
A formidable and continuously evolving cyber threat, dubbed "GlassWorm," has initiated its fourth documented campaign, now specifically targeting the macOS developer community with highly insidious tactics involving trojanized cryptocurrency wallet applications delivered through compromised VSCode/OpenVSX extensions. This latest iteration marks a significant escalation, shifting its focus from a broader Windows-centric approach to a dedicated assault on Apple’s operating system, leveraging advanced obfuscation, persistence mechanisms, and a decentralized command-and-control infrastructure.
The genesis of the GlassWorm campaign can be traced back to October of the previous year when security researchers first identified its clandestine presence within developer ecosystems. Initial attacks manifested through malicious extensions embedded in the OpenVSX registry and, at times, the Microsoft Visual Studio Marketplace. These platforms serve as critical repositories for extensions that augment the functionality of VS Code-compatible editors, providing developers with essential tools, language support, and productivity enhancements. While the Microsoft marketplace operates as the official distribution channel for Visual Studio Code, OpenVSX offers an open, vendor-neutral alternative, catering to editors that either do not support or opt not to rely on Microsoft’s proprietary infrastructure. The initial wave of GlassWorm employed a deceptive technique, concealing its malicious code within extensions using "invisible" Unicode characters, a subtle form of obfuscation designed to evade cursory inspection. Upon successful installation, this initial variant demonstrated a broad range of malicious capabilities, including the systematic exfiltration of sensitive credentials pertinent to GitHub, npm, and OpenVSX accounts. Crucially, it also targeted cryptocurrency wallet data, seeking to compromise digital assets held by developers. Beyond data theft, the malware established a robust foothold on compromised systems, enabling remote access through VNC (Virtual Network Computing) and facilitating traffic routing via a SOCKS proxy, transforming victim machines into unwitting nodes for further illicit activities.
Despite public exposure and the subsequent implementation of enhanced defensive measures, GlassWorm proved to be a resilient and adaptive adversary. Following its initial discovery, the malware swiftly resurfaced in early November, once again leveraging the OpenVSX platform for distribution, demonstrating its capacity for rapid re-engineering and redeployment. A third wave emerged in early December, this time migrating back to the VSCode marketplace, showcasing the threat actor’s agility in navigating and exploiting vulnerabilities across different distribution channels. Each subsequent wave brought subtle yet significant modifications, reflecting a continuous effort to bypass detection and improve efficacy, underscoring the dynamic nature of this particular threat.

The most recent iteration, constituting the fourth wave, represents a strategic pivot and a substantial upgrade in the GlassWorm operational framework. Identified by security experts at Koi Security, this campaign is exclusively engineered to target macOS systems, a notable departure from its predecessors which primarily focused on Windows environments. This shift signifies a recognition by the threat actors of the increasing value and presence of macOS within the developer community, coupled with a potential perception of lower scrutiny or different security paradigms compared to Windows. The methods of payload delivery have also evolved; instead of relying on the invisible Unicode characters of the first two waves or the compiled Rust binaries observed in the third, the current attacks embed an AES-256-CBC encrypted payload within compiled JavaScript directly within the OpenVSX extensions. This layered approach to obfuscation and encryption complicates analysis and detection, requiring more sophisticated reverse engineering techniques to unravel the malware’s true intent. A notable feature of this new variant is a deliberate 15-minute delay before the malicious logic executes, a common tactic employed by advanced persistent threats to thwart automated analysis in sandboxed environments, which typically monitor for immediate suspicious activity.
The architectural changes in the latest GlassWorm campaign extend to its persistence mechanisms and operational toolkit. For instance, the malware now leverages AppleScript for executing malicious commands, replacing the PowerShell scripts utilized in Windows-centric attacks. Similarly, instead of modifying the Windows Registry for persistence, it now employs LaunchAgents, a standard macOS mechanism for launching programs at specific times or events, allowing the malware to maintain a persistent presence across system reboots. This meticulous adaptation to the macOS operating system highlights the attacker’s in-depth understanding of the platform’s intricacies and security architecture. Despite these significant shifts in execution and persistence, the command-and-control (C2) mechanism remains consistent, relying on the Solana blockchain. The use of a decentralized blockchain for C2 offers distinct advantages to threat actors, making it significantly harder for security researchers and law enforcement to dismantle the C2 infrastructure, as there is no single point of failure to target. Researchers have also noted an overlap in the underlying infrastructure, suggesting a continuity in the threat actor group behind these campaigns.
