A cunningly crafted cyberattack has leveraged a subtly altered domain name, mimicking a popular Microsoft activation utility, to disseminate potent PowerShell scripts that subsequently infect Windows machines with the ‘Cosmali Loader’ malware, highlighting the persistent threat of typosquatting in software supply chains. This incident underscores the critical vulnerabilities introduced by unofficial software activation methods and the sophisticated tactics employed by threat actors to exploit minor user errors.
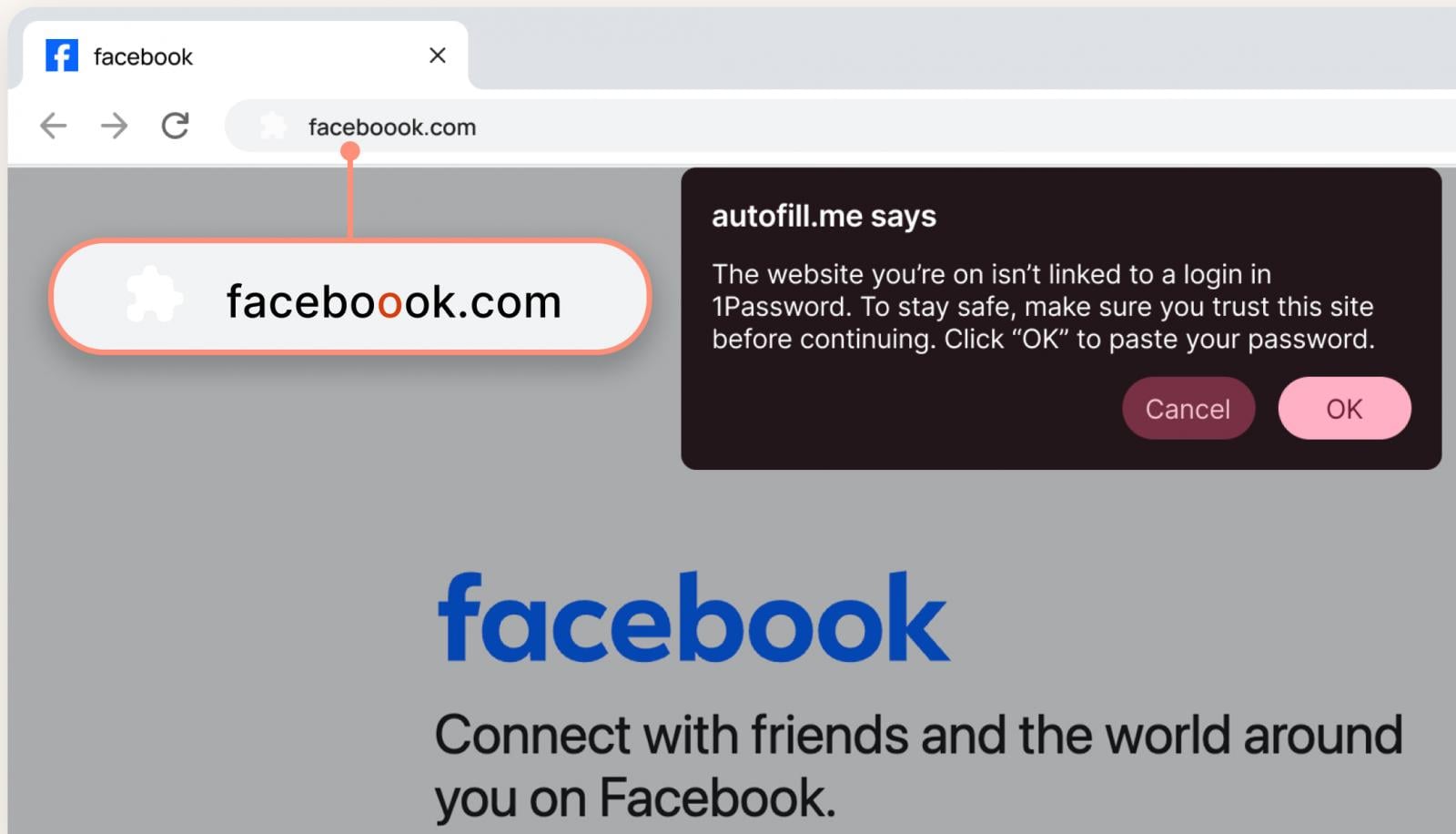
The recent discovery of a malicious campaign exploiting a typosquatted domain designed to impersonate the legitimate Microsoft Activation Scripts (MAS) tool has sent ripples through the cybersecurity community. This particular scheme involved a deceptive domain, "get.activate[.]win," which closely mirrors the authentic "get.activated.win" used in the official MAS activation instructions. The minute difference – a single omitted character – was deliberately chosen to capitalize on potential user mistypings, a classic technique known as typosquatting. This method preys on human fallibility, transforming a simple typographical error into a gateway for significant system compromise.
