A recent sophisticated cyber espionage operation, active between October and December 2025, has strategically targeted high-ranking personnel within Ukraine’s defense apparatus, deploying advanced backdoor malware disguised as legitimate charitable initiatives. This campaign, meticulously detailed by Ukraine’s Computer Emergency Response Team (CERT-UA), highlights the persistent and evolving threat landscape facing critical national security entities in regions of geopolitical conflict. The attackers leveraged a novel malware variant, dubbed PluggyApe, employing intricate social engineering tactics to infiltrate the digital infrastructure of key Ukrainian defense personnel.
The forensic analysis conducted by CERT-UA points with medium confidence towards ‘Void Blizzard,’ also recognized as ‘Laundry Bear,’ a Russian state-sponsored threat group. This attribution underscores the ongoing cyber warfare dimensions intertwined with conventional conflict, where intelligence gathering through digital means plays a pivotal role. Void Blizzard has a documented history of targeting entities aligned with Russian strategic interests, particularly within NATO member states, with a primary objective of exfiltrating sensitive files and communications. Notably, this group was previously implicated in a significant breach of Dutch police internal systems in 2024, resulting in the theft of confidential information pertaining to law enforcement officers, demonstrating their capacity for high-impact intelligence operations against Western targets.
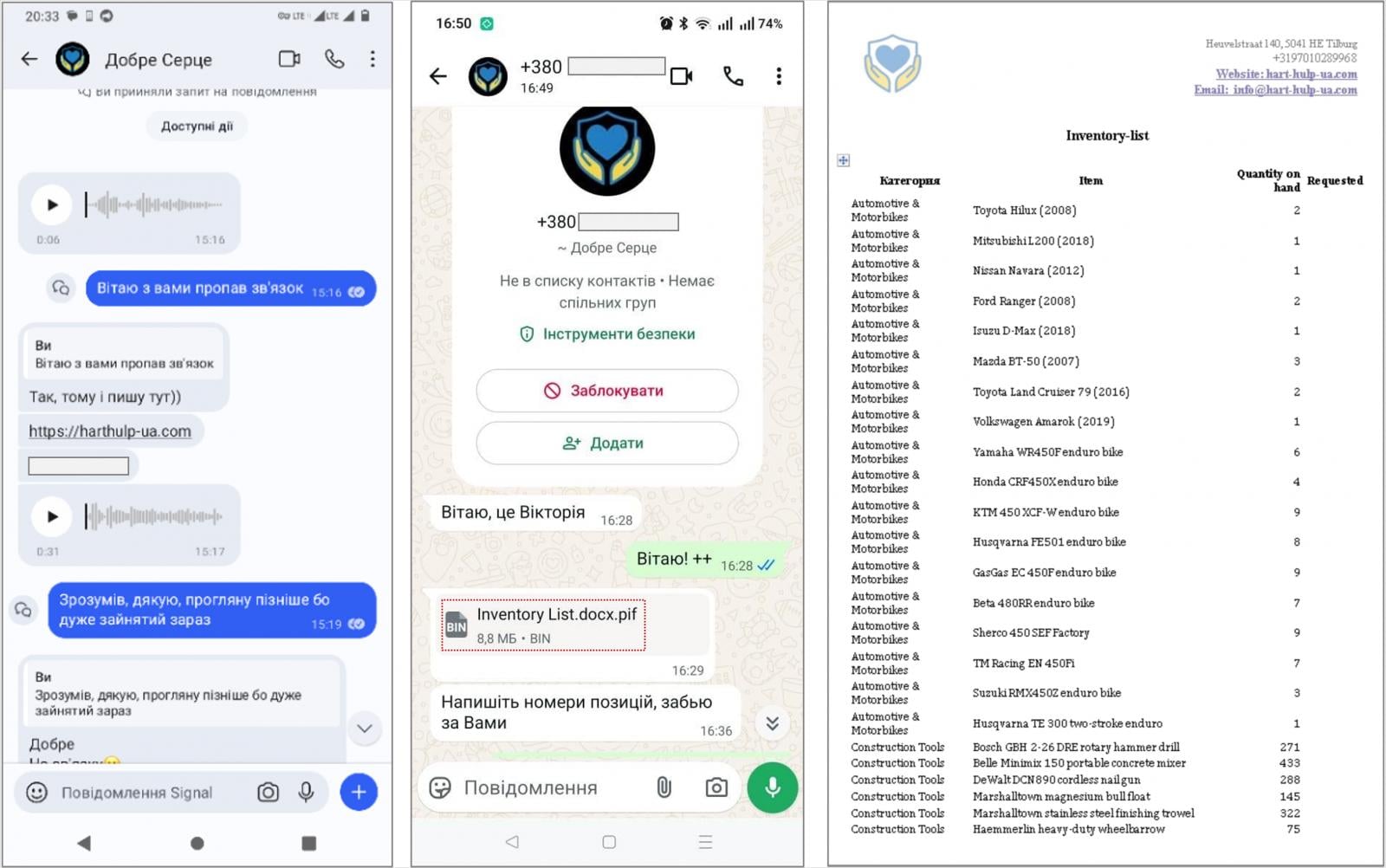
The modus operandi of this particular campaign against Ukrainian defense officials showcases a refined approach to initial compromise and malware delivery. The attack chain typically commenced with highly personalized instant messages disseminated via popular communication platforms such as Signal or WhatsApp. These messages were meticulously crafted to appear urgent and legitimate, directing recipients to visit ostensibly benevolent websites purportedly affiliated with charitable foundations. The charitable theme was a calculated deception, designed to exploit empathy and a sense of duty, thereby lowering the target’s natural suspicion.

