
Spain’s preeminent energy provider, Endesa, along with its regulated market operator Energía XXI, has confirmed a substantial cybersecurity incident involving unauthorized access to its commercial systems, leading to the exposure of sensitive customer contract information and personal details, an event now compounded by claims from threat actors offering an extensive database of Endesa customer records for sale on illicit online marketplaces.
A Critical Infrastructure Target Under Siege
Endesa, a colossal entity in the European energy sector and a vital component of Spain’s critical national infrastructure, serves over 10 million customers across Spain and Portugal, with a total client base reportedly encompassing 22 million individuals and businesses. Its strategic importance, coupled with its vast repository of customer data, makes it an attractive target for cyber adversaries. The company’s recent disclosure marks a concerning development in the escalating digital threat landscape faced by essential service providers globally. Owned by the Italian Enel Group, Endesa’s operational footprint and data holdings are immense, underscoring the gravity of any compromise to its digital architecture.
The breach was detected following evidence of illicit access to Endesa’s commercial platform. In response, both Endesa and Energía XXI have initiated notifications to affected customers, signaling a commitment to transparency in the wake of the intrusion. The notifications explicitly state that despite robust security measures, unauthorized entry resulted in the compromise of personal data linked to energy contracts. This includes, but is not limited to, a range of personally identifiable information (PII) crucial for identity verification and service management.
Scope of Compromise and Immediate Corporate Response
According to the ongoing internal investigation, the compromised data encompasses a variety of critical customer details. While the precise categories were not exhaustively listed in the initial public statements, the nature of contract-related information typically includes names, addresses, contact numbers, national identification numbers, billing details, and service historical data. Crucially, Endesa has affirmed that account passwords were not among the data types accessed, mitigating one vector of immediate risk for customers. This distinction is significant as it prevents direct account takeover attempts solely through stolen credentials from this incident.

Upon discovery of the unauthorized access, Endesa implemented a series of immediate and decisive incident response protocols. These actions included blocking the compromised internal accounts to contain further illicit activity, systematically dumping log records for comprehensive forensic analysis, and initiating the process of direct customer notifications. Furthermore, the company has escalated its monitoring capabilities across its network to detect and thwart any subsequent suspicious behaviors or potential re-entry attempts by the perpetrators.
In adherence to regulatory obligations, particularly under the General Data Protection Regulation (GDPR), Endesa has promptly informed the Spanish Data Protection Agency (AEPD) and other pertinent national authorities. This step is a mandatory requirement for data breaches that pose a risk to individuals’ rights and freedoms, enabling regulatory oversight and guidance throughout the investigative process. The company’s proactive engagement with authorities underscores the seriousness with which it is treating the incident.
The Shadowy Market for Stolen Data
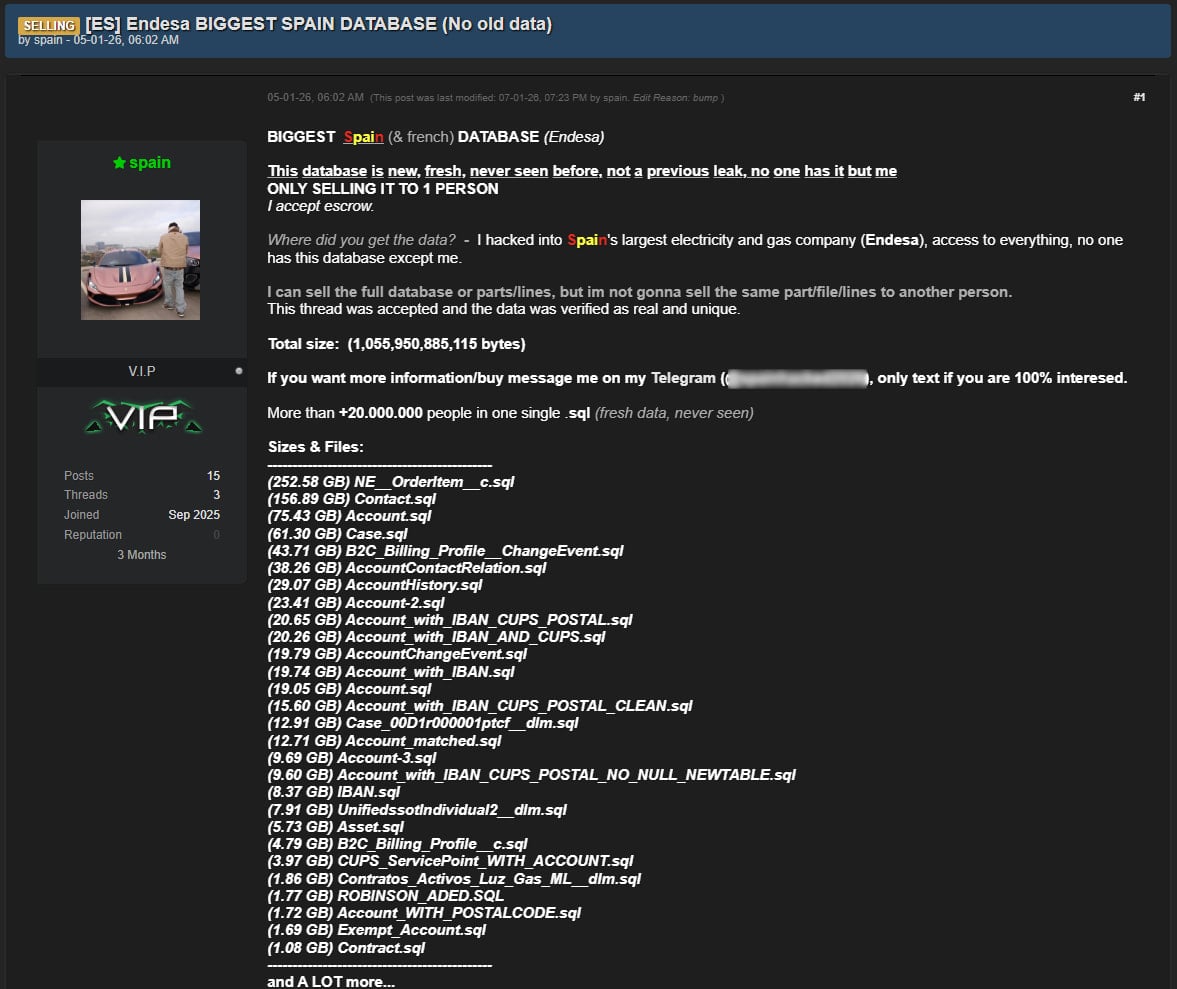
Concurrent with Endesa’s official disclosure, a disconcerting development has emerged on underground cybercrime forums. Threat actors have surfaced, claiming to possess and offering for sale a colossal database purportedly stolen from Endesa. These individuals allege access to approximately 1 terabyte of SQL databases containing detailed information on an estimated 20 million Endesa customers. The sheer volume of data claimed, if accurate, represents a significant portion of Endesa’s entire customer base and points to a deeply impactful breach.