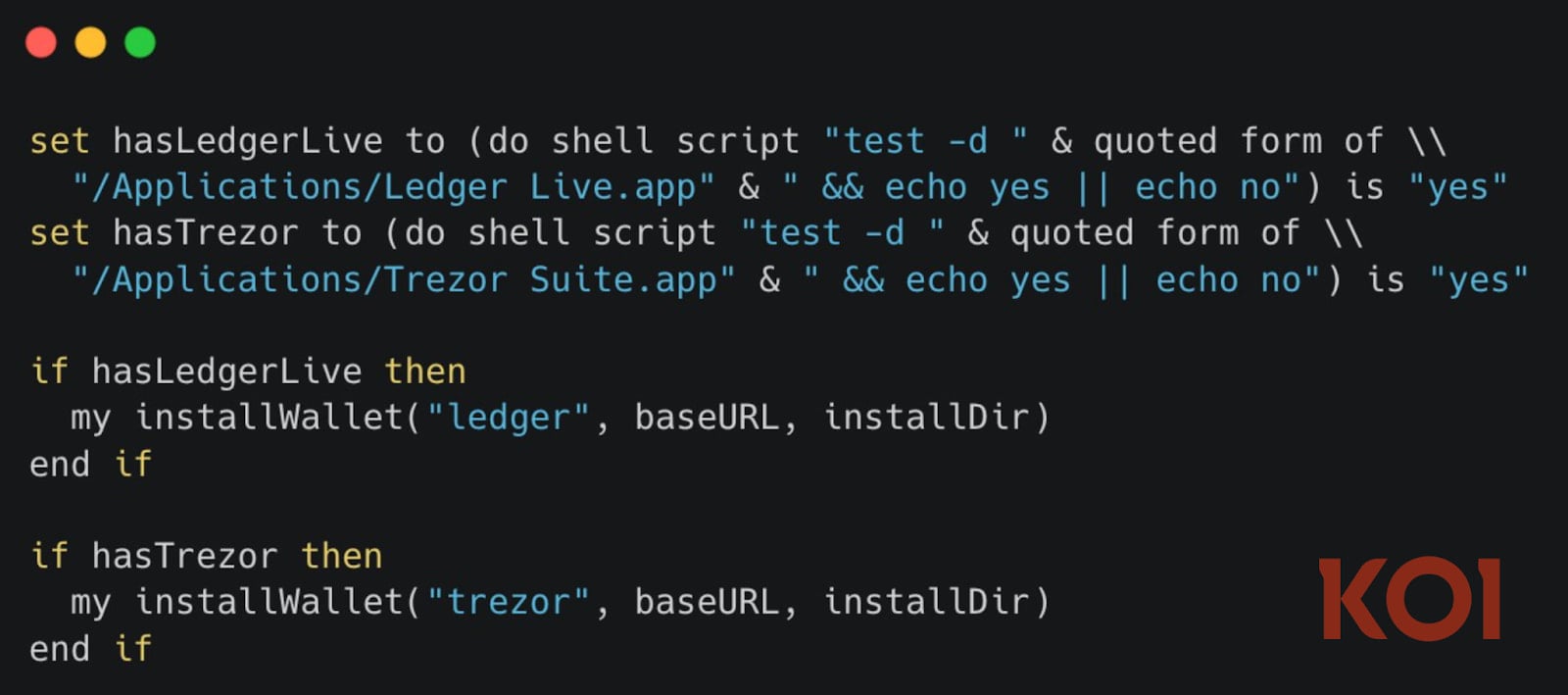
The expanded capabilities of this macOS-focused GlassWorm variant are particularly alarming. Beyond its previous targets of browser-based cryptocurrency extensions, GitHub, and npm developer credentials, and general browser data, the malware now actively attempts to steal Keychain passwords. The macOS Keychain stores a multitude of sensitive information, including website login credentials, Wi-Fi network passwords, and encrypted notes, making its compromise a critical security breach. Furthermore, a highly concerning new feature has been integrated: the malware actively scans for the presence of legitimate hardware cryptocurrency wallet applications such as Ledger Live and Trezor Suite on the victim’s system. If detected, it attempts to replace these authentic applications with trojanized versions. This direct targeting of hardware wallet management software, which is often considered the gold standard for cryptocurrency security, represents a severe escalation in the threat landscape for digital asset holders.