Upon navigating to these deceptive web portals, targets were instructed to download a password-protected archive, which the attackers claimed contained documents of significant interest or importance, often related to humanitarian aid or military support. This stage of the attack is critical, as it manipulates the target into willingly executing the malicious payload. Instead of benign documents, these archives concealed executable PIF (Program Information File) files, cleverly disguised with double extensions such as .docx.pif, intended to mimic legitimate document formats. In some instances, the PluggyApe payloads were directly transmitted through the messaging applications themselves, bypassing the need for a fake website and accelerating the infection process.
The choice of PIF files as a loader represents an adaptation in the threat actor’s toolkit. Earlier iterations of PluggyApe deployment, prior to December 2025, reportedly utilized .pdf.exe extensions for their loaders. The shift to PIF files, which are essentially executable programs often associated with older MS-DOS programs but still recognized by Windows, exploits a user’s potential unfamiliarity with less common file extensions or misinterpretation of file icons. The malicious PIF file itself was engineered using PyInstaller, an open-source utility that bundles Python applications and all their necessary dependencies into a single executable package. This technique allows threat actors to leverage the versatility of Python for their malware development while ensuring portability across target systems without requiring a Python environment.
PluggyApe functions as a robust backdoor, designed for persistent access and intelligence gathering. Upon successful execution, the malware initiates a comprehensive profiling of the compromised host, collecting vital system information. This data, which includes a unique victim identifier, is then exfiltrated to the attackers’ command-and-control (C2) infrastructure. Following the initial reconnaissance, PluggyApe establishes persistence on the system, primarily through modifications to the Windows Registry, ensuring that it automatically launches upon system startup and maintains its foothold even after reboots. Once persistent, the backdoor lies dormant, awaiting further instructions or code execution commands from the threat actors, effectively turning the compromised system into a remote surveillance and access point.

