
A sophisticated cyber offensive, attributed to the North Korean state-sponsored threat group known as Konni, has escalated its tactics by employing bespoke, AI-generated PowerShell malware to compromise high-value targets within the global blockchain engineering ecosystem. This strategic pivot highlights an evolving landscape where advanced persistent threat (APT) groups leverage artificial intelligence to craft more elusive and potent digital weaponry, specifically designed to infiltrate critical development environments and exfiltrate sensitive cryptocurrency assets.
Konni, also identified by intelligence agencies under the aliases Opal Sleet and TA406, is a prolific and persistent cyber espionage entity with a documented operational history spanning back to at least 2014. This group is widely believed to maintain close affiliations with other notorious North Korean clusters, including APT37 and Kimsuky, suggesting a coordinated and multi-faceted national cyber agenda. Historically, Konni’s targeting spectrum has been broad, encompassing governmental bodies, diplomatic missions, and defense sectors across multiple geographies, including South Korea, Russia, Ukraine, and various European nations. The current campaign, however, demonstrates a sharpened focus on the burgeoning blockchain industry, particularly within the Asia-Pacific region, with forensic evidence indicating initial malware submissions originating from Japan, Australia, and India. This geographical concentration underscores a calculated effort to exploit vulnerabilities in a rapidly expanding sector crucial to global financial innovation.

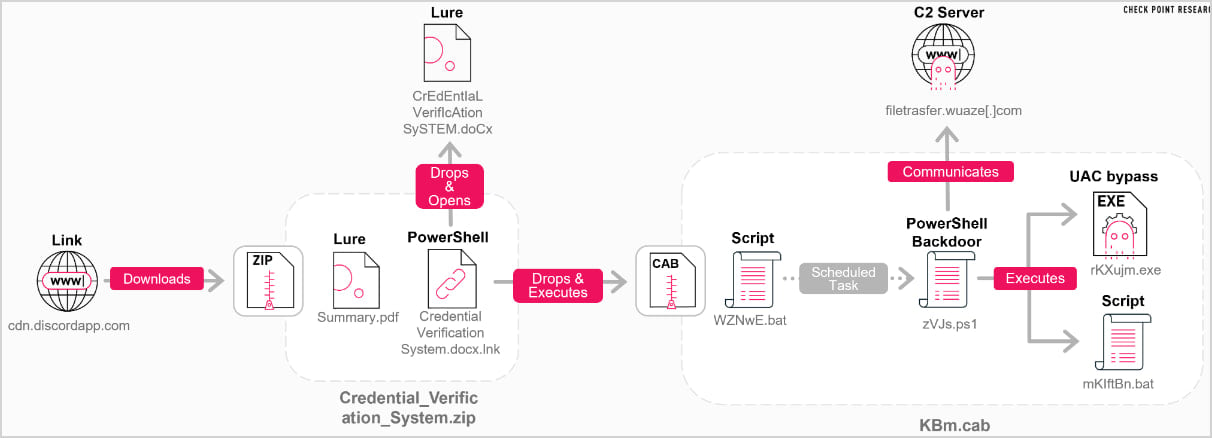
The initial breach vector for this refined attack chain is a meticulously crafted spear-phishing attempt, delivered via a Discord-hosted link. Upon engagement, the unsuspecting victim is prompted to download a ZIP archive. This archive is ingeniously designed to contain a seemingly innocuous PDF document, acting as a decoy, alongside a highly malicious LNK shortcut file. This seemingly benign LNK file is the linchpin of the initial compromise, initiating a complex, multi-stage infection sequence designed to establish a persistent foothold within the target’s system.
Execution of the LNK shortcut triggers an embedded PowerShell loader, a crucial component that orchestrates the subsequent stages of the attack. This loader is responsible for extracting two key elements: a decoy DOCX document and a self-contained CAB archive. The DOCX document, when opened, serves as a convincing lure, presenting content designed to misdirect the victim while the underlying malicious processes unfold. Concurrently, the CAB archive, a compressed file format, surreptitiously unpacks its payload, which includes a highly sophisticated PowerShell backdoor, two ancillary batch files, and a User Account Control (UAC) bypass executable. This intricate layering of components is indicative of a well-resourced and technically proficient adversary aiming for deep system compromise.
The content of the decoy DOCX document is specifically tailored to the target audience – blockchain engineers and developers. It articulates a plausible scenario, such as a project proposal or technical specification, while implicitly suggesting the hackers’ ultimate objective: to compromise development environments. Gaining access to these environments is highly coveted, as it provides a gateway to a treasure trove of sensitive assets, including critical infrastructure credentials, API keys, direct wallet access, and, ultimately, significant cryptocurrency holdings. The high-value nature of these targets explains the investment in developing such a sophisticated and multi-layered attack.

Following the initial execution, the first batch file meticulously prepares a staging directory on the compromised system. This directory serves as a clandestine repository for the PowerShell backdoor and the second batch file. A critical step in establishing persistence involves the creation of an hourly scheduled task, cunningly disguised as a legitimate OneDrive startup task. This scheduled task is designed to operate stealthily, reading an XOR-encrypted PowerShell script directly from disk. This script is then decrypted in memory, ensuring its execution without leaving easily traceable forensic artifacts on the disk. Upon successful execution, the task self-destructs, further erasing traces of its activity and making detection and forensic analysis significantly more challenging for security professionals. This level of operational security is a hallmark of state-sponsored actors.
