
The second day of the Pwn2Own Automotive 2026 competition in Tokyo witnessed an unprecedented demonstration of security vulnerabilities, with expert researchers successfully compromising 29 distinct zero-day flaws across various vehicle systems, leading to substantial cash rewards totaling $439,250. This pivotal event, hosted during the prestigious Automotive World conference from January 21st to 23rd, serves as a crucial barometer for the cybersecurity posture of the rapidly evolving automotive industry. Participants rigorously test fully patched electric vehicle (EV) charging infrastructure, sophisticated in-vehicle infotainment (IVI) systems, and foundational car operating systems, including Automotive Grade Linux, highlighting critical areas for immediate enhancement in vehicle security.
Pwn2Own, orchestrated by Trend Micro’s Zero Day Initiative (ZDI), stands as a premier ethical hacking contest, designed to expose zero-day vulnerabilities in widely used software and hardware before malicious actors can exploit them. Its automotive iteration specifically targets the burgeoning landscape of connected vehicles, recognizing the profound safety, privacy, and economic implications of insecure vehicular technology. The competition’s structure ensures that only fully updated systems are presented, compelling researchers to uncover novel, previously unknown flaws. The high stakes, both in terms of financial rewards for researchers and the potential for widespread impact on manufacturers, underscore the critical importance of these findings for the global automotive sector. The event not only incentivizes advanced security research but also fosters a collaborative environment where vulnerabilities are responsibly disclosed, allowing vendors a 90-day window to develop and deploy patches before public disclosure, a model that has proven instrumental in strengthening digital defenses across various industries.

The cumulative results from the initial two days of Pwn2Own Automotive 2026 paint a compelling picture of the current threat landscape. A staggering 66 zero-day vulnerabilities have been identified and exploited, culminating in cash awards exceeding $955,750. These figures represent a significant investment in proactive security and reflect the increasing complexity and interconnectedness of modern vehicle architectures. The consistent discovery of such a high volume of critical flaws across successive Pwn2Own Automotive events—with 49 zero-days yielding $886,250 in 2025, and another 49 vulnerabilities securing $1,323,750 in 2024—underscores a persistent challenge for manufacturers in keeping pace with the rapid technological advancements and the evolving capabilities of security researchers. The continuous exposure of these vulnerabilities provides invaluable intelligence, driving manufacturers to adopt more robust security-by-design principles and implement more agile patch management processes.
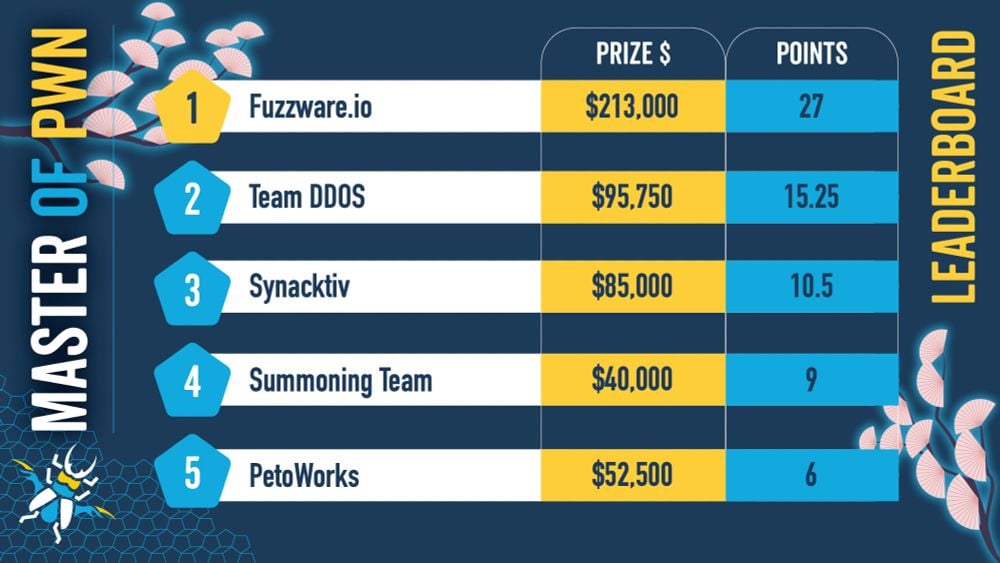
Fuzzware.io emerged as a dominant force during the competition, accumulating a total of $213,000 across the first two days. A significant portion of this total, $95,000, was earned on the second day through successful exploits targeting a range of EV charging controllers and stations. Their demonstrated ability to compromise the Phoenix Contact CHARX SEC-3150 charging controller, the ChargePoint Home Flex EV charger, and the Grizzl-E Smart 40A EV charging station highlights a critical vulnerability in the nascent but rapidly expanding EV charging infrastructure. The implications of these specific exploits are far-reaching, extending beyond mere financial disruption. Compromised charging stations could be manipulated to disrupt power grids, overcharge or damage vehicle batteries, or even serve as entry points for broader network attacks. Such vulnerabilities pose risks not only to individual users but also to the stability and reliability of national energy infrastructures.
