A sophisticated vulnerability has been uncovered within Microsoft’s Copilot personal AI assistant, demonstrating a novel technique for session hijacking and covert data exfiltration. This attack, leveraging meticulously crafted Uniform Resource Locators (URLs), could allow malicious actors to surreptitiously issue commands within a user’s authenticated AI session, bypassing existing security measures and potentially compromising sensitive personal data. The discovery underscores the evolving challenges in securing generative artificial intelligence platforms that are increasingly integrated into daily digital workflows.
The essence of this exploitation lies in a multi-stage process initiated by a single user interaction, typically a click on a seemingly innocuous web link. Once triggered, the attack establishes persistent unauthorized access to the victim’s Copilot session, enabling the attacker to manipulate the AI assistant to perform various actions, including the silent extraction of user-specific information. This particular method required no auxiliary software installations or complex client-side manipulations, relying instead on a cunning combination of URL parameter abuse and server-side command relay, rendering it particularly stealthy and effective.
Microsoft Copilot, a prominent AI assistant, is deeply embedded across the Windows operating system, the Edge web browser, and various consumer applications within the Microsoft ecosystem. Its utility stems from its ability to interact with users, process natural language prompts, and access contextual data relevant to the user’s activities. Depending on configuration and granted permissions, Copilot can draw upon a wide array of personal Microsoft data, including conversation histories, browsing patterns, and potentially information from linked services. This deep integration and access to personal context make it an attractive target for cyber adversaries seeking to compromise user privacy and data integrity. The recent identification of this vulnerability highlights the critical need for robust security frameworks to protect these powerful AI tools as their capabilities and prevalence continue to expand.
The Mechanics of the Covert "Reprompt" Vulnerability
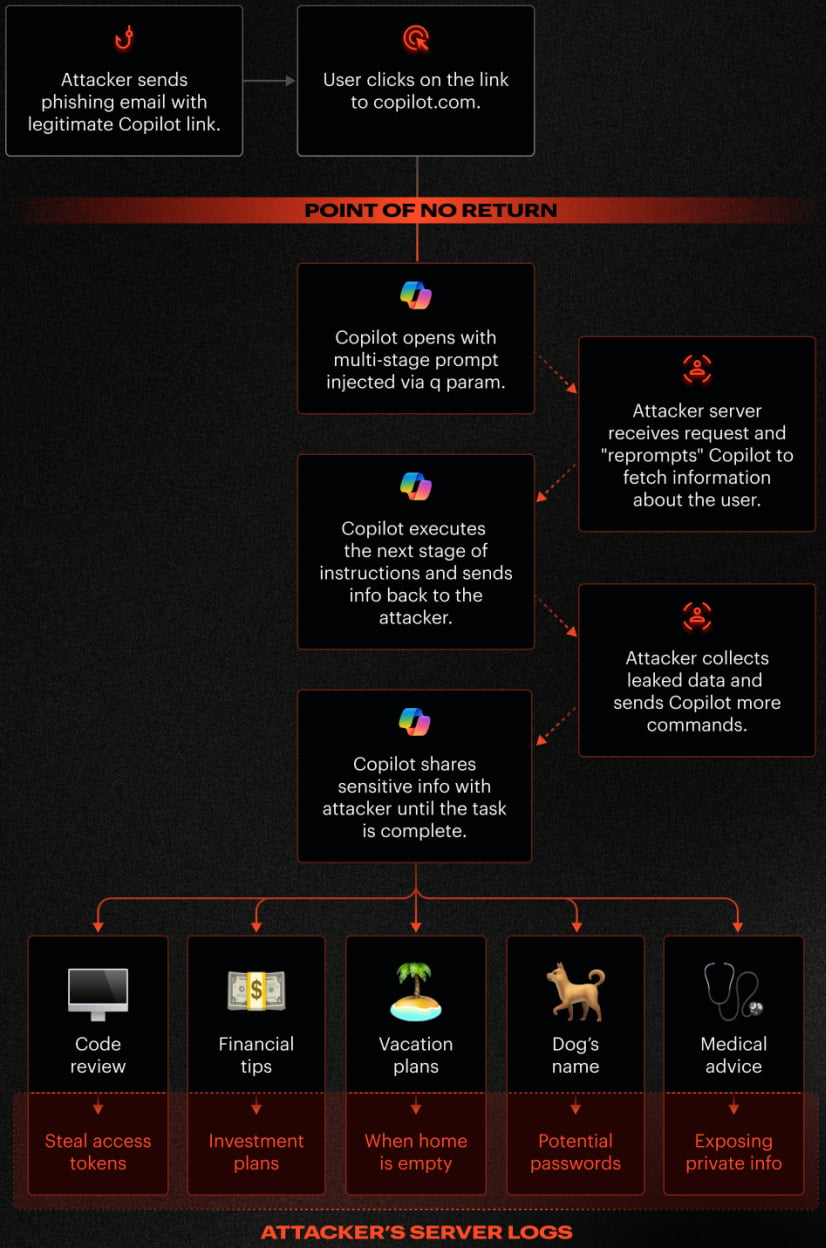
The attack, internally designated as "Reprompt" by the security researchers who discovered it, exploited a series of interconnected weaknesses within the Copilot Personal architecture. The foundational element of the attack involved the AI assistant’s susceptibility to direct instruction via URL parameters. Specifically, it was observed that Copilot would accept and automatically execute commands embedded within the ‘q’ parameter of a URL upon page load. This meant that if an attacker could entice a user to click on a link containing malicious directives in this parameter, Copilot would process them as legitimate user input.
