A newly identified, severe security flaw within MongoDB, designated as CVE-2025-14847 and colloquially termed "MongoBleed," has entered a phase of active exploitation, exposing a substantial number of database instances to unauthorized data extraction. This critical vulnerability, rooted in how the popular NoSQL database processes compressed network traffic, allows unauthenticated attackers to remotely siphon sensitive information from affected servers, with public internet scans revealing over 87,000 potentially compromised systems globally. The urgency for organizations to apply available patches and implement robust security measures cannot be overstated, given the profound implications for data confidentiality and system integrity.
The Genesis of MongoBleed: A Deep Dive into the Technical Flaw
The MongoBleed vulnerability, formally tracked as CVE-2025-14847, originates from a fundamental mishandling of network packets by the MongoDB Server, specifically concerning its interaction with the zlib library for lossless data compression. zlib is a widely adopted data compression library, integral to numerous network protocols and applications due to its efficiency. In the context of MongoDB, it facilitates the compression and decompression of network messages, aiming to optimize data transfer and reduce bandwidth consumption.
The core of the flaw lies in a critical logical error: instead of accurately returning the actual length of decompressed data, the MongoDB Server erroneously reports the total amount of memory it has allocated for the decompression buffer. This seemingly minor discrepancy creates a significant security loophole. An attacker can craft and transmit a malformed network message that deceptively claims a much larger size after decompression than it actually is. Upon receiving this message, the vulnerable MongoDB server, following its flawed logic, allocates a disproportionately large memory buffer based on the attacker’s false claim. Crucially, when the server then attempts to respond or process this data, it may inadvertently include portions of its own in-memory data, which resides adjacent to the oversized buffer, and leak this sensitive information back to the attacker’s client.
This information disclosure vulnerability is particularly insidious because it bypasses the authentication stage. The decompression of incoming network messages is a preliminary step in the server’s processing pipeline, occurring before any authentication checks are performed. Consequently, a malicious actor does not require valid credentials or any form of prior access to exploit MongoBleed, rendering virtually any publicly accessible, unpatched MongoDB instance a potential target. The severity of this issue is reflected in its assigned CVSS score of 8.7, categorizing it as a critical vulnerability that demands immediate attention.

The Pervasive Threat: Scope and Impact of Exposure
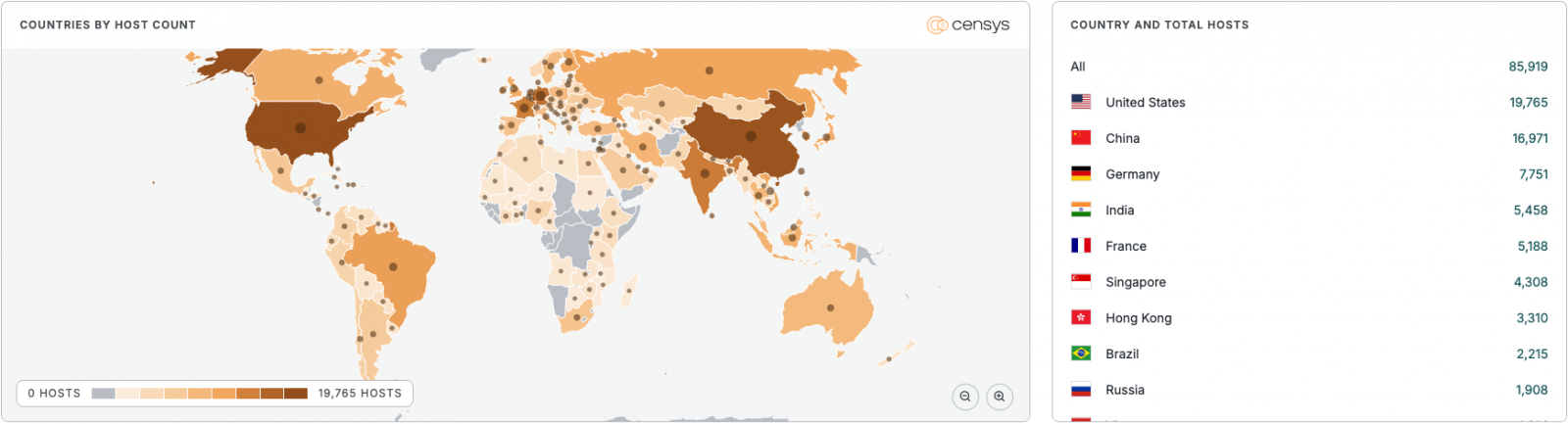
