
A sophisticated wave of voice-based social engineering, or "vishing," is actively targeting Okta Single Sign-On (SSO) accounts, leveraging advanced adversary-in-the-middle (AiTM) phishing kits to compromise enterprise credentials and facilitate extensive data theft. These highly adaptive platforms enable threat actors to manipulate authentication flows in real-time, bypassing traditional multi-factor authentication (MFA) mechanisms and gaining unauthorized access to critical corporate resources across various industries. This emerging threat highlights a significant escalation in social engineering tactics, demanding immediate and robust defensive strategies from organizations reliant on cloud-based identity management solutions.
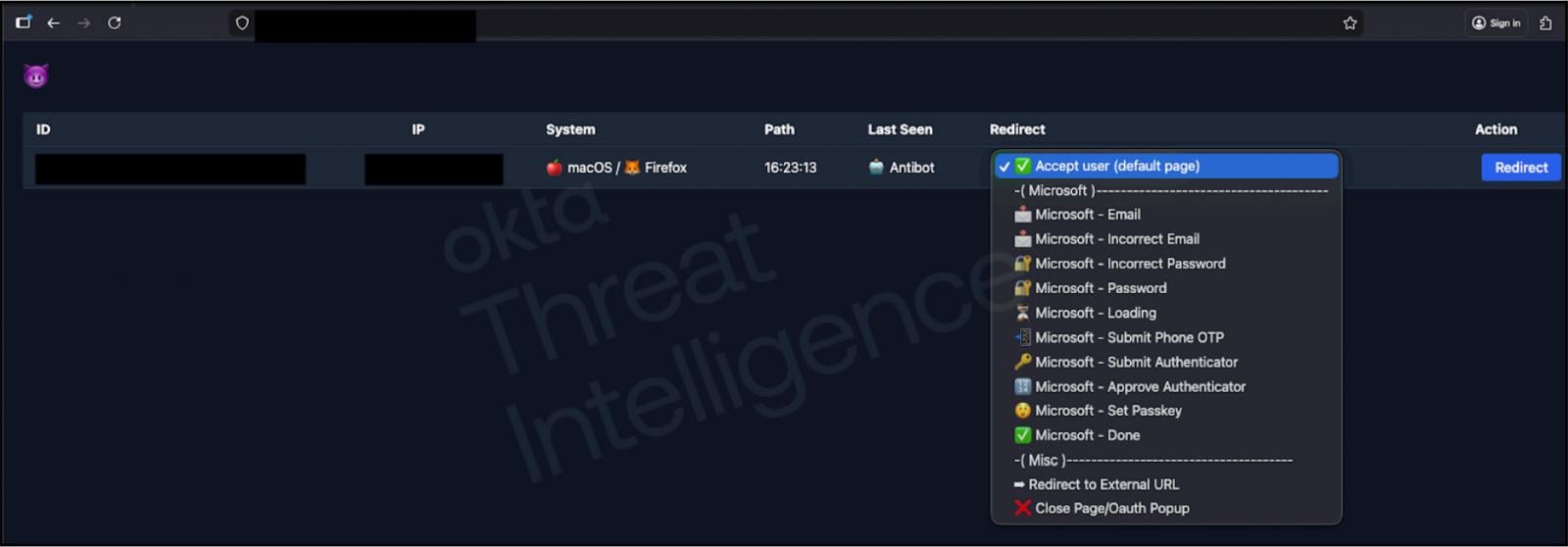
The core of these escalating attacks lies in specialized phishing kits, now widely available through a "Phishing-as-a-Service" (PhaaS) model. These sophisticated tools are being deployed by numerous hacking collectives, not only against identity providers such as Google, Microsoft, and Okta but also extending to high-value cryptocurrency platforms. Unlike conventional static phishing pages that merely collect submitted credentials, these next-generation AiTM platforms are engineered for dynamic interaction, allowing attackers to modify webpage content and display prompts in real-time during a live voice call with a target. This interactive capability creates a highly convincing illusion of legitimacy, making it exceptionally difficult for victims to discern the fraudulent nature of the interaction.
At a technical level, these advanced kits operate by establishing a proxy between the victim and the legitimate service. As a user enters their credentials onto the attacker-controlled phishing page, these inputs are immediately relayed to the threat actor’s backend infrastructure. Simultaneously, the attacker attempts to authenticate with the legitimate service using the stolen credentials. Should the service respond with an MFA challenge – such as a push notification or a one-time password (OTP) request – the attacker’s command-and-control (C2) panel dynamically updates the phishing page to mirror the legitimate MFA prompt. This synchronized display of fraudulent MFA requests creates an environment where even security-conscious users are susceptible, believing they are interacting directly with their organization’s authentication system.