Reports from affected MAS users, surfacing across various online forums, detailed the unsettling experience of receiving unexpected pop-up warnings indicating an infection by a payload identified as ‘Cosmali Loader.’ These notifications, unusually candid, directly attributed the infection to the user’s navigational error, explicitly stating: "You have been infected by a malware called ‘cosmali loader’ because you mistyped ‘get.activated.win’ as ‘get.activate[.]win’ when activating Windows in PowerShell." The warnings further claimed that the malware’s control panel was insecure, potentially exposing infected systems to unauthorized access, and strongly advised a complete reinstallation of Windows. To substantiate the claim, users were instructed to scrutinize their Task Manager for anomalous PowerShell processes, providing a seemingly legitimate diagnostic step within the notification itself.
The Modus Operandi: Typosquatting and Malicious Script Delivery
Typosquatting, also referred to as URL hijacking, is a form of cybersquatting that relies on mistakes made by Internet users when typing a website address into a web browser. The attacker registers a domain name that is a common misspelling of a legitimate domain. In this case, the perpetrators meticulously selected a domain differing by only one letter from the official MAS activation domain. This calculated strategy demonstrates a clear understanding of user behavior and the common shortcuts or errors individuals might make when manually entering commands or URLs.
Upon accessing the malicious "get.activate[.]win" domain, users were unknowingly served PowerShell scripts designed to initiate the infection chain. PowerShell, a powerful command-line shell and scripting language developed by Microsoft, is a favored tool among system administrators for automating tasks. However, its inherent capabilities also make it an attractive vector for threat actors, who can leverage it to execute arbitrary code, download additional payloads, and establish persistence on compromised systems, often bypassing traditional security defenses that might focus on executable files. The execution of remote PowerShell scripts without thorough scrutiny represents a significant security risk, as it grants attackers direct control over the system’s core functionalities.

Cosmali Loader: A Multifaceted Threat
The primary payload delivered through this typosquatting campaign is the ‘Cosmali Loader.’ Security researchers, notably RussianPanda, have identified Cosmali Loader as an open-source malware framework capable of deploying various secondary threats. In the context of this specific incident, analysis revealed that Cosmali Loader was instrumental in delivering cryptomining utilities and the XWorm remote access trojan (RAT).
Cryptomining malware clandestinely harnesses the processing power of an infected computer to mine cryptocurrencies for the attacker. This process consumes significant system resources, leading to degraded performance, increased power consumption, and accelerated hardware wear, all without the user’s knowledge or consent. While not always immediately destructive, the long-term impact on system health and operational costs can be substantial.
The XWorm RAT, on the other hand, represents a more direct and severe threat. Remote Access Trojans provide attackers with comprehensive control over a compromised system, enabling them to perform a wide array of malicious activities. These can include, but are not limited to, data exfiltration, keystroke logging, webcam and microphone activation, arbitrary file execution, and even complete system takeover. The presence of a RAT transforms an infected machine into a potent tool for further cybercriminal activities, potentially compromising sensitive personal and corporate data.
The Enigma of the Self-Reporting Malware
One of the most unusual aspects of this campaign was the nature of the infection warnings themselves. The pop-up messages explicitly informed users of their compromise and even provided rudimentary instructions for verifying the infection. This self-reporting characteristic is highly atypical for malware, which typically operates stealthily to maximize its operational lifespan.
Speculation within the cybersecurity community suggests that these warning messages might have originated from a "well-intended researcher" who managed to gain unauthorized access to the malware’s command-and-control (C2) panel. Such an individual might have then leveraged this access to push warning notifications to infected users, essentially turning the attackers’ infrastructure against them to alert victims. While unconventional, this hypothesis aligns with the observed behavior. However, such an intervention, while potentially beneficial to victims, also raises complex ethical and legal questions regarding unauthorized access to adversary infrastructure, even if for a benevolent purpose. It also highlights the inherent vulnerabilities within the threat actors’ own operational security, suggesting a lack of robust protection for their C2 infrastructure.

