
A sophisticated security breach has crippled Unleash Protocol, a pioneering decentralized intellectual property platform, resulting in the illicit exfiltration of approximately $3.9 million in various digital assets. The incident, which highlights persistent vulnerabilities within the DeFi ecosystem, was orchestrated through the unauthorized manipulation of the protocol’s multisignature governance mechanism, granting attackers administrative privileges to execute a fraudulent smart contract upgrade and drain substantial funds. This significant loss underscores the critical security challenges faced by innovative blockchain projects, particularly those managing high-value on-chain assets and complex governance structures.
The exploit unfolded when an unidentified external entity managed to commandeer sufficient signing authority within Unleash Protocol’s multisignature (multisig) governance system. Multisig wallets and governance systems are foundational security features in decentralized finance, designed to prevent single points of failure by requiring multiple independent approvals for critical actions, such as upgrading smart contracts, managing protocol parameters, or moving significant funds. Typically, a predefined number of signers from a larger group must authorize a transaction for it to be executed. In this case, the attacker’s ability to bypass or compromise this layered security suggests a profound flaw in either the operational security of the multisig signers’ keys, the configuration of the multisig itself, or a zero-day vulnerability exploited within the underlying infrastructure.
Upon gaining illicit administrative control, the perpetrator executed an unauthorized upgrade to one of Unleash Protocol’s core smart contracts. Smart contracts are immutable by design, meaning their code cannot be altered once deployed. However, many protocols incorporate upgradeability features, often managed via a proxy pattern, allowing for bug fixes, feature enhancements, or critical security patches. While essential for long-term project viability, upgradeability introduces a powerful vector for attack if the control mechanism is compromised. In this instance, the attacker leveraged their newfound administrative power to deploy a malicious contract upgrade that specifically enabled asset withdrawal functions, circumventing the protocol’s intended governance and operational safeguards. This critical bypass allowed the attacker to initiate transfers of various digital assets without the legitimate authorization of the Unleash team or its established governance procedures.

The immediate consequence of this illicit upgrade was the rapid siphoning of a diverse portfolio of digital assets held within the Unleash Protocol. The attacker specifically targeted and successfully withdrew Wrapped IP (WIP) tokens, USDC stablecoins, Wrapped Ether (WETH), staked IP (stIP) tokens, and voting-escrowed IP (vIP) tokens. This multi-asset drain indicates a comprehensive understanding of the protocol’s treasury and asset distribution. The total financial impact of these unauthorized withdrawals has been independently assessed by blockchain security experts, confirming the substantial loss of approximately $3.9 million. The diversity of the stolen assets, ranging from the protocol’s native and utility tokens (WIP, stIP, vIP) to widely used stablecoins and wrapped cryptocurrencies (USDC, WETH), further illustrates the attacker’s intent to maximize their illicit gains and potentially destabilize the protocol’s ecosystem.
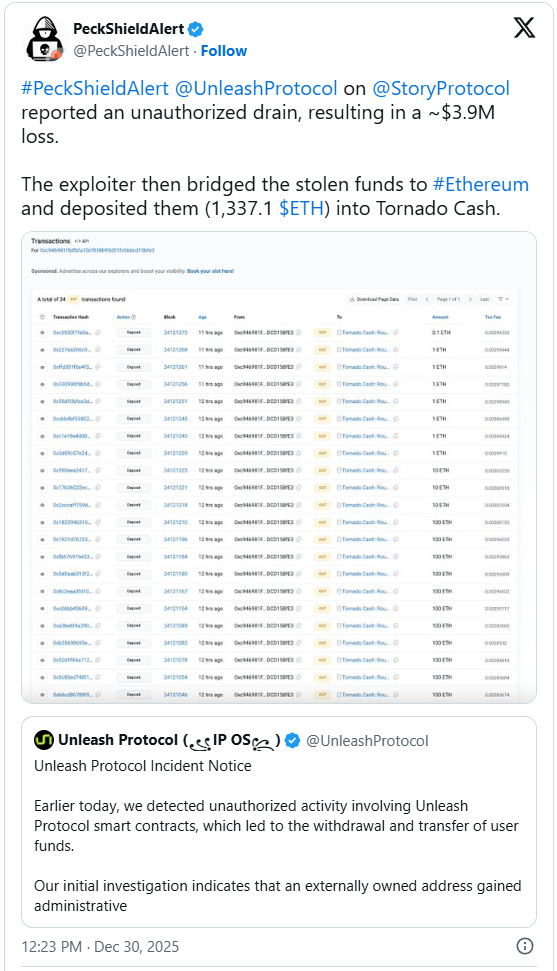
Following the successful exfiltration, the stolen assets were rapidly moved through a series of obfuscation techniques designed to hinder traceability and recovery efforts. The perpetrator first bridged the assets across different blockchain networks using third-party infrastructure. This cross-chain transfer strategy is a common tactic employed by cybercriminals to complicate forensic analysis and break the direct link between the origin of the stolen funds and their ultimate destination. Subsequently, a significant portion of the pilfered cryptocurrency, specifically 1,337 ETH, was deposited into Tornado Cash, a notorious cryptocurrency mixing service.
