A sophisticated cryptocurrency phishing operation has exploited a legitimate subdomain belonging to the food delivery platform GrubHub, luring users with promises of a tenfold return on Bitcoin transferred to attacker-controlled digital wallets. This incident highlights the evolving tactics employed by cybercriminals, who increasingly leverage trusted brand infrastructure to enhance the credibility of their fraudulent schemes and bypass conventional email security protocols. The deceptive campaign, which unfolded across late December, underscores the persistent challenges faced by both corporations in securing their digital ecosystems and individuals in discerning authentic communications from highly convincing fakes.
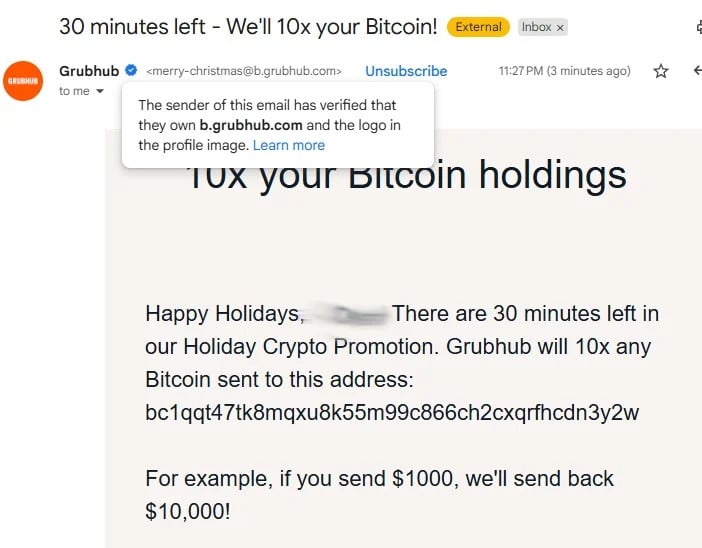
The fraudulent messages, disseminated beginning around December 24, masqueraded as official communications from GrubHub, specifically targeting recipients with a purported "Holiday Crypto Promotion." These emails contained highly enticing offers, such as a pledge to multiply any Bitcoin sent to a designated address by a factor of ten. For instance, a sender transferring $1,000 in Bitcoin was promised a return of $10,000. What lent an alarming degree of legitimacy to these solicitations was their apparent origin from email addresses residing on a subdomain, b.grubhub.com, which is genuinely utilized by GrubHub for official correspondence with its extensive network of merchant partners and restaurants. Specific sender addresses observed included variations such as [email protected] and [email protected], further reinforcing the illusion of authenticity and often incorporating the recipient’s name to personalize the deception.
This particular method of attack, where a legitimate or seemingly legitimate subdomain is utilized, represents a significant escalation from typical phishing attempts. Rather than relying on easily identifiable spoofed domains or generic email addresses, the attackers meticulously crafted messages that appeared to originate from a verified part of GrubHub’s digital footprint. This technique is particularly effective because it often allows the malicious emails to circumvent standard spam filters and email authentication checks (such as SPF, DKIM, and DMARC) that are designed to detect and block messages from unauthorized senders. When an email originates from a domain or subdomain that is genuinely configured to send email for the legitimate entity, it is far more likely to land in a user’s primary inbox, increasing the probability of engagement and potential compromise.

The core mechanism of this scheme is a classic cryptocurrency reward scam, a pervasive form of financial fraud where victims are enticed to send digital assets to perpetrators under the false pretense of receiving a substantially larger sum in return. These scams often play on human greed and the desire for quick wealth, leveraging the volatile and sometimes opaque nature of cryptocurrency markets. The promise of an immediate tenfold return is an extreme outlier in any legitimate investment scenario, yet the perceived urgency—often indicated by short deadlines such as "30 minutes left"—coupled with the apparent legitimacy of the sender, can override rational judgment. The irreversible nature of cryptocurrency transactions means that once funds are sent to a scammer’s wallet, recovery is exceptionally difficult, if not impossible, making these attacks highly lucrative for criminals.
While GrubHub has acknowledged the incident, describing the messages as "unauthorized" and confirming that they have "contained the issue" and are "taking steps to ensure it doesn’t happen again," the precise vector of the attack remains undisclosed. Industry speculation has pointed towards potential vulnerabilities such as a DNS takeover attack, where an attacker gains control over a domain’s DNS records, allowing them to send emails that pass authenticity checks. Alternatively, the compromise of an email sending service or a misconfiguration in GrubHub’s email infrastructure could have been exploited. Without specific technical details from GrubHub, the exact method by which the attackers managed to dispatch emails from a verified subdomain remains a subject of ongoing analysis within the cybersecurity community. The company’s response, though swift in containment, has not yet elucidated the root cause, which is crucial for preventing similar incidents across the broader digital landscape.
