The contemporary cybersecurity landscape has fundamentally shifted, with adversaries increasingly bypassing traditional perimeter defenses by compromising user identities, rendering robust Identity Threat Detection and Response (ITDR) an indispensable cornerstone of any forward-thinking organizational security strategy for the coming year. This strategic imperative stems from the undeniable reality that sophisticated attackers no longer primarily seek to "break into" systems; instead, they adeptly "log in" using stolen or manipulated credentials, exploiting the trust inherent in legitimate user accounts. Counteracting this pervasive threat necessitates a profound and granular understanding of all IT events, enabling organizations to proactively identify and neutralize suspicious identity-related activities before they escalate into catastrophic breaches.
The Evolving Nexus of Cyberattack: Identities Under Siege
Identity-based incursions represent the predominant vector for cyberattacks confronting enterprises today. The sheer volume and relentless nature of these attacks, ranging from meticulously crafted phishing campaigns and widespread password spraying to sophisticated social engineering tactics and the exploitation of leaked credentials, underscore their efficacy. These low-effort, high-impact methodologies are easily automated and scalable, creating a continuous barrage that can erode even the most robust human vigilance and technical safeguards. The critical vulnerability lies in the fact that a single successful breach among thousands of attempts can precipitate profound organizational disruption and financial ruin.
Once an unauthorized entity gains access to a legitimate account within a network, their operational tempo accelerates dramatically. Attackers swiftly engage in lateral movement across systems, escalate privileges, exfiltrate sensitive data, and meticulously obscure their tracks, often maintaining a dormant presence for extended periods. This dwell time allows them to thoroughly map the network, identify high-value targets, and position themselves to inflict maximum damage at a moment of their choosing, frequently culminating in data encryption, widespread system compromise, or public exposure of sensitive information. The silent infiltration and subsequent calculated destruction highlight the inadequacy of solely preventive measures.
Transcending Risk Mitigation: The Imperative for Proactive Defense
Organizations traditionally implement a layered defense architecture comprising various risk mitigation strategies. These foundational security controls are undoubtedly crucial and should remain integral to any comprehensive security framework. Email filtering systems, for instance, are designed to intercept and quarantine malicious phishing attempts before they reach end-users’ inboxes. Multi-Factor Authentication (MFA) and conditional access policies serve as critical barriers against unauthorized logins, adding essential layers of verification beyond mere passwords. Furthermore, the meticulous application of the Principle of Least Privilege (PoLP) ensures that users and systems are granted only the minimum necessary access rights required to perform their functions, thereby significantly limiting the potential blast radius should a single account become compromised. While these measures collectively contribute to a stronger security posture, they inherently operate on the premise of prevention and risk reduction.
However, the undeniable truth remains that no single preventive measure, or even a combination thereof, offers absolute infallibility. This inherent limitation leaves security teams confronting a critical and often unsettling question: How can an organization definitively ascertain if a breach has occurred? Would the presence of a stealthy attacker, quietly reconnoitering the environment, be detectable? Or would their presence remain unknown until a catastrophic event, such as data exfiltration or widespread system encryption, irrevocably signals their malicious activity, often when it is already too late to contain the damage?
In a threat landscape where identity has emerged as the primary attack surface, organizations aspiring to mount an effective defense must elevate Identity Security to a central position within their strategic planning. The era of merely mitigating risk and hoping for the best is definitively over. Identity Threat Detection and Response (ITDR) transcends traditional preventative paradigms by providing the deep, real-time visibility necessary to monitor, understand, and respond to unfolding events within the IT environment precisely when it matters most, shifting the organizational stance from reactive to truly proactive.