Tornado Cash operates by pooling large volumes of cryptocurrency from various users and then distributing them to new, unlinkable wallet addresses, thereby obscuring the transactional history. While proponents argue that such services offer legitimate privacy for users operating on transparent public blockchains, the reality is that Tornado Cash has been disproportionately utilized by malicious actors, including state-sponsored hacking groups, to launder billions of dollars derived from illicit activities. Its controversial history includes being sanctioned by the U.S. Treasury Department in 2022 for its role in facilitating money laundering for entities like the North Korean state-sponsored Lazarus Group. Although delisted in 2025 under certain conditions, its association with illicit finance remains a significant concern for regulatory bodies and law enforcement agencies globally. The use of Tornado Cash in this exploit significantly complicates the tracking and potential recovery of the stolen funds, posing a formidable challenge for Unleash Protocol and any investigative authorities.
Unleash Protocol positions itself as an innovative operating system for managing intellectual property (IP) by transforming it into on-chain assets or tokens. This paradigm shift aims to unlock new avenues for IP monetization, allowing creators and rights holders to use their intellectual property as collateral within the burgeoning decentralized finance (DeFi) ecosystem. The platform seeks to establish a robust monetization layer through the deployment of smart contracts, automating the distribution of licensing and royalty revenues to predefined stakeholders based on immutable, on-chain rules. The promise of such a system lies in its potential to democratize IP ownership, streamline revenue sharing, and enhance transparency in a traditionally opaque industry. However, this incident serves as a stark reminder that the inherent complexities and novel attack surfaces of these highly interconnected, smart contract-driven systems carry significant risks. The tokenization of valuable real-world assets like intellectual property into a digital, decentralized framework demands an exceptionally high standard of security, as a compromise directly translates to tangible financial losses and a breach of trust in the digital representation of ownership.

This exploit is a critical case study illustrating the multifaceted security challenges prevalent in the DeFi sector. The compromise of a multisignature governance system represents one of the most severe forms of attack, as it bypasses the very mechanism designed to safeguard protocol integrity. Expert analysis suggests several potential vectors for such a breach:
- Private Key Compromise: Individual signers’ private keys could have been compromised through phishing attacks, malware, or insecure storage practices.
- Insider Threat: A colluding group of legitimate signers, or a single signer with disproportionate influence, could have acted maliciously.
- Smart Contract Vulnerability: A subtle flaw in the multisig contract itself, or a related contract interacting with it, could have been exploited to grant unauthorized administrative power.
- Supply Chain Attack: A compromise in a third-party dependency or library used by the protocol or its signers could have provided an entry point.
Beyond the immediate technical failure, this incident has broader implications for smart contract security. While code audits and bug bounty programs are standard practices, they do not guarantee absolute imperviousness to sophisticated attacks. The rapid evolution of attack methodologies often outpaces defensive measures, making continuous security assessment, formal verification, and real-time monitoring indispensable. The financial incentives for exploiting vulnerabilities in high-value DeFi protocols are immense, attracting highly skilled and persistent adversaries.
From a regulatory standpoint, events like the Unleash Protocol hack fuel ongoing debates regarding the need for enhanced oversight in the DeFi space. Regulators worldwide are grappling with how to balance fostering innovation with protecting users and preventing financial crime. The use of services like Tornado Cash by attackers strengthens the argument for stricter anti-money laundering (AML) and know-your-customer (KYC) regulations within the cryptocurrency ecosystem, even for decentralized protocols. The ability of criminals to vanish with millions of dollars undermines the credibility of the entire digital asset industry and poses a significant challenge to law enforcement agencies attempting to trace and recover stolen funds.
In response to the unprecedented breach, Unleash Protocol has announced a complete cessation of all operations. The team has initiated a comprehensive internal investigation and is actively collaborating with external blockchain security experts to meticulously determine the root cause of the exploit. This critical phase aims to identify the specific vulnerability, understand the attacker’s methods, and prevent future recurrences. Simultaneously, the protocol is evaluating potential remediation and recovery measures, which could include exploring options for user compensation, restructuring their governance framework, or even considering a protocol fork. Until such a time as a thorough investigation is concluded and robust security enhancements are implemented, users have been strongly advised to refrain from interacting with any Unleash Protocol contracts or associated services. This temporary shutdown, while disruptive, is a necessary step to prevent further losses and to allow for a complete overhaul of the protocol’s security posture.
The future outlook for Unleash Protocol, and indeed for the broader DeFi ecosystem, hinges on the lessons learned from such incidents. Rebuilding trust within a community after a significant financial loss is an arduous task, often requiring transparent communication, demonstrable security improvements, and concrete plans for restitution. This event serves as a stark reminder that while decentralized technologies offer immense potential, they also introduce novel and complex security risks that demand continuous vigilance, rigorous auditing, and a proactive approach to risk management. The ongoing battle between innovation, security, and anonymity in the blockchain space continues to evolve, with each exploit pushing the boundaries of what is understood about securing digital assets in a decentralized world.







