle against sophisticated cyber threats necessitates a collaborative effort between security researchers, platform providers, and end-users. While Google has acted promptly to remove the reported malicious extensions, the underlying challenge of vetting and securing vast extension marketplaces remains. The future outlook suggests a continued evolution of such browser-based attacks, likely expanding to target other critical Software-as-a-Service (SaaS) platforms and leveraging increasingly sophisticated social engineering tactics. Organizations must therefore remain agile, continuously updating their security postures, investing in advanced threat intelligence, and fostering a strong security culture to defend against these persistent and evolving digital threats. Incident response for affected entities should include immediate reporting to security administrators, comprehensive forensic analysis to determine the extent of compromise, and mandatory password resets and MFA re-enrollment across all potentially impacted platforms.