The core of Konni’s enhanced capabilities in this campaign resides in the PowerShell backdoor itself, which exhibits characteristics strongly suggesting AI-assisted development. The malware is heavily obfuscated using advanced techniques, including arithmetic-based string encoding and sophisticated runtime string reconstruction. The final malicious logic is executed via Invoke-Expression, a powerful PowerShell cmdlet often abused by attackers to run arbitrary code dynamically. What truly distinguishes this particular backdoor, according to cybersecurity researchers, is its unusual structure and explicit internal comments. Unlike typical operator-authored malware, which often prioritizes conciseness and stealth over readability, this script features clear, structured documentation at its inception and a remarkably modular, clean layout.
A particularly telling piece of evidence pointing to Large Language Model (LLM) generation is the presence of a specific comment: # – your permanent project UUID. This phrasing is highly characteristic of code generated by AI models, where the model explicitly instructs a human user on how to customize a placeholder value. Such didactic comments are frequently observed in AI-produced scripts, tutorials, and boilerplate code, serving as a subtle yet significant indicator of its origin. The adoption of AI tools by state-sponsored groups like Konni signifies a lower barrier to entry for developing complex malware, potentially leading to faster development cycles, increased sophistication in evasion techniques, and a greater challenge for traditional signature-based detection mechanisms. This development marks a significant shift in the cyber threat landscape, where adversaries can leverage readily available AI platforms to augment their offensive capabilities.
Prior to fully establishing its malicious operations, the backdoor incorporates robust anti-analysis checks. It meticulously performs hardware, software, and user activity assessments to ascertain whether it is operating within a controlled analysis environment, such as a sandbox or virtual machine. If such an environment is detected, the malware will cease its execution or alter its behavior to avoid detection and reverse engineering. Once these checks are passed, the malware generates a unique host ID, crucial for identifying and tracking compromised systems. Subsequently, the backdoor dynamically adapts its actions based on the execution privileges it has successfully acquired on the compromised host. This privilege-based action diagram illustrates a sophisticated, adaptive strategy, where the malware can escalate its capabilities and pursue different objectives depending on the level of access it achieves, from basic data exfiltration to deeper system control and lateral movement.
Once fully operational on the infected device, the backdoor establishes periodic communication with its command-and-control (C2) server. This communication involves sending basic host metadata, providing the attackers with initial reconnaissance data about the compromised system. The backdoor then polls the C2 server at randomized intervals, a technique designed to evade detection by network monitoring systems that might flag regular, predictable communication patterns. If the C2 server responds with additional PowerShell code, the backdoor seamlessly transforms this code into a script block and executes it asynchronously via background jobs. This method allows the attackers to inject new commands and expand their control over the compromised system without directly interfering with normal user operations, making their presence harder to detect.
The attribution of these sophisticated attacks to the Konni threat actor is founded on a confluence of forensic evidence. Cybersecurity researchers have identified distinct commonalities with earlier Konni operations, including overlaps in launcher formats, specific lure filenames, and script names. Furthermore, the structural consistency in the execution chain observed in this campaign strongly aligns with established Konni methodologies. These technical indicators provide a robust basis for linking the current AI-enhanced attacks to the well-documented activities of this North Korean state-sponsored group, reinforcing the understanding of their evolving TTPs (Tactics, Techniques, and Procedures).
The implications of this campaign for the blockchain sector are profound. Blockchain engineers and developers are prime targets due to their privileged access to high-value digital assets, sensitive intellectual property, and critical infrastructure within the decentralized finance ecosystem. A successful compromise can lead to not only direct financial theft but also intellectual property loss, supply chain attacks (if development environments are used to inject malicious code into legitimate projects), and reputational damage. Organizations operating in this space must recognize the heightened threat level and implement robust security measures.
Mitigation and defense strategies must be multi-faceted and proactive. Organizations must prioritize comprehensive employee security awareness training, particularly regarding spear-phishing tactics and the dangers of interacting with suspicious links or attachments, even from seemingly legitimate sources. Robust endpoint detection and response (EDR) solutions, coupled with advanced network monitoring, are essential to detect and block malicious activity early in the kill chain. Implementing strong access controls, multi-factor authentication (MFA) across all critical systems, and regular security audits of development environments are paramount. Furthermore, the emergence of AI-generated malware necessitates a shift towards AI-aware security solutions capable of identifying anomalous code structures and behavioral patterns that might bypass traditional signature-based defenses. Sharing threat intelligence, including the Indicators of Compromise (IoCs) associated with this campaign, is critical for collective defense.
Looking ahead, Konni’s adoption of AI in malware development signals a broader trend in cyber warfare. The ability to rapidly generate highly obfuscated, polymorphic, and adaptive malware components using LLMs will likely democratize access to advanced offensive capabilities, potentially lowering the technical barrier for threat actors. This will necessitate a parallel evolution in defensive strategies, focusing on behavioral analytics, anomaly detection, and potentially leveraging AI in defense to counter AI in offense. The ongoing cyber arms race will increasingly be fought on the frontier of artificial intelligence, demanding continuous innovation and vigilance from the global cybersecurity community to protect critical infrastructure and financial systems.








