In a significant blow to the global cybercrime ecosystem, Microsoft, in a concerted international effort, has effectively dismantled RedVDS, a sophisticated virtual desktop service that served as a foundational platform for a vast array of illicit digital activities. This decisive action, spearheaded by Microsoft’s Digital Crimes Unit (DCU) and involving law enforcement agencies across multiple continents, targets the very infrastructure enabling widespread fraud, data theft, and financial exploitation, which has reportedly cost victims in the United States alone over $40 million since March 2025.
The operation, executed with the strategic collaboration of Europol and German authorities, involved a multi-pronged legal and technical offensive. Microsoft initiated civil litigation in both the United States and the United Kingdom, leading to the seizure of critical malicious infrastructure and the subsequent incapacitation of RedVDS’s primary marketplace and customer portals. This highly coordinated intervention marks a critical step in disrupting the "cybercrime-as-a-service" model that has fueled a surge in digitally-enabled offenses worldwide.
To underscore the tangible impact of RedVDS’s operations, Microsoft was joined in its legal proceedings by two key co-plaintiffs who had suffered substantial losses. H2-Pharma, a pharmaceutical firm based in Alabama, reported a staggering $7.3 million loss attributed to a sophisticated business email compromise (BEC) scheme facilitated by RedVDS. Similarly, the Gatehouse Dock Condominium Association in Florida experienced a