The Strategic Imperative of Identity Intelligence: Knowing Your User, Unmasking the Adversary

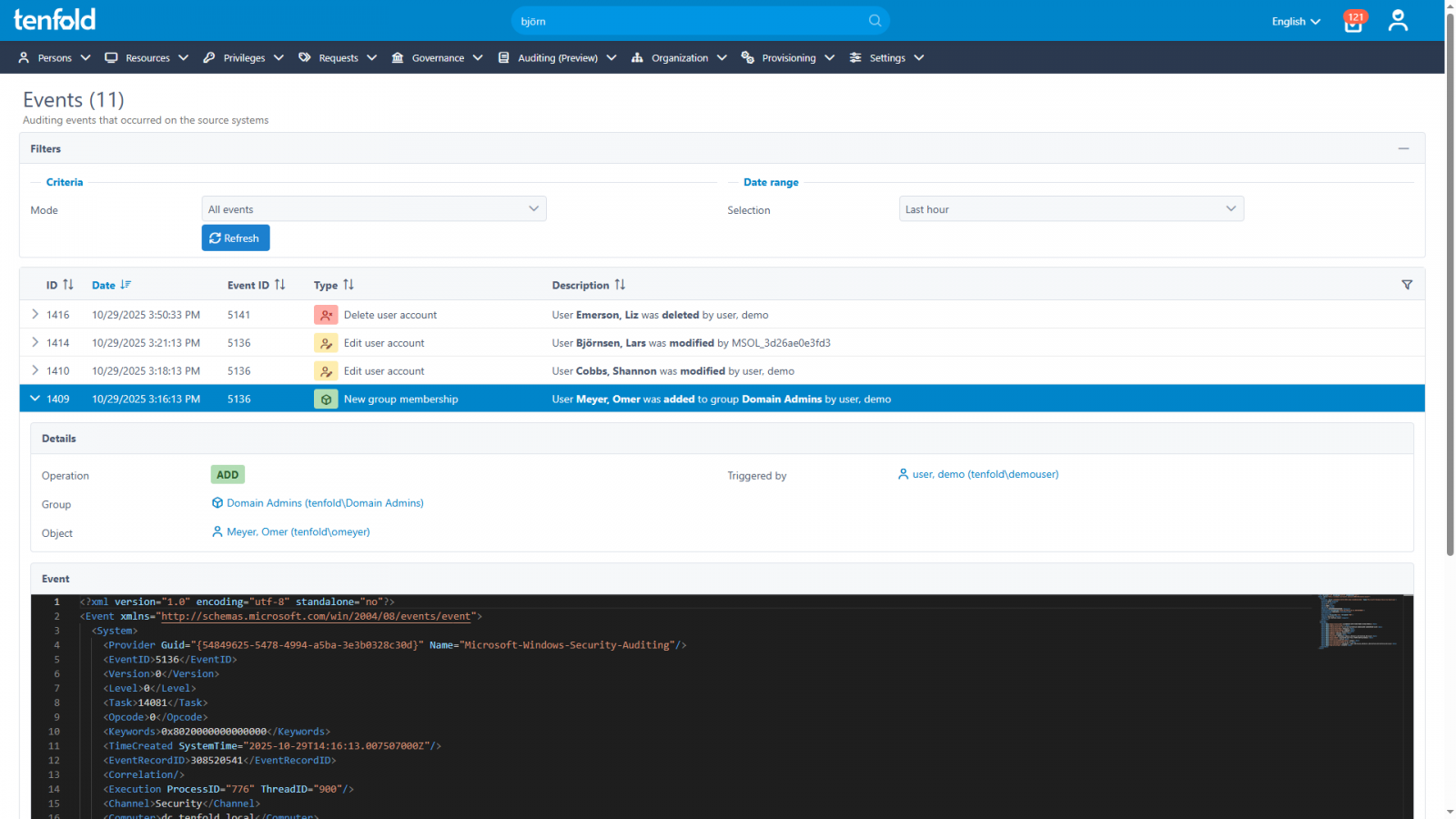
The core strength of ITDR lies in its ability to systematically log, aggregate, and meticulously analyze events across all connected systems, furnishing up-to-the-minute intelligence on the precise activities occurring within an IT ecosystem. This encompasses understanding legitimate user behavior – what users are doing, when new accounts are provisioned, or when critical security group memberships are altered. By establishing a robust baseline of normal operational patterns, ITDR solutions leverage sophisticated filters, real-time alerts, and advanced behavioral analytics to discern anomalous or suspicious activity with high fidelity, enabling security teams to respond to emergent threats with unparalleled speed and precision.
The more thoroughly an organization comprehends the typical behavior of its users, the more readily it can pinpoint deviations indicative of malicious intent. For example, most employees adhere to predictable work hours, access a confined set of applications, folders, and network resources directly relevant to their assigned projects. Any significant departure from these established patterns warrants immediate scrutiny. Conversely, certain IT events serve as immediate red flags that demand prompt investigation by security personnel:
- Unusual Login Geographies or Times: A user logging in from an atypical geographic location, especially one far removed from their normal operational area, or attempting access outside standard business hours, particularly late at night or on weekends, strongly suggests a compromised account.
- Rapid Privilege Escalation: An account suddenly requesting or being granted elevated administrative privileges without proper authorization or established workflow is a critical indicator of an attacker attempting to expand their access.