The scale of the MongoBleed exposure is alarming. Internet-wide scanning platforms, such as Censys, have identified more than 87,000 MongoDB instances that are not only potentially vulnerable but also directly exposed to the public internet. This vast digital footprint represents a significant attack surface for cyber adversaries. The geographical distribution of these exposed servers highlights a global risk, with the United States accounting for nearly 20,000 instances, followed closely by China with almost 17,000, and Germany with approximately 8,000. This widespread exposure underscores a common cybersecurity challenge: the misconfiguration of database servers, often left with default settings or inadequate network segmentation, making them readily discoverable and accessible to anyone with an internet connection.
Beyond self-hosted deployments, the cloud environment also faces substantial risk. Telemetry data from cloud security platforms indicates that a significant percentage of visible systems, specifically 42% in some observations, possess at least one MongoDB instance running a version susceptible to CVE-2025-14847. This figure encompasses both internal network resources and publicly exposed instances, emphasizing that the problem extends beyond direct internet exposure to potentially impact internal corporate networks if an attacker gains initial foothold. The "shared responsibility model" prevalent in cloud computing places the onus of patching and securing self-managed database instances squarely on the customer, a responsibility often overlooked until a critical vulnerability like MongoBleed emerges.
The types of secrets that can be exfiltrated through this flaw are extensive and highly valuable to attackers. They range from database credentials, API keys, and cloud access keys—which can grant access to broader cloud infrastructure—to session tokens, personally identifiable information (PII), sensitive internal logs, system configurations, file paths, and various forms of client-related data. The compromise of such data can lead to cascading security incidents, including full system compromise, data breaches, financial fraud, and compliance violations, with severe reputational and legal consequences for affected organizations.
Active Exploitation and the Accelerating Threat Landscape
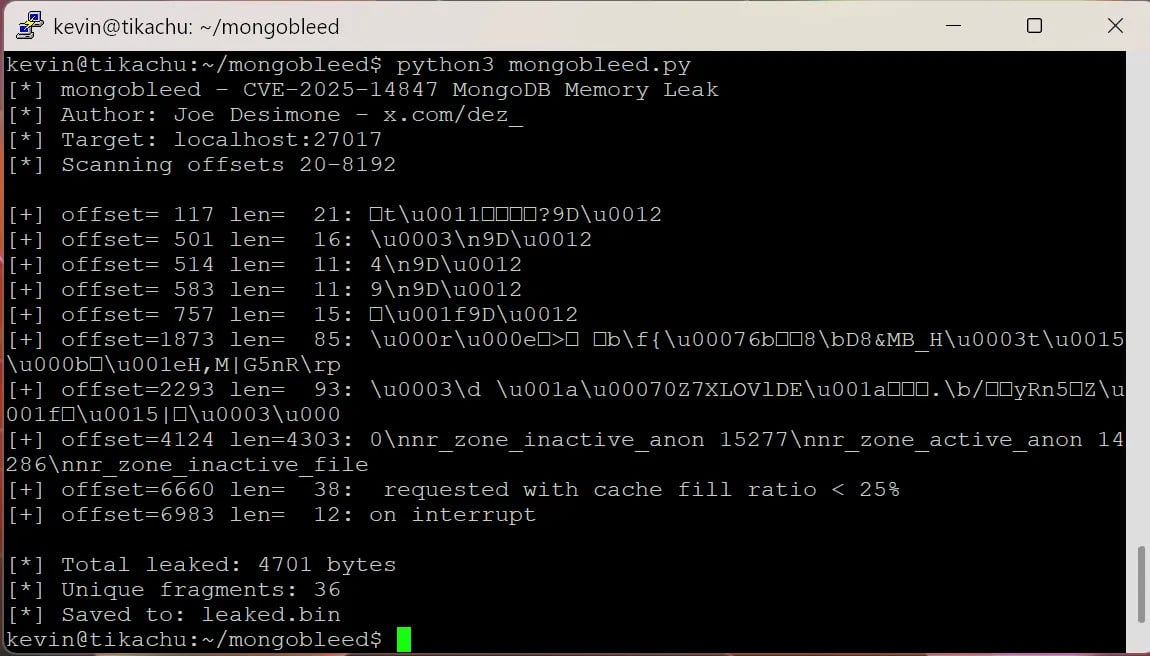
The transition of MongoBleed from a theoretical vulnerability to an actively exploited threat has been rapid, fueled by the public release of a proof-of-concept (PoC) exploit. Security researchers at Ox Security meticulously detailed the technical underpinnings of the flaw, providing critical insights into its mechanics. Subsequently, Elastic security researcher Joe Desimone developed and released a functional PoC, aptly named "MongoBleed," specifically designed to demonstrate the memory data leakage. Esteemed security researcher Kevin Beaumont independently verified the efficacy of this PoC, confirming that it requires only the IP address of a MongoDB instance to begin extracting sensitive in-memory data, including plaintext database passwords and AWS secret keys.