near half-million-dollar depletion of resident funds due to related fraudulent activities. These instances serve as stark reminders of the profound financial and operational damage inflicted upon legitimate businesses and organizations by such platforms.

Steven Masada, Assistant General Counsel within Microsoft’s Digital Crimes Unit, articulated the insidious nature of RedVDS, stating that for a minimal monthly fee—reportedly as low as $24—the service provided cybercriminals with readily accessible, disposable virtual computers. This affordability and ease of access made fraud economically viable, highly scalable, and exceptionally challenging for law enforcement to trace. Masada emphasized that such services have quietly become a pervasive force, underpinning the escalating tide of cyber-enabled crime that indiscriminately harms individuals, corporations, and communities globally.
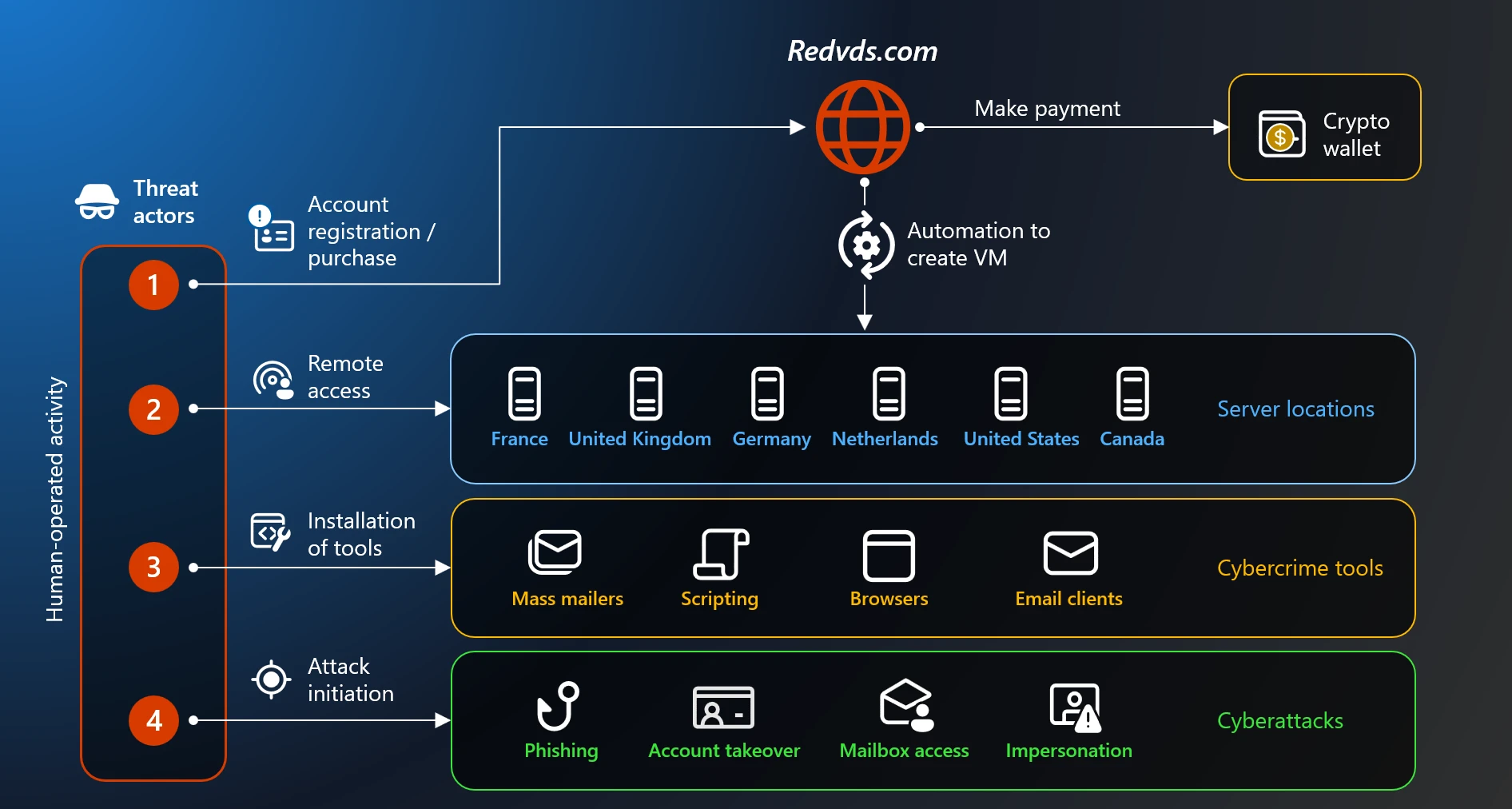
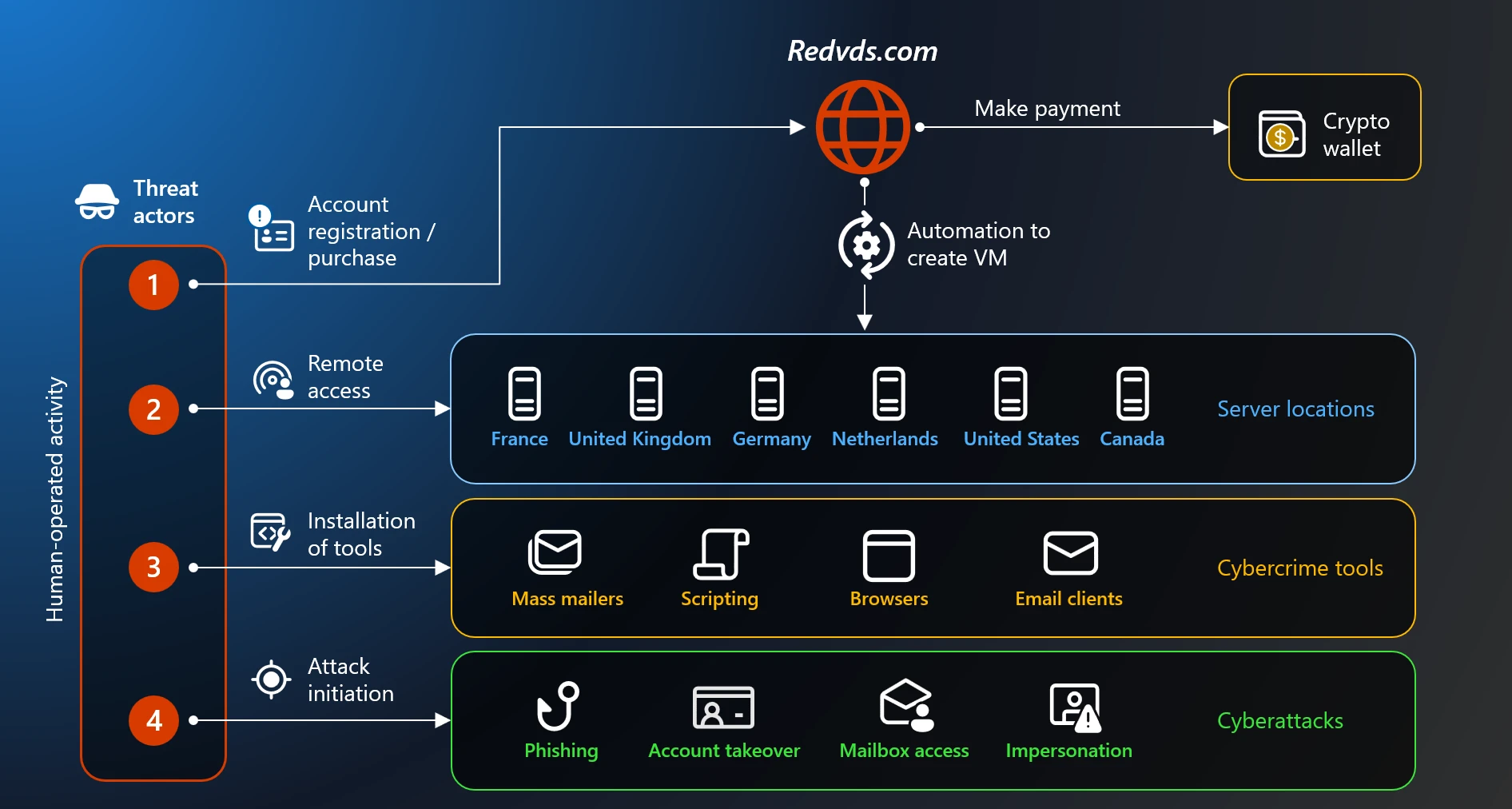
RedVDS, which had been operational as a cybercrime-as-a-service provider since 2019, utilized a network of domains including redvds[.]com, redvds[.]pro, and vdspanel[.]space. Its core offering was access to virtual Windows cloud servers, complete with administrator privileges and no usage restrictions. This robust, low-cost infrastructure proved highly attractive to numerous cybercriminal syndicates, including prominent threat actors tracked by Microsoft as Storm-0259, Storm-2227, Storm-1575, and Storm-1747, among others. These groups leveraged the platform to execute a wide spectrum of malicious campaigns.
