An international law enforcement collaboration has culminated in the apprehension of a Lithuanian national, identified as the orchestrator behind a sophisticated global cybercriminal operation that compromised nearly three million computer systems through a malevolent variant of the widely used KMSAuto software activation utility, leading to the illicit acquisition of over a million dollars in virtual assets.
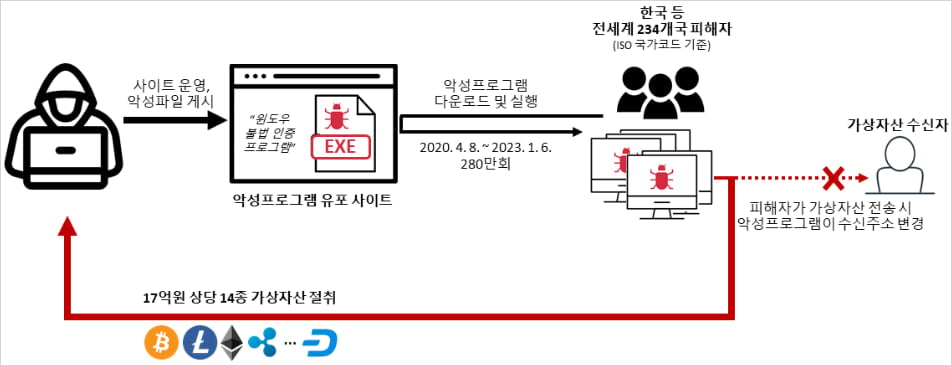
This significant breakthrough in cybercrime enforcement marks the culmination of a multi-jurisdictional investigation spanning several years, targeting the architect of a pervasive "clipper" malware campaign. The 29-year-old suspect was successfully extradited from Georgia to South Korea, a process facilitated by meticulous coordination through INTERPOL. The Korean National Police Agency disclosed that the individual had weaponized the KMSAuto tool, a utility frequently employed for the unauthorized activation of Microsoft Windows and Office suites, embedding it with malicious code designed to intercept and redirect cryptocurrency transactions. This insidious method allowed the attacker to replace legitimate recipient wallet addresses, copied by users to their clipboards, with addresses under the attacker’s control, thereby siphoning off funds during transfer.
The malicious distribution activity, according to official reports, spanned a substantial period, commencing in April 2020 and continuing until January 2023. During this timeframe, the cybercriminal disseminated approximately 2.8 million copies of the malware globally, masquerading as a legitimate, albeit illicit, software activation solution. The financial ramifications of this widespread compromise were considerable, with investigators attributing the theft of virtual assets valued at approximately KRW 1.7 billion, equivalent to about $1.2 million USD, across 8,400 distinct transactions involving 3,100 unique virtual asset addresses.
The initial impetus for this complex investigation emerged in August 2020, following a report detailing a cryptojacking incident in which a victim’s system was infected with clipper malware. This particular incident highlighted the subtle yet effective nature of the attack, where the intended recipient’s wallet address was stealthily swapped, diverting payments to the perpetrator. Forensic analysis subsequently linked this incident to the compromised KMSAuto tool, revealing a broader pattern of infection. The investigative teams meticulously uncovered that the clipper malware specifically targeted transactions on at least six prominent cryptocurrency exchanges, demonstrating a calculated focus on high-value digital assets.

The investigation’s trajectory involved an intricate process of tracing the stolen virtual assets across various blockchain networks and meticulously identifying the digital footprints of the perpetrator. This digital trail eventually led law enforcement to Lithuania, where a coordinated raid was executed in December 2024. This operation resulted in the seizure of 22 items, including laptop computers and mobile phones, believed to contain critical evidence related to the cybercriminal enterprise. The subsequent examination of these confiscated devices yielded conclusive incriminating evidence, providing the necessary foundation for the suspect’s eventual arrest in April 2025. The individual was apprehended while traveling from Lithuania to Georgia, illustrating the persistent global reach of law enforcement in pursuing cybercriminals across borders.