The immediate availability of a functional PoC significantly lowers the barrier for exploitation, making it accessible to a broader spectrum of threat actors, from opportunistic script kiddies to sophisticated organized cybercrime groups and state-sponsored entities. The observed exploitation in the wild, as confirmed by cloud security firm Wiz, indicates that attackers are already leveraging this vulnerability. While unverified, some threat actors have even claimed to have utilized the MongoBleed flaw in a recent high-profile breach targeting Ubisoft’s Rainbow Six Siege online platform, illustrating the potential for real-world impact on widely used services.
The rapid weaponization of such vulnerabilities underscores a critical dynamic in modern cybersecurity: the shrinking window between vulnerability disclosure and active exploitation. Organizations must possess agile and proactive security postures to mitigate risks effectively. The existence of a public exploit means that any unpatched, internet-facing MongoDB server is under immediate and continuous threat of compromise.
Mitigation and Remediation Strategies: A Race Against Time
Addressing the MongoBleed vulnerability demands immediate and decisive action from organizations managing MongoDB deployments. The primary and most effective mitigation strategy is to upgrade to a patched version of the MongoDB Server. MongoDB Inc. responded swiftly by releasing critical fixes, making patches available for self-hosting instances since December 19. The recommended safe releases include versions 8.2.3, 8.0.17, 7.0.28, 6.0.27, 5.0.32, and 4.4.30. A wide array of MongoDB versions are impacted, some dating back to late 2017 and others as recent as November 2025, highlighting the pervasive nature of this underlying issue across multiple product lines.
For customers leveraging MongoDB Atlas, the fully managed, multi-cloud database service, the patching process has been largely automated. These users received the necessary updates automatically, significantly reducing their exposure risk without requiring manual intervention. This scenario underscores the inherent security advantages of managed cloud services, where the vendor assumes responsibility for underlying infrastructure patching.
However, for organizations unable to immediately upgrade due to operational constraints or compatibility issues, MongoDB has provided an interim workaround: disabling zlib compression on the server. While this action eliminates the attack vector by preventing the server from processing compressed network messages via zlib, it comes with a potential trade-off in performance and bandwidth efficiency. MongoDB also recommends considering safer, well-maintained alternatives for lossless data compression, such as Zstandard (zstd) developed by Meta, or Snappy (formerly Zippy) maintained by Google. These libraries often offer superior performance and have undergone rigorous security scrutiny.