Understanding Microsoft Activation Scripts (MAS)
Microsoft Activation Scripts (MAS) is an open-source collection of PowerShell scripts designed to automate the activation of Microsoft Windows and Microsoft Office products. The project employs various activation methods, including Hardware ID (HWID) activation, Key Management Service (KMS) emulation, and other bypasses like Ohook and TSforge. These scripts are widely available on platforms like GitHub and are actively maintained by a community of developers.
From Microsoft’s perspective, tools like MAS are considered piracy tools. They enable users to activate software products without a legitimate, purchased license, circumventing the company’s established licensing system. While MAS provides a functional alternative for users seeking to activate Microsoft products without incurring costs, its unofficial nature inherently places users at a heightened risk. The very act of seeking and utilizing such tools often involves interacting with less secure sources and executing scripts from unverified origins, creating a fertile ground for malware distribution. The MAS project maintainers themselves have issued warnings regarding this specific campaign, urging users to meticulously verify any commands before execution, underscoring the awareness within the community of the associated risks.
The Inherent Dangers of Unofficial Activation Tools
This incident serves as a stark reminder of the persistent and significant dangers associated with using unofficial software activation tools. While the allure of free software activation can be strong, the risks far outweigh the perceived benefits. Historically, such tools have been repeatedly exploited by threat actors as a highly effective vector for malware delivery.
Attackers frequently embed malicious payloads within these activators or distribute them through compromised websites mimicking legitimate sources. Users, eager to bypass licensing fees, often overlook security warnings and execute unverified scripts or applications with elevated privileges, creating a direct pathway for malware to infiltrate their systems. Past incidents have even involved state-sponsored groups leveraging malicious Windows activators to target specific entities, demonstrating the severity and sophistication of threats that can hide within these seemingly innocuous utilities. The current campaign, while not directly attributed to state actors, mirrors the methodology and exploits the same underlying user behavior and trust vulnerabilities.
Mitigation Strategies and Best Practices
.png)
To safeguard against such sophisticated typosquatting attacks and the broader risks associated with unofficial software, users and organizations must adopt stringent cybersecurity practices:
- Verify URLs Meticulously: Always double-check domain names, especially when executing commands or downloading software. Even a single character difference can lead to a malicious site. Browser extensions that highlight potential typosquats can also be beneficial.
- Adhere to Official Licensing: The most robust defense is to use legitimate, officially licensed software obtained directly from Microsoft or authorized resellers. This ensures software integrity and regular security updates.
- Exercise Extreme Caution with Remote Code Execution: Never execute remote code, particularly PowerShell scripts, if its origin is not fully trusted or if its functionality is not completely understood. Always review scripts line by line before execution.
- Utilize Sandboxing for Suspicious Files: For any unverified scripts or executables, execute them within a sandboxed environment or a virtual machine. This isolates potential threats, preventing them from impacting the host system.
- Implement Robust Endpoint Security: Deploy comprehensive endpoint detection and response (EDR) solutions that can identify and block malicious PowerShell activity, cryptominers, and RATs. Regular scanning and real-time monitoring are crucial.
- Network Segmentation and Least Privilege: Organizations should segment their networks to limit the lateral movement of malware. Implementing the principle of least privilege ensures that users and applications only have the minimum necessary access rights, reducing the potential damage of a compromise.
- Regular Software Updates: Keep operating systems, applications, and security software fully patched and updated to remediate known vulnerabilities that attackers might exploit.
- User Education and Awareness: Continuous training for users on phishing, typosquatting, social engineering, and the dangers of unofficial software is paramount. A well-informed user base is the first line of defense.
- Leverage DNS Security: Implement DNS filtering and security services that can block access to known malicious domains, including typosquatted ones.
Future Outlook and Industry Implications
This incident serves as a potent reminder that cyber adversaries are continuously refining their tactics, relying on a blend of technical prowess and psychological manipulation. Typosquatting remains an effective vector due to the inherent human tendency for error and the vastness of the internet, making perfect recall of every URL impractical. The use of powerful system tools like PowerShell for malware delivery underscores a broader trend where legitimate utilities are weaponized, posing a significant challenge for signature-based detection mechanisms.
The peculiar nature of the self-reporting malware, irrespective of its true origin, also highlights the dynamic and unpredictable landscape of cyber warfare. Whether it was an attacker’s oversight, a researcher’s intervention, or a deliberate tactic to create confusion, it adds a layer of complexity to incident response. Cybersecurity professionals must remain vigilant, constantly adapting their defenses to counter evolving threats and educating users about the multifaceted risks present in the digital ecosystem. The reliance on official channels for software procurement and activation, combined with robust technical controls and continuous user awareness, forms the bedrock of a resilient cybersecurity posture against such deceptive and damaging campaigns.