The evolution of PluggyApe between its initial sightings and December 2025 indicates a concerted effort by Void Blizzard to enhance its capabilities and evade detection. PluggyApe version 2, observed in later attacks, introduced significant improvements, including superior obfuscation techniques to complicate reverse engineering and analysis. A notable architectural change was the adoption of MQTT (Message Queuing Telemetry Transport) for its communication protocol. MQTT, a lightweight messaging protocol popular in IoT and constrained environments, offers a stealthier and potentially more resilient communication channel compared to traditional HTTP-based C2, making it harder to detect and block. Furthermore, PluggyApe v2 incorporated additional anti-analysis checks, designed to identify and thwart attempts by security researchers to scrutinize its functionality in sandboxed environments.
A particularly sophisticated aspect of PluggyApe’s operation is its dynamic command-and-control (C2) address fetching mechanism. Rather than relying on less flexible hardcoded C2 entries, which can be quickly blacklisted once discovered, PluggyApe retrieves its C2 addresses from external, seemingly innocuous sources such as rentry.co and pastebin.com. These public code-sharing and text-hosting platforms are used by the attackers to publish base64-encoded strings that contain the current C2 server details. This method provides Void Blizzard with significant flexibility, allowing them to rapidly update C2 infrastructure, switch to new servers, and maintain resilience against takedowns, as the malware itself does not need to be updated to reflect C2 changes.
CERT-UA’s analysis also underscores a critical vulnerability increasingly exploited by state-sponsored actors: mobile devices. The agency warns that smartphones and tablets have become prime targets due to their often-lower security posture compared to traditional desktop systems, coupled with less rigorous monitoring by organizational security teams. When these inherent vulnerabilities are combined with sophisticated attack preparation, such as the use of compromised accounts, legitimate phone numbers from Ukrainian telecommunication operators, and highly personalized communication in the local language, the efficacy of these social engineering attacks dramatically increases.
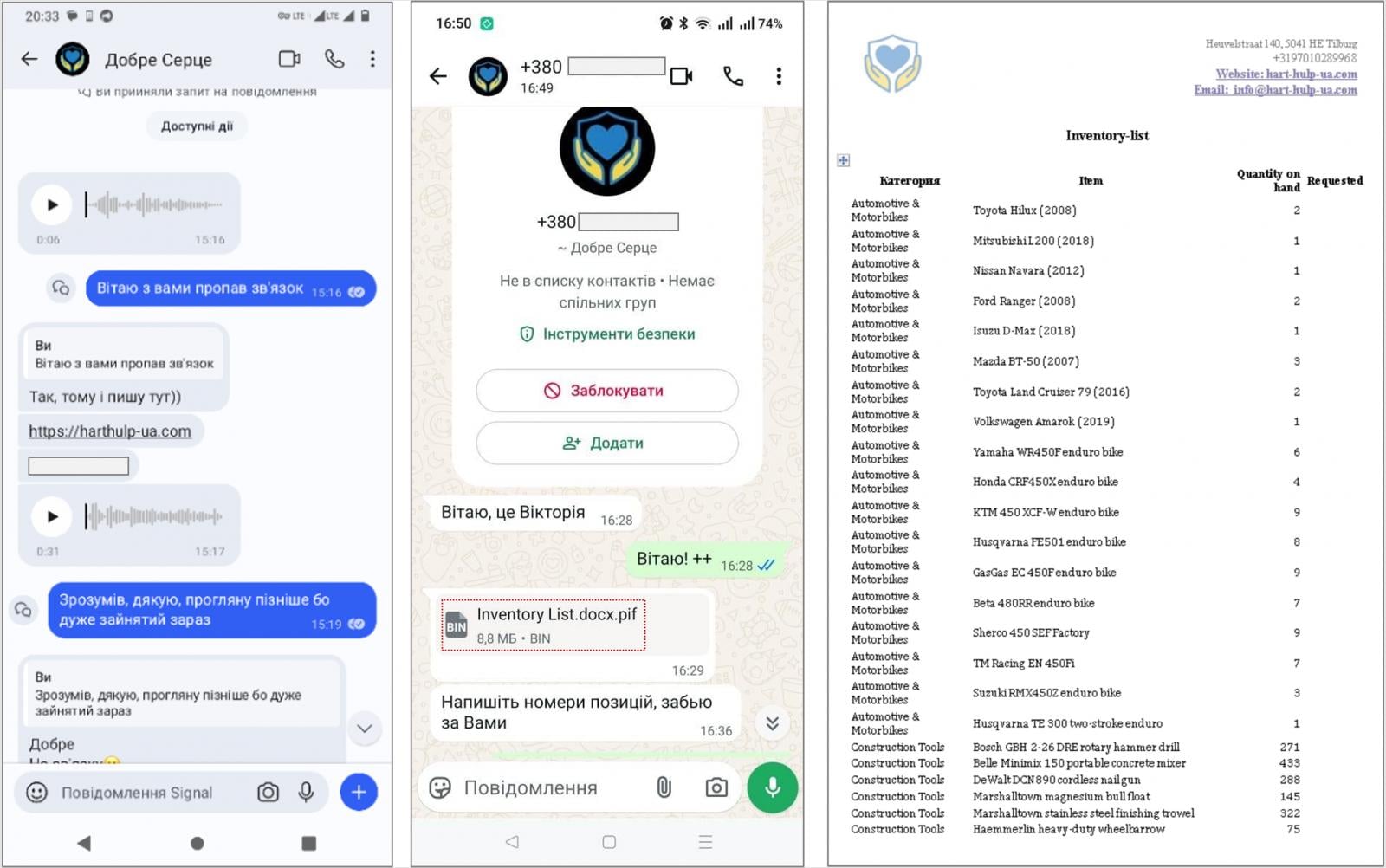