Beyond patching, a defense-in-depth strategy is crucial. Organizations must re-evaluate and strengthen their network segmentation policies, ensuring that MongoDB instances are not directly exposed to the public internet unless absolutely necessary. Implementing robust firewalls, access control lists (ACLs), and virtual private networks (VPNs) to restrict access to trusted networks and users can significantly reduce the attack surface. Furthermore, even though MongoBleed bypasses authentication, maintaining strong authentication and authorization practices remains fundamental to overall security posture, protecting against other attack vectors. Regular security audits, penetration testing, and vulnerability scanning are essential to proactively identify and address weaknesses before they can be exploited.
Detection and Incident Response: Proactive Monitoring for Compromise
Given the active exploitation of MongoBleed, organizations must not only focus on patching but also on detecting potential compromises. Simply patching after a period of exposure may not be sufficient if an attacker has already exfiltrated data or established persistence. Security researcher Eric Capuano has provided valuable insights into detection methodologies, suggesting that organizations look for specific indicators of compromise (IoCs). A key indicator involves monitoring MongoDB logs for a source IP address exhibiting an unusually high number of connections—hundreds or even thousands—but with a complete absence of associated client metadata events. This pattern could signify an attacker attempting to repeatedly trigger the MongoBleed flaw without fully authenticating or engaging in typical client-server interactions.
Leveraging Capuano’s research, Florian Roth, creator of the THOR APT Scanner, developed the "MongoBleed Detector," a specialized tool designed to parse MongoDB logs and identify these tell-tale signs of CVE-2025-14847 exploitation. While such tools are invaluable, Capuano also cautions that current detection methods are based on the publicly available PoC exploit code. Sophisticated attackers could modify their attack patterns, for instance, by including fabricated client metadata or by reducing the speed of exploitation to evade detection based on current signatures. This highlights the need for adaptable and intelligent threat detection systems that can identify anomalous behavior rather than relying solely on static signatures.
A comprehensive incident response plan is critical for any organization suspecting a MongoBleed compromise. This plan should encompass immediate steps such as isolating affected systems to prevent further data exfiltration, conducting thorough forensic analysis to determine the extent of the breach and identify compromised data, containing the threat, eradicating the attacker’s presence, recovering systems and data, and conducting a post-mortem analysis to enhance future security postures. Proactive logging, centralized log management, and security information and event management (SIEM) systems are indispensable for effective detection and response.
Broader Implications and Future Cybersecurity Outlook
The MongoBleed vulnerability serves as a stark reminder of the intricate dependencies within modern software ecosystems and the persistent challenges of securing internet-facing infrastructure. The flaw’s origin in the zlib library, a foundational component, underscores the ripple effect that vulnerabilities in underlying software supply chain elements can have on widely deployed applications. This incident calls for renewed emphasis on memory safety in programming languages, rigorous input validation, and comprehensive security testing of all third-party libraries and components.
The coordinated disclosure and patching process, involving security researchers and MongoDB, exemplify the vital collaboration required to address widespread vulnerabilities effectively. However, the responsibility ultimately falls on organizations to prioritize patching and maintain continuous vigilance. The ongoing threat landscape necessitates a proactive and adaptive approach to cybersecurity, moving beyond reactive patching to embrace holistic security strategies that include network segmentation, robust monitoring, and a well-rehearsed incident response capability.
Looking ahead, as data increasingly becomes the lifeblood of organizations, the security of databases like MongoDB will remain a paramount concern. Regulatory frameworks such as GDPR, CCPA, and HIPAA impose stringent requirements for data protection, and breaches stemming from vulnerabilities like MongoBleed can lead to substantial fines and legal repercussions. The lessons learned from MongoBleed reinforce the imperative for secure-by-design principles, continuous vulnerability management, and a culture of cybersecurity awareness throughout all levels of an organization. Only through such sustained efforts can the digital assets underpinning our interconnected world be adequately protected against evolving cyber threats.