Beyond EV charging systems, in-vehicle infotainment (IVI) units also proved susceptible to sophisticated attacks. Sina Kheirkhah of the Summoning Team secured $40,000 by gaining root access to prominent navigation and multimedia receivers, including the Kenwood DNR1007XR navigation receiver, the ChargePoint Home Flex, and the Alpine iLX-F511 multimedia receiver. IVI systems, often internet-connected and integrating various vehicle functions, represent a significant attack surface. Exploits against these systems could lead to unauthorized access to personal data, manipulation of vehicle settings, or even serve as a pivot point to compromise more critical vehicle control units, posing risks to driver safety and privacy. The successful exploitation of such widely deployed components underscores the need for stringent security measures within the entire infotainment supply chain, from hardware design to software development.

Core automotive operating systems, the foundational software layers governing vehicle operations, also faced scrutiny. Rob Blakely of Technical Debt Collectors and Hank Chen of InnoEdge Labs each garnered $40,000 for demonstrating zero-day exploit chains against Automotive Grade Linux (AGL) and the Alpitronic HYC50 charging station. Automotive Grade Linux, an open-source platform gaining traction across the industry, underpins many advanced IVI and telematics systems. Vulnerabilities at this foundational level are particularly concerning as they could grant attackers deep control over vehicle functions, ranging from remote diagnostics to critical driving systems. The Alpitronic HYC50, a high-power charging station, further reinforces the pervasive nature of security weaknesses across the EV ecosystem, indicating that even industrial-grade charging solutions are not immune to sophisticated attacks. These findings highlight the necessity for rigorous security auditing and continuous vulnerability management for all software components, especially those operating at the core of vehicle functionality.
Day one of the competition provided additional insights into the sophisticated techniques employed by researchers. The Synacktiv Team notably secured $35,000 by successfully chaining an information leak with an out-of-bounds write flaw to achieve root permissions on the Tesla Infotainment System via a USB-based attack. This demonstrates that even vehicles from manufacturers renowned for their advanced technology are not impenetrable. Furthermore, the same team received an additional $20,000 for chaining three distinct zero-day flaws to gain root-level code execution on the Sony XAV-9500ES digital media receiver. The ability to achieve root access, particularly through complex exploit chains, signifies a profound compromise, potentially allowing full control over the affected system and presenting significant risks for data exfiltration, system manipulation, or further lateral movement within the vehicle’s network.
The pervasive nature of these vulnerabilities carries profound implications for the automotive industry. As vehicles transition from mere transportation devices to highly connected, software-defined platforms, their attack surface expands exponentially. Manufacturers face immense pressure to integrate advanced technologies while simultaneously ensuring an impenetrable security posture. The findings from Pwn2Own Automotive 2026 serve as a stark reminder that security must be a foundational element throughout the entire product lifecycle, from initial design and development to post-sales support and over-the-air updates. Compliance with emerging international cybersecurity regulations, such as UNECE WP.29 and ISO/SAE 21434, becomes not just a legal requirement but an operational imperative to mitigate risks and maintain consumer trust. Failure to address these vulnerabilities proactively could lead to significant financial losses, reputational damage, and, critically, compromise the physical safety of vehicle occupants.
Looking ahead to the final day of the competition, the Grizzl-E Smart 40A EV charger will again be targeted by the Slow Horses of Qrious Secure and the PetoWorks team, suggesting persistent interest in this particular model or a belief that further vulnerabilities remain. The Juurin Oy team will focus on the Alpitronic HYC50, another high-capacity charging station, while Ryo Kato will attempt to exploit the Autel MaxiCharger. These continued efforts underscore the ongoing drive by security researchers to comprehensively probe the robustness of EV charging infrastructure. The cumulative results and the persistent focus on specific targets indicate that the industry must redouble its efforts in securing these critical components of the future mobility ecosystem.
In conclusion, the Pwn2Own Automotive 2026 competition has once again provided invaluable insights into the evolving cybersecurity landscape of connected vehicles. The significant number of zero-day vulnerabilities discovered across EV chargers, IVI systems, and car operating systems highlights the urgent need for manufacturers to prioritize security at every stage of development. The collaborative framework established by events like Pwn2Own, facilitating responsible disclosure and prompt remediation, is crucial for fostering a more secure automotive future. As vehicles become more autonomous and integrated into smart city infrastructures, continuous vigilance, proactive threat modeling, and robust security engineering will be paramount to safeguarding not only the integrity of individual vehicles but also the broader societal infrastructure they will increasingly interact with. The intelligence gathered from these events serves as a vital catalyst for the industry to accelerate its adoption of best practices in cybersecurity, ensuring that the promise of intelligent mobility is realized without compromising safety or privacy.