The purported samples of this data, when scrutinized, appear to corroborate the types of information Endesa has acknowledged as being compromised through its internal investigation. This alignment strengthens the credibility of the threat actors’ claims and suggests a direct link between the confirmed breach and the data being peddled online. The offering specifies a preference for a "single exclusive buyer," a common tactic in the dark web to maximize profit and prevent rapid devaluation of the data through widespread distribution. This exclusivity also hints at the perceived high value of this particular dataset.
Implications for Customers and Broader Industry Concerns

Despite Endesa’s assertion that, as of the current reporting, there is no evidence of fraudulent use of the affected data, the risk remains tangible and significant. The company has appropriately advised recipients of its notification letters to maintain heightened vigilance against potential identity impersonation, sophisticated phishing attacks, and outright data theft. Customers are urged to report any suspicious communications or activities to the dedicated contact channels provided by Endesa.
The exposure of personal details, even without passwords, creates fertile ground for targeted social engineering campaigns. Threat actors can leverage stolen names, addresses, and contract specifics to craft highly convincing phishing emails or phone calls, designed to trick individuals into divulging further sensitive information, installing malware, or authorizing fraudulent transactions. For an energy provider, data such as billing history or service addresses could be exploited to initiate fraudulent service changes or even physical access attempts to properties.
This incident is not an isolated event but rather indicative of a disturbing trend where critical infrastructure providers, including energy companies, are increasingly targeted. The motives are diverse, ranging from financial gain through data monetization to industrial espionage, or even state-sponsored disruption. The energy sector, being fundamental to national security and economic stability, presents high-value targets for sophisticated cyber adversaries.
Expert Analysis and Future Outlook
The Endesa breach underscores several critical vulnerabilities inherent in managing vast digital estates. Large organizations with extensive customer bases and complex IT infrastructures often present a broader attack surface. Legacy systems, third-party integrations, and human factors can all introduce points of weakness that well-resourced attackers are adept at exploiting.
From an analytical perspective, the alleged sale of such a large dataset suggests a financially motivated attack, likely by organized cybercriminal groups. The demand for comprehensive customer records remains high on illicit markets, as this data forms the bedrock for various downstream criminal activities, including targeted fraud, identity theft, and further extortion.
The incident will undoubtedly prompt a rigorous review of Endesa’s entire cybersecurity posture. This includes, but is not limited to, strengthening access controls, enhancing endpoint detection and response (EDR) capabilities, implementing advanced threat intelligence feeds, and refining incident response plans. A shift towards zero-trust architectures, where no user or device is inherently trusted regardless of their location, will become increasingly imperative for critical infrastructure operators. Furthermore, continuous security auditing, employee training on phishing awareness, and multi-factor authentication for all critical systems and customer interactions are essential preventative measures.
Regulatory bodies, like the AEPD, will closely monitor Endesa’s compliance with data protection laws and the effectiveness of its remediation efforts. Non-compliance with GDPR, particularly concerning data security and timely breach notification, can result in substantial financial penalties, impacting not only the company’s bottom line but also its reputation and customer trust.
In conclusion, the Endesa data breach serves as a stark reminder of the persistent and evolving cyber threats confronting critical infrastructure and large enterprises. While the immediate focus is on containment and customer protection, the long-term implications will necessitate a fundamental re-evaluation and hardening of digital defenses across the energy sector to safeguard both operational integrity and the privacy of millions of customers. The ongoing investigation and subsequent actions taken by Endesa will be closely watched by regulators, cybersecurity experts, and, most importantly, its extensive customer base.