The level of detail and personalization in these campaigns is alarming. As CERT-UA articulates, initial interactions with targets are increasingly conducted using legitimate accounts and phone numbers, often incorporating audio and video communication to build trust and authenticity. Attackers demonstrate a profound and relevant understanding of the individual target, their organization, and the specifics of its operations. This deep contextual knowledge, likely gleaned from prior intelligence gathering or compromised networks, makes the deceptive lures incredibly convincing and difficult to discern from legitimate communications, even for security-aware individuals. Such tailored attacks highlight the significant resources and strategic planning invested by state-sponsored groups like Void Blizzard.
The implications of such sophisticated cyber espionage campaigns are far-reaching. For Ukraine’s defense forces, successful compromises can lead to the exfiltration of critical operational plans, intelligence assessments, sensitive communications, and personal data of military personnel, severely impacting national security and operational effectiveness. Beyond the immediate operational risks, these attacks erode trust in digital communication channels and place an immense burden on cybersecurity defenders to continuously adapt to evolving threats. The targeting of defense officials through personal devices and messaging apps also blurs the lines between professional and personal digital security, emphasizing the need for comprehensive security awareness training that extends beyond traditional corporate perimeters.
To counter these persistent threats, a multi-layered defense strategy is imperative. This includes robust endpoint detection and response (EDR) solutions, advanced threat intelligence sharing among national and international partners, and continuous vulnerability management. Crucially, enhancing human resilience through extensive cybersecurity awareness training is paramount. Personnel, particularly those in sensitive roles, must be educated on recognizing sophisticated social engineering attempts, verifying the legitimacy of unsolicited communications, and exercising extreme caution before opening attachments or clicking links, even if they appear to originate from trusted sources. Implementing multi-factor authentication (MFA) across all accounts, maintaining up-to-date software, and segmenting networks can further mitigate the impact of successful breaches.