The operational methodology behind these vishing campaigns demonstrates meticulous planning and execution. Threat actors initiate their campaigns with extensive reconnaissance, gathering intelligence on specific employees, their associated applications, and the legitimate contact numbers for their company’s IT support or helpdesk. This preparatory phase enables the creation of highly customized phishing pages and allows attackers to spoof corporate or helpdesk phone numbers, adding another layer of authenticity to their deceptive calls. When a victim is successfully lured into entering their username and password on the counterfeit site, these credentials are instantly forwarded, often to encrypted messaging channels like Telegram, which serve as the attackers’ real-time data exfiltration conduits.
This immediate interception of credentials allows threat actors to trigger genuine authentication attempts against the target organization’s systems. While maintaining the voice call with the victim, they can then direct the individual to enter any subsequent MFA codes – such as time-based one-time passwords (TOTP) – directly onto the phishing site. These codes are subsequently harvested and used by the attackers to complete the login process, thereby bypassing even robust, push-based MFA systems. The attackers’ ability to instruct victims on which specific number to select during an MFA challenge, coupled with the phishing kit’s real-time modification of the displayed prompt, effectively neutralizes advanced MFA features like number matching, which are designed to thwart simpler phishing attempts. In response to these evolving threats, Okta strongly advocates for the adoption of phishing-resistant MFA solutions, including Okta FastPass, FIDO2 security keys, and passkeys, which fundamentally alter the authentication paradigm by preventing credential capture.
The severity of these attacks is underscored by their ultimate objective: data theft. Okta, a leading cloud-based identity provider, serves as the central authentication hub for an immense array of enterprise web services and cloud platforms. Its Single Sign-On (SSO) service allows employees to authenticate once and gain seamless access to a multitude of corporate applications without repeated logins. This interconnected ecosystem includes critical platforms such as Microsoft 365, Google Workspace, Dropbox, Salesforce, Slack, Zoom, Box, Atlassian Jira and Confluence, and Coupa, among many others. By compromising an Okta SSO account, threat actors gain a privileged gateway to a company’s entire digital infrastructure. The Okta SSO dashboard, acting as a control panel, lists all accessible services, transforming a single compromised credential into a master key for a vast repository of organizational data.

The initial phase of the social engineering attack typically involves threat actors impersonating internal IT support personnel. They often offer assistance with setting up advanced security features, such as passkeys, for the Okta SSO service. This deceptive pretext guides employees to specially crafted adversary-in-the-middle phishing sites, which are designed to capture both SSO credentials and TOTP codes. These sophisticated sites are frequently named to appear legitimate, incorporating company branding and terms like "internal" or "my" (e.g., googleinternal.com or mygoogle.com for a hypothetical Google target), further enhancing their credibility. Technical intelligence indicates that some of these real-time attack relays have previously utilized Socket.IO servers, such as those hosted at inclusivity-team.onrender.com, to facilitate instant communication between the phishing site, the attacker, and the victim.
Once an employee’s credentials are successfully exfiltrated, the attackers immediately exploit them to log into the Okta SSO dashboard. From this vantage point, they meticulously survey the available applications and services, prioritizing those that contain sensitive or high-value data. Reports indicate a particular focus on platforms like Salesforce, which are often targeted due to the perceived ease of data exfiltration. The post-compromise activities are swiftly followed by extortion attempts, with threat actors demanding payment to prevent the public disclosure of stolen information. Evidence suggests that some of these extortion demands have been signed by ShinyHunters, a notorious group linked to numerous high-profile data breaches, including previous Salesforce data theft incidents. While ShinyHunters has not confirmed its direct involvement in these specific campaigns, their modus operandi aligns with the observed tactics.
The current targeting landscape indicates a concentrated effort against organizations within the Fintech, Wealth Management, Financial, and Advisory sectors, underscoring the financial motivations behind these sophisticated attacks. The financial services industry, with its trove of sensitive customer data and high transaction volumes, presents an attractive target for threat actors seeking to monetize stolen information or disrupt operations.
Okta’s Defensive Cyber Operations team actively monitors the threat landscape, identifying and proactively notifying customers of suspicious phishing infrastructure designed to mimic their sign-in pages. The company emphasizes the critical importance of robust security measures and continuous employee education to counter the increasing sophistication and insidiousness of these phishing campaigns. Okta provides extensive best practices and practical guidance to assist customers in identifying and preventing social engineering attacks, consistently updating its resources to address evolving threats.
The ongoing proliferation of advanced vishing kits and their successful deployment against critical identity infrastructure like Okta SSO represents a significant evolution in the cyber threat landscape. Organizations must move beyond traditional MFA implementations and prioritize phishing-resistant authentication methods. Beyond technical controls, a multi-layered security strategy is imperative, encompassing rigorous employee training programs to enhance awareness of social engineering tactics, robust incident response plans, continuous security monitoring, and the adoption of zero-trust architectural principles. The reliance on centralized identity providers makes them a high-value target, and securing this critical layer is paramount to safeguarding an organization’s entire digital footprint against increasingly adaptive and determined adversaries. The future of enterprise security will undoubtedly hinge on proactive defense mechanisms and a collective commitment to fostering a security-first culture that can withstand these dynamic and technologically advanced threats.