This incident is not an isolated event for GrubHub. Earlier in the year, the food delivery enterprise disclosed a separate data breach where a threat actor gained unauthorized access to personal information, including names, email addresses, and phone numbers, belonging to its customers, merchants, and drivers. That prior intrusion was attributed to a compromised account used by a third-party service provider offering support to GrubHub. Such recurring security challenges underscore the complexities of managing a vast digital infrastructure, especially when reliant on third-party integrations, which often introduce additional attack surfaces and vulnerabilities that must be rigorously managed. The interconnectedness of modern digital services means that a weak link in any part of the supply chain can expose the entire ecosystem to risk.

The broader implications of such sophisticated phishing campaigns extend beyond immediate financial losses to victims. They erode trust in digital communications, making users increasingly skeptical of even legitimate messages from established brands. This "crying wolf" effect can lead to users ignoring critical security alerts or legitimate marketing communications, creating further problems for businesses. For corporations like GrubHub, such incidents can inflict significant reputational damage, potentially leading to customer churn, legal liabilities, and increased regulatory scrutiny. Maintaining customer trust is paramount in the competitive food delivery market, and security breaches directly undermine this critical asset.
From a technical perspective, the exploitation of legitimate subdomains highlights the limitations of current email authentication standards if not implemented perfectly or if the underlying infrastructure is compromised. While protocols like SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting & Conformance) are designed to verify the sender’s identity and prevent spoofing, their effectiveness relies on meticulous configuration and continuous monitoring. A compromised server or a misconfigured record within a legitimate subdomain can bypass these checks, creating a credible conduit for malicious traffic. This necessitates a proactive and holistic approach to cybersecurity, encompassing not just perimeter defenses but also internal network hygiene, third-party vendor risk management, and continuous vulnerability assessments.
The psychological dimension of these scams cannot be overstated. Attackers skillfully combine urgency, authority, and the allure of high returns to manipulate victims. The "fear of missing out" (FOMO) on a unique, time-sensitive opportunity can override caution, particularly when the offer appears to come from a trusted entity. The anonymity and decentralized nature of cryptocurrency also play a significant role. Unlike traditional banking transactions, which often have chargeback mechanisms or regulatory oversight, cryptocurrency transfers are typically irreversible. Once the digital assets leave a user’s wallet and enter the attacker’s, tracing and recovering them becomes an arduous, often fruitless, endeavor, frequently requiring cooperation from international law enforcement and cryptocurrency exchanges, which is rarely forthcoming for smaller individual losses.
To mitigate such threats, both individuals and organizations must adopt enhanced security postures. For individuals, vigilance is paramount. Any unsolicited communication promising extraordinary returns on investment, especially involving cryptocurrency, should be treated with extreme skepticism. Users should independently verify offers by navigating directly to the official website of the company in question, rather than clicking links embedded in suspicious emails. Furthermore, enabling multi-factor authentication (MFA) on all online accounts, exercising caution with personal information, and understanding the irreversible nature of cryptocurrency transactions are crucial defensive measures.
For corporations, the incident serves as a stark reminder of the need for comprehensive domain and email security strategies. This includes not only robust implementation of SPF, DKIM, and DMARC across all domains and subdomains but also continuous monitoring of DNS records for unauthorized changes, rigorous access controls for email sending infrastructure, and stringent vetting of third-party vendors with access to any part of the digital ecosystem. Regular security audits, penetration testing, and employee training on phishing awareness are also indispensable components of a resilient cybersecurity framework. Incident response plans must be well-rehearsed, allowing for rapid containment and clear communication in the event of a breach.
Looking ahead, the landscape of cybercrime is likely to continue evolving, with attackers refining their techniques to exploit new technologies and human vulnerabilities. The increasing sophistication of phishing attempts, particularly those leveraging legitimate infrastructure, signals a future where distinguishing authentic digital communications from malicious ones will become progressively more challenging. As businesses expand their digital footprints and rely more heavily on interconnected services, the imperative for proactive, adaptive cybersecurity measures will only intensify. The GrubHub incident serves as a critical case study, emphasizing the ongoing arms race between cyber defenders and attackers, and the collective responsibility to enhance digital literacy and security practices across all levels of online engagement.