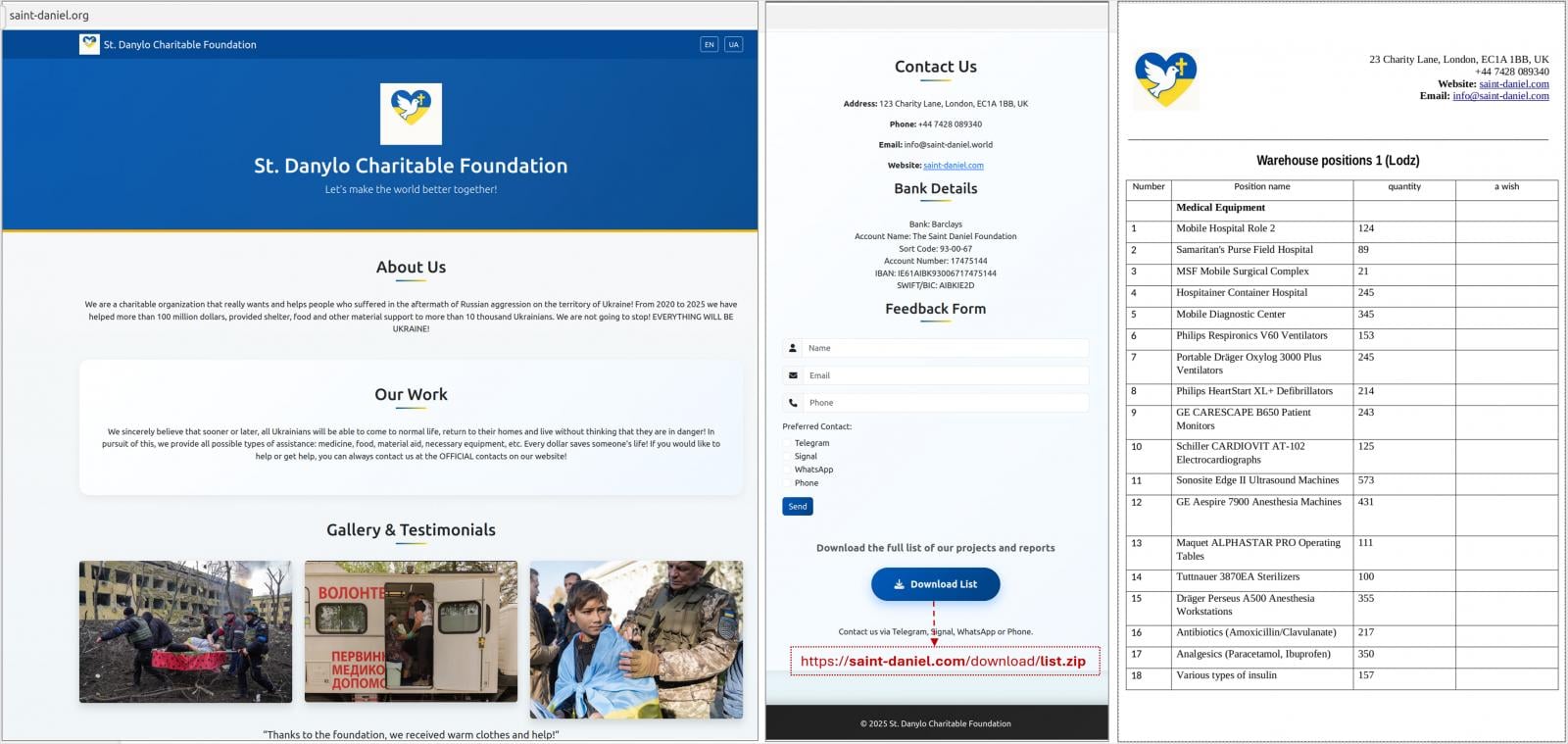
The detailed indicators of compromise (IoCs), including the deceptive websites posing as charity portals, provided in CERT-UA’s comprehensive report, are invaluable for defensive operations. These IoCs allow security teams to proactively block malicious infrastructure, detect existing compromises, and strengthen their defenses against similar future attacks. As the geopolitical landscape remains volatile, the cyber front will undoubtedly continue to be a critical domain, demanding constant vigilance and innovation in cybersecurity defenses to protect national interests and critical infrastructure from state-sponsored aggression.







