A highly sophisticated campaign attributed to a prominent Chinese state-sponsored cyberespionage collective has been uncovered, revealing the deployment of an advanced kernel-mode rootkit to meticulously conceal the activities of its signature ToneShell backdoor within government networks. This development marks a significant escalation in the tactical sophistication of a group known for its persistent targeting of sensitive institutions globally, introducing a new paradigm of evasion that fundamentally challenges conventional endpoint security mechanisms.
The cyberespionage group, widely tracked across the cybersecurity industry under various aliases including Mustang Panda, HoneyMyte, and Bronze President, has long been recognized for its persistent focus on government entities, non-governmental organizations (NGOs), think tanks, and other strategically important organizations worldwide. Their operational objectives typically revolve around intelligence gathering, intellectual property theft, and strategic data acquisition, aligning with broader state interests. The recent discovery by security researchers highlights a critical evolution in their methodologies, moving beyond user-mode malware to leverage kernel-level functionalities for unprecedented operational stealth and resilience.
The Evolving Threat Landscape: Mustang Panda’s Strategic Imperatives
Mustang Panda has established itself as one of the most active and persistent advanced persistent threat (APT) groups operating out of China. Active for over a decade, their campaigns are characterized by a blend of widely available tools and custom-developed malware, consistently evolving their tactics, techniques, and procedures (TTPs) to maintain an advantage over defensive measures. Their targets often include nations in Southeast Asia, Europe, and Africa, with a particular emphasis on organizations that possess information relevant to China’s geopolitical and economic interests. This strategic focus underscores the long-term, calculated nature of their cyber operations, which often involve sustained access to compromised networks over extended periods.
Historically, the group has relied on initial access vectors such as spear-phishing campaigns leveraging politically charged lures, exploitation of public-facing vulnerabilities, and supply chain compromises. Once initial access is achieved, they deploy a range of backdoors and information stealers, with ToneShell being a recurring element in their custom malware toolkit. The shift towards kernel-mode components signifies a deeper investment in operational security and a deliberate effort to circumvent the increasing efficacy of user-mode detection technologies. This tactical pivot suggests a response to enhanced defensive postures and a clear intent to secure more enduring and covert footholds within high-value targets.

ToneShell’s Transformation: Enhanced Stealth and Control
The ToneShell backdoor itself is a modular and adaptable piece of malware designed for remote access and control, facilitating intelligence collection and network reconnaissance. Earlier variants of ToneShell, while effective, operated predominantly within user-mode environments, making them susceptible to detection by advanced endpoint detection and response (EDR) solutions and behavioral analytics that monitor user-space activities. The newly analyzed variant, however, showcases significant enhancements aimed at bolstering its stealth and operational longevity.
A critical upgrade involves its host identification scheme, which now utilizes a compact 4-byte host ID marker, a departure from the more verbose 16-byte Globally Unique Identifier (GUID) previously employed. This seemingly minor alteration contributes to a smaller forensic footprint and potentially faster communication overhead. More profoundly, the new variant incorporates sophisticated network traffic obfuscation techniques, including the use of fake TLS (Transport Layer Security) headers. This method disguises command-and-control (C2) communications as legitimate encrypted web traffic, making it exceedingly difficult for network security appliances to distinguish malicious data exfiltration or command retrieval from normal, encrypted internet browsing. This technique is particularly effective against deep packet inspection and signature-based network intrusion detection systems, allowing the backdoor to blend seamlessly with benign network activity.
Furthermore, the command set supported by the new ToneShell variant has been expanded, offering attackers a broader array of remote operations. These include standard file system manipulation commands like pwd (print working directory), ls (list directory contents), and cd (change directory), alongside capabilities for upload and download files. More potent functionalities include exec (execute arbitrary commands), shell (launch a remote shell), exit (terminate connection), stop (stop specific processes), get_config and set_config (manage backdoor configuration), update (update the malware), and uninstall (remove the malware). This comprehensive suite of commands grants the threat actors granular control over compromised systems, enabling extensive data exfiltration, lateral movement, and the deployment of additional payloads, all while operating under a veil of enhanced secrecy.
The Kernel-Mode Rootkit: A Deep Dive into ProjectConfiguration.sys