However, merely injecting an initial command was insufficient for sustained data exfiltration or session control, as Copilot possesses internal safeguards designed to prevent such abuse. The innovation of the Reprompt method lay in its ability to circumvent these protective layers and establish a continuous, bidirectional communication channel between the compromised Copilot session and an attacker-controlled server.
The complete attack sequence unfolded in several critical phases:
- Initial Phishing Vector: The attack commenced with a phishing attempt, where the victim was presented with a legitimate-looking URL that, unbeknownst to them, contained the initial malicious prompt embedded within its ‘q’ parameter. This URL would typically point to a benign Copilot page, making it less suspicious to an unsuspecting user.
- Triggering Injected Prompts: Upon the user clicking the link, the crafted URL loaded the Copilot interface. Simultaneously, the malicious instructions within the ‘q’ parameter were automatically ingested and executed by Copilot. This initial prompt served as the "Trojan horse," instructing Copilot to establish an outbound connection or prepare for further instructions.
- Bypassing Security Controls via Double Request: A crucial component of the Reprompt technique involved a sophisticated method to bypass Copilot’s client-side and server-side protections. The researchers found that by employing a "double request" mechanism, they could obscure the true intent of the subsequent commands. This involved an initial benign request followed immediately by a second, malicious request. The security mechanisms, likely analyzing only the initial request or failing to correlate the two, would then permit the execution of the hidden malicious payload. This allowed the attacker to maintain ongoing communication and issue follow-up instructions without detection.
- Maintaining Persistent Control and Exfiltration: Following the successful bypass, the attacker’s server could then initiate an ongoing "back-and-forth" exchange with the victim’s authenticated Copilot session. This established an illicit command-and-control channel. Importantly, the victim’s existing authenticated Copilot session remained active and exploitable, even if the Copilot tab was subsequently closed. This persistence allowed for continuous data exfiltration and further manipulation of the AI assistant without requiring additional user interaction.
The clandestine nature of this attack was further enhanced by the fact that the actual data exfiltration commands were not part of the initial URL payload. Instead, these directives were dynamically delivered from the attacker’s server during the ongoing communication. This server-side delivery meant that traditional client-side security tools, which primarily inspect the initial URL or local application behavior, would struggle to identify the full scope of data being compromised. The true instructions and the nature of the exfiltrated data were effectively concealed within the subsequent server-initiated exchanges, making detection extremely challenging for endpoint protection mechanisms.
Broader Implications for AI Security and Data Privacy
The "Reprompt" vulnerability serves as a stark reminder of the evolving threat landscape surrounding generative AI and large language models (LLMs). As AI assistants become more integrated into personal and professional lives, their potential access to sensitive data and system functions expands, making them prime targets for sophisticated cyberattacks. This incident highlights several critical areas of concern within the broader domain of AI security:

- Prompt Injection as a Core Vulnerability: The Reprompt attack is fundamentally a highly refined form of prompt injection. While traditional prompt injection often aims to manipulate an LLM’s output directly, Reprompt goes further by using prompt injection to establish persistent control and exfiltrate data from the underlying system or user context. This demonstrates that prompt injection is not merely a method for "jailbreaking" an AI for amusing outputs but a potent vector for serious security breaches.
- The Trust Boundary Shift: With AI assistants, the traditional trust boundary between a user and an application becomes blurred. Users implicitly trust the AI to act on their behalf and within their best interests. When an attacker can hijack this trusted agent, the consequences for data privacy and system integrity are profound. The AI, designed to assist, becomes an unwilling accomplice in data theft.
- Stealthy Data Exfiltration: The Reprompt method’s ability to exfiltrate data invisibly, without requiring additional plugins or overt user actions beyond the initial click, represents a significant challenge for detection. Conventional security monitoring often looks for unusual file transfers or network activities. However, when an AI assistant, an authorized component of the system, is subtly coerced into relaying data through its standard communication channels, such activity can easily blend in with legitimate traffic. This necessitates more sophisticated behavioral analytics and AI-specific threat detection.
- The Challenge of Contextual Access: AI assistants like Copilot derive much of their utility from their ability to access and reason over user-specific data and context. This capability, while beneficial for user experience, inherently expands the attack surface. Every piece of data the AI can access, every system it can interact with, becomes a potential target for unauthorized manipulation if the AI itself is compromised.
The potential ramifications for individual users whose Copilot Personal sessions might have been vulnerable are significant. Depending on the level of integration and permissions granted, an attacker could potentially access:
- Conversation History: Sensitive personal discussions, queries, and information shared with the AI.