- Access to Unrelated or Sensitive Resources: A user accessing files, databases, or systems that are entirely outside their usual scope of work or contain highly sensitive information they typically do not handle.
- Bulk Data Downloads or Transfers: Unexpectedly large volumes of data being downloaded, copied, or transferred to external services or unusual internal destinations.
- Account Lockouts or Failed Login Attempts: A surge in failed login attempts for a specific account, particularly if originating from multiple IP addresses, could indicate a brute-force attack.
- Changes to Critical System Configurations or Security Groups: Unauthorized modifications to system settings, security group memberships, or access control lists (ACLs) are often a precursor to broader compromise.
- Anomalous Application Usage: A user attempting to launch or interact with applications they typically do not use, especially security tools or system utilities, in an unusual manner.
Even in scenarios where an unusual pattern of IT activity might ultimately have an innocuous explanation, the awareness and capacity to investigate these events are invaluable. It empowers IT teams to proactively validate the nature of the activity, decisively rule out an account breach, or identify an insider threat. In the realm of suspicious behavioral patterns, the guiding principle must always be "better safe than sorry," prioritizing investigation to safeguard the organizational infrastructure.
Converged Identity Management: Governance and Event Auditing in a Unified Platform
For organizations seeking to elevate their Identity Security strategy in 2026, the consolidation of identity governance and security functions within a single, integrated platform offers significant operational and strategic advantages. The fragmentation of identity management tools often leads to gaps in visibility, increased operational complexity, and higher total cost of ownership. A unified solution addresses these challenges by providing a holistic view of user identities, their entitlements, and their activities.
Such a platform seamlessly integrates Identity Governance (IGA) with Identity Threat Detection and Response (ITDR). IGA capabilities encompass robust role-based access control, ensuring that access rights are systematically assigned and managed based on job function, thereby minimizing over-privileging. It includes comprehensive identity lifecycle automation, streamlining the provisioning and de-provisioning of accounts as employees join, change roles, or depart, thereby eliminating dormant accounts that attackers can exploit. Regular, automated access reviews for shared content and critical systems ensure that entitlements remain appropriate and compliant, reducing the attack surface.
When combined with advanced logging and event auditing features, this integrated platform transforms into a powerful security nexus. It allows organizations to move beyond mere access management to actively monitor and analyze every identity-related event. This convergence means that with a single subscription, an organization can:
- Implement and Enforce Robust Identity Governance: Establish clear policies for access, automate user lifecycle processes, and conduct regular audits to ensure compliance and reduce unnecessary privileges.
- Gain Real-time Visibility into User Activities: Monitor who is accessing what, from where, and when, across the entire IT environment, providing the raw data for threat detection.
- Detect and Respond to Anomalous Behaviors: Leverage behavioral analytics to identify deviations from normal user patterns, signaling potential compromises or insider threats.
- Streamline Compliance and Auditing: Maintain comprehensive audit trails for regulatory requirements and internal governance, simplifying the process of demonstrating adherence to security policies.
- Reduce Operational Overhead and Complexity: Manage identities and security from a single pane of glass, reducing the need for multiple disparate tools and the associated integration challenges.
The adoption of user-friendly, no-code platforms significantly lowers the barrier to entry for implementing sophisticated Identity Threat Detection capabilities. Designed for rapid deployment and intuitive operation, these solutions empower security teams to quickly establish a robust identity security posture. By closing the loop between streamlined identity onboarding, continuous governance, and real-time event auditing, organizations can govern their digital identities with unprecedented confidence. This holistic approach ensures that identities, once a primary vulnerability, become a fortified element of the cybersecurity defense, safeguarding critical assets against the advanced threats of 2026 and beyond.
Conclusion
The strategic landscape of cybersecurity has irrevocably shifted, placing user identities at the forefront of both organizational operations and adversary targets. In this new paradigm, traditional perimeter defenses, while necessary, are insufficient without the deep, real-time intelligence afforded by Identity Threat Detection and Response. For organizations aiming to cultivate a truly resilient digital frontier in 2026, integrating ITDR into the core of their security strategy is not merely an enhancement but an existential imperative. By understanding the intricate dance of legitimate user behavior and meticulously scrutinizing deviations, enterprises can proactively identify, mitigate, and neutralize identity-based threats, transforming potential vulnerabilities into an unyielding defense. The future of enterprise security hinges on this fundamental reorientation, empowering organizations to operate with confidence in an increasingly complex and hostile digital world.