The Perilous Landscape of Software Piracy
The case underscores a critical and often overlooked vulnerability: the inherent risks associated with using unofficial or pirated software. Software activators, crack tools, and key generators, such as the KMSAuto utility implicated in this campaign, frequently serve as conduits for malware distribution. Users, driven by the desire to circumvent legitimate licensing costs, inadvertently expose their systems to significant security threats. These tools often require elevated system privileges to function, making them ideal vehicles for injecting malicious code deep within the operating system, bypassing standard security protocols.
The global landscape of software piracy remains a fertile ground for cybercriminals. The perceived anonymity and the widespread availability of such tools on unregulated forums and websites create an ecosystem where malware can proliferate with alarming ease. From a cybersecurity perspective, any executable file downloaded from an untrusted source, particularly one promising to unlock copyrighted software for free, should be treated with extreme caution. The lack of digital signatures, coupled with the opaque nature of their source code, renders these applications highly susceptible to tampering and malicious modification. This incident is a stark reminder that the cost savings from pirated software are often dwarfed by the potential financial and privacy losses incurred from subsequent malware infections.
Understanding Clipper Malware: A Silent Threat

Clipper malware represents a particularly insidious form of cyber threat, designed to exploit a common user behavior: copying and pasting digital information, particularly sensitive data like cryptocurrency wallet addresses. Its effectiveness lies in its simplicity and stealth. Once installed, it operates in the background, continuously monitoring the system’s clipboard for patterns indicative of cryptocurrency addresses. When a valid address is detected, the malware instantly replaces it with an address belonging to the attacker. The speed of this replacement is often imperceptible to the user, who typically pastes the seemingly correct address without re-verification, leading to irreversible loss of funds.
The rise of cryptocurrency has inadvertently created new vectors for cybercrime. The decentralized and immutable nature of blockchain transactions, while offering numerous benefits, also means that once a transaction is confirmed, it is nearly impossible to reverse. This characteristic makes cryptocurrency transfers an attractive target for clipper malware, as successful theft provides immediate, untraceable gains for the attacker. The attacker in this case leveraged this fundamental aspect of cryptocurrency, combining it with the widespread use of pirated software, to maximize their illicit gains across a global victim pool.
International Cooperation in Cybercrime Enforcement
The successful apprehension and extradition of the suspect highlight the increasing effectiveness of international law enforcement cooperation in combating sophisticated cybercrime. Cybercriminals frequently operate across national borders, leveraging the complexities of different legal jurisdictions to evade capture. However, organizations like INTERPOL play a crucial role in bridging these gaps, facilitating intelligence sharing, and coordinating cross-border operations. The extradition from Georgia to South Korea, involving a Lithuanian national, demonstrates the growing commitment and capability of global authorities to track, identify, and prosecute cybercriminals regardless of their physical location or the digital nature of their crimes. Such collaborations are essential for creating a deterrent effect and ensuring that cyberspace does not remain a safe haven for illegal activities.
Implications and Future Outlook
This incident carries significant implications for both individual users and the broader cybersecurity landscape. For individuals, it serves as a critical warning against the dangers of software piracy and the necessity of verifying all critical information, especially financial addresses, before completing transactions. Implementing basic cybersecurity hygiene, such as using legitimate software, maintaining up-to-date antivirus solutions, and practicing multi-factor authentication for cryptocurrency wallets, is paramount.
From a broader perspective, this case underscores the evolving nature of cyber threats. While large-scale data breaches and ransomware attacks often dominate headlines, seemingly simpler and more targeted malware, like clippers, can still inflict substantial financial damage on a vast number of victims. The exploitation of common user behaviors and the leveraging of readily available tools (like KMSAuto) represent a persistent challenge for cybersecurity professionals.
Looking forward, the fight against such cyber campaigns will require a multi-faceted approach. Enhanced international collaboration, as demonstrated in this case, will continue to be vital. Furthermore, increased public awareness campaigns highlighting the risks of pirated software and the mechanisms of clipper malware are necessary to educate users. Technological advancements in cybersecurity, including more sophisticated endpoint detection and response (EDR) solutions, behavioral analysis, and real-time transaction monitoring by cryptocurrency exchanges, will also play a crucial role in mitigating these threats. As digital currencies become more integrated into mainstream finance, the vigilance against such insidious forms of digital theft must intensify. The successful dismantling of this operation sends a clear message: the digital world is not beyond the reach of justice, and those who exploit its vulnerabilities will ultimately be held accountable.