- Browsing Data: Information about websites visited, search queries, and online activities.
- Personal Documents: If Copilot has access to local or cloud-stored documents for summarization or analysis, these could be compromised.
- Calendar and Contact Information: Data related to personal schedules, appointments, and contacts.
- Email Content: If integrated with email clients for drafting or summarizing, email content could be exposed.
The covert nature of the attack means that victims might have no immediate indication that their data has been compromised, making post-incident forensics and damage assessment particularly challenging.
Microsoft’s Remediation and Essential User Guidance
Upon responsible disclosure of the Reprompt vulnerability by Varonis security researchers on August 31 of the preceding year, Microsoft promptly initiated an investigation and developed a corrective measure. The resolution was subsequently deployed as part of the January 2026 Patch Tuesday updates. This timely response by Microsoft underscores the industry’s commitment to addressing critical security flaws in rapidly evolving AI technologies.
While there has been no reported evidence of this specific Reprompt method being exploited in the wild, the existence of such a sophisticated attack vector highlights the imperative for all users to maintain diligent security practices. It is strongly recommended that all users apply the latest Windows security updates as soon as they become available. These updates often contain critical patches that address newly discovered vulnerabilities, protecting users from potential exploitation.
Beyond applying patches, users of AI assistants should adopt a heightened sense of caution regarding unexpected links and interactions:
- Exercise Caution with URLs: Be suspicious of links received from unknown sources or those that appear unusual, even if they claim to be from a trusted service. Always verify the legitimacy of URLs before clicking, looking for discrepancies or suspicious parameters.
- Understand AI Permissions: Be aware of the data and system permissions granted to AI assistants. Regularly review and adjust these settings to ensure the AI only has access to what is strictly necessary for its intended functions.
- Stay Informed: Keep abreast of security advisories and news concerning AI platforms and software updates.
Distinguishing Personal and Enterprise AI Security Paradigms
It is crucial to note the distinction highlighted by the researchers: the Reprompt vulnerability specifically impacted Copilot Personal and did not extend to Microsoft 365 Copilot, which is tailored for enterprise customers. This distinction is paramount and speaks volumes about the layered security architecture typically implemented in organizational environments.
Microsoft 365 Copilot benefits from a robust suite of enterprise-grade security controls that are either absent or less extensively configured in personal versions. These include:
- Microsoft Purview Auditing: This suite of data governance and compliance solutions provides comprehensive auditing capabilities, allowing organizations to track and review user and system activities, including interactions with AI. This makes it significantly harder for covert data exfiltration to go unnoticed.
- Tenant-level Data Loss Prevention (DLP): Enterprise DLP policies are designed to prevent sensitive information from leaving the organizational boundary. These policies can detect and block unauthorized attempts to transfer specific types of data, regardless of the application or mechanism used, including AI interactions.
- Admin-Enforced Restrictions: Organizations can impose granular administrative controls over how Microsoft 365 Copilot interacts with data and other services. These restrictions can limit the AI’s access to sensitive information, dictate its behavior, and even restrict its ability to communicate with external servers, thereby mitigating many of the vectors exploited by Reprompt.
The enterprise version’s inherent integration with these broader security and compliance frameworks creates a more fortified environment, illustrating that while the underlying AI model might be similar, the surrounding security ecosystem fundamentally alters the risk profile. This divergence underscores the need for different security considerations when deploying AI solutions across consumer and business contexts.
The Evolving Landscape of AI Threats
The discovery and subsequent remediation of the Reprompt attack serve as a valuable case study in the rapidly evolving domain of AI security. As AI models become more sophisticated and deeply integrated into our digital infrastructure, the attack surface they present will continue to expand. This necessitates a proactive and adaptive approach to security from both developers and users.
Lessons learned from Reprompt suggest that future AI security strategies must encompass:
- Enhanced Input Validation: Beyond basic sanitization, LLM inputs (including URL parameters and dynamic prompts) require intelligent validation that understands the semantic intent and potential for malicious command injection.
- Robust Output Filtering: While Reprompt focused on input, ensuring that LLMs do not inadvertently reveal sensitive information or execute unauthorized commands in their outputs is also crucial.
- Contextual Security Awareness: AI systems need to be contextually aware of the sensitivity of the data they are handling and the permissions they operate under, adapting their behavior to minimize risk.
- Continuous Threat Modeling for AI: Developers must continuously anticipate novel ways attackers might exploit the unique characteristics of LLMs, such as their conversational nature and ability to interpret diverse inputs.
- Zero Trust Principles for AI: Applying zero-trust principles, where no entity (including an AI assistant) is inherently trusted, and all interactions are continuously verified, will be critical for securing complex AI ecosystems.
The Reprompt attack is a clear indicator that the security community must remain vigilant, innovating defensive measures as quickly as malicious actors devise new methods of exploitation. As AI continues to reshape our digital world, securing these intelligent systems will be paramount to ensuring their safe and beneficial adoption.