A crucial breakthrough in Microsoft’s investigation involved identifying a distinctive technical fingerprint. Analysis revealed that the developer and operator of RedVDS, identified internally as Storm-2470, had created all virtual machines from a single, cloned Windows Server 2022 image. This resulted in every instance sharing an identical computer name: WIN-BUNS25TD77J. This seemingly minor anomaly proved to be a critical forensic clue, allowing investigators to meticulously track the service’s operational footprint across a multitude of disparate malicious campaigns, thereby unraveling the full extent of its reach.

The operational strategy of RedVDS involved renting servers from legitimate third-party hosting providers situated across a diverse geographical spread, including the United States, the United Kingdom, France, Canada, the Netherlands, and Germany. This distributed infrastructure enabled RedVDS customers to provision IP addresses in close geographical proximity to their intended targets, a tactic specifically designed to bypass location-based security filters and obfuscate their true origins. The ability to rapidly deploy and decommission these virtual environments provided criminals with a high degree of agility and anonymity.
Investigations into the activities facilitated by RedVDS servers unveiled a comprehensive arsenal of malicious tools and software deployed by its clientele. This included sophisticated mass-mailing utilities for large-scale phishing operations, email address harvesters for compiling target lists, privacy tools to maintain anonymity, and remote-access software for gaining unauthorized control over victim systems. The service thus provided an all-encompassing toolkit for cybercriminals to launch mass phishing campaigns, host fraudulent infrastructure, and orchestrate complex fraud schemes, all while leveraging cryptocurrency payments to ensure anonymity.
Beyond phishing and general fraud, RedVDS servers were instrumental in a range of more specialized and high-impact cybercrimes. These included widespread credential theft, enabling account takeovers across various platforms; sophisticated business email compromise (BEC) attacks, often referred to as payment diversion schemes, which tricked organizations into rerouting legitimate payments to criminal accounts; and highly damaging real estate payment diversion scams. The latter, in particular, led to colossal financial losses for over 9,000 customers across Canada and Australia, demonstrating the global and devastating reach of RedVDS-enabled criminal enterprises.
A concerning trend identified by Microsoft’s investigation was the increasing adoption of advanced technologies by RedVDS customers. Many criminals were found to be utilizing artificial intelligence tools, including large language models like ChatGPT, to generate more convincing and grammatically flawless phishing emails, significantly increasing their success rates. Furthermore, some malicious actors employed sophisticated deepfake technologies, such as face-swapping, video manipulation, and voice cloning, to impersonate trusted individuals and organizations, adding a new layer of deception and making it even harder for victims to detect fraud.
The sheer scale of RedVDS’s operations is staggering. In a single month, cybercriminals operating more than 2,600 RedVDS virtual machines were observed sending an average of one million phishing messages per day specifically targeting Microsoft customers. This relentless assault culminated in the compromise of nearly 200,000 Microsoft accounts within a four-month period. Masada highlighted that since September 2025, attacks enabled by RedVDS infrastructure have led to the compromise or fraudulent access of over 191,000 organizations globally. He further clarified that these figures represent only a subset of the accounts impacted across all technology providers, underscoring how rapidly and extensively such infrastructure can amplify the scale and impact of cyberattacks.
This latest disruption by Microsoft’s Digital Crimes Unit is part of a broader, sustained effort to dismantle the underlying infrastructure of cybercrime. In a related operation in September, in coordination with Cloudflare, Microsoft successfully disrupted RaccoonO365, another massive Phishing-as-a-Service (PhaaS) operation responsible for stealing thousands of Microsoft 365 credentials. These consecutive actions demonstrate a strategic shift towards targeting the enablers of cybercrime, aiming to cut off the resources and services that empower malicious actors globally.
The ongoing battle against cybercrime necessitates a multi-faceted approach, combining robust technical defenses, proactive intelligence gathering, stringent legal action, and unparalleled international cooperation. The dismantling of RedVDS serves as a potent reminder of the persistent threat posed by organized cybercrime and the critical importance of public-private partnerships in safeguarding the digital ecosystem. As cybercriminals continue to innovate and leverage new technologies like AI, the cybersecurity community must remain vigilant, adaptable, and collaborative to stay ahead of evolving threats and protect individuals and enterprises from pervasive digital fraud and exploitation. The success against RedVDS offers a template for future operations, emphasizing the strategic value of targeting the infrastructure that makes cybercrime "cheap, scalable, and difficult to trace."