While the capability to replace legitimate hardware wallet applications with malicious versions is fully developed within the malware’s code, Koi Security’s analysis indicates that this specific mechanism is currently failing, with the trojanized wallet files returning as empty. This anomaly suggests several possibilities: the attackers may still be in the preparatory phase of developing or uploading fully functional macOS wallet trojans, or their backend infrastructure for delivering these specific payloads might be undergoing transition or refinement. Regardless of the current operational status of this particular function, the underlying capability is demonstrably built and ready for deployment. The implication is clear: once the necessary payloads are uploaded, this feature will become fully operational, posing an existential threat to hardware wallet users on macOS. Crucially, all other malicious functionalities, including credential theft, unauthorized access to the Keychain, data exfiltration, and persistence mechanisms, are reported to be fully operational and effective.
The ongoing presence of these malicious extensions on platforms like OpenVSX, even with publisher verification warnings, underscores a fundamental vulnerability within the developer ecosystem. The reported download counters, exceeding 33,000 installations for some extensions, are particularly concerning, although such figures are frequently inflated by threat actors to project an image of legitimacy and trustworthiness. The inherent trust placed in development tools and extensions makes them prime targets for supply chain attacks. Developers, by nature of their work, often download numerous extensions to enhance productivity, sometimes without rigorous scrutiny of their origins or integrity. This blind spot creates an ideal vector for malware like GlassWorm to infiltrate critical systems.
The implications for the macOS ecosystem are profound. As macOS gains increasing traction among developers, creative professionals, and high-value targets, it naturally attracts more sophisticated and dedicated cyber threats. The perceived security of macOS, while often higher than other operating systems out-of-the-box, can lead to a false sense of complacency, making users potentially less vigilant against highly targeted attacks. The compromise of developer accounts (GitHub, npm) can have cascading effects, potentially leading to further supply chain attacks where malicious code is injected into legitimate projects, affecting a wider user base. Financial losses from compromised cryptocurrency wallets can be irreversible, and the theft of Keychain passwords exposes a wealth of personal and professional data.
From a strategic analytical perspective, the GlassWorm campaign showcases a high degree of attacker sophistication and adaptability. The rapid evolution across multiple waves, the shift in operating system targets, and the continuous refinement of evasion techniques (e.g., Unicode, Rust binaries, AES-256-CBC JavaScript) demonstrate a well-resourced and persistent threat actor. The choice of a decentralized Solana blockchain for C2 further highlights a move towards resilient and censorship-resistant infrastructure, making takedowns more challenging. The 15-minute delay tactic is a hallmark of sophisticated malware designed to bypass automated security solutions. This campaign is not merely opportunistic; it represents a targeted and calculated effort to compromise high-value individuals within the software development and cryptocurrency sectors.
In response to this persistent threat, developers are strongly advised to adopt a proactive and defensive posture. Immediate action is warranted for anyone who has installed any of the identified malicious extensions; they must be removed without delay. Following removal, a comprehensive security audit of the system is imperative, or, ideally, a complete reinstallation of the operating system to ensure no residual malware components remain. Crucially, all affected credentials, particularly GitHub account passwords, must be reset, and any associated npm tokens should be revoked immediately. The implementation of multi-factor authentication (MFA) on all developer accounts and cryptocurrency platforms is no longer optional but a critical baseline security measure. Beyond immediate remediation, developers should cultivate a habit of extreme caution when installing extensions, verifying publisher authenticity through multiple sources, and scrutinizing permissions requested by new software. Organizations employing macOS developers must also integrate robust supply chain security practices, including rigorous vetting of third-party tools and extensions, continuous monitoring of developer endpoints for anomalous activity, and comprehensive security awareness training.
The GlassWorm campaign serves as a stark reminder of the escalating risks within the software supply chain and the evolving tactics employed by cybercriminals targeting digital assets. As the digital economy continues its expansion, and developers become increasingly central to innovation, the tools and environments they rely upon will remain attractive targets. The ongoing cat-and-mouse game between threat actors and cybersecurity defenders necessitates continuous vigilance, rapid intelligence sharing, and the adoption of advanced security paradigms to safeguard against such persistent and adaptive threats. The future outlook suggests a continued proliferation of sophisticated supply chain attacks, emphasizing the critical need for a multi-layered defense strategy and an ingrained culture of security within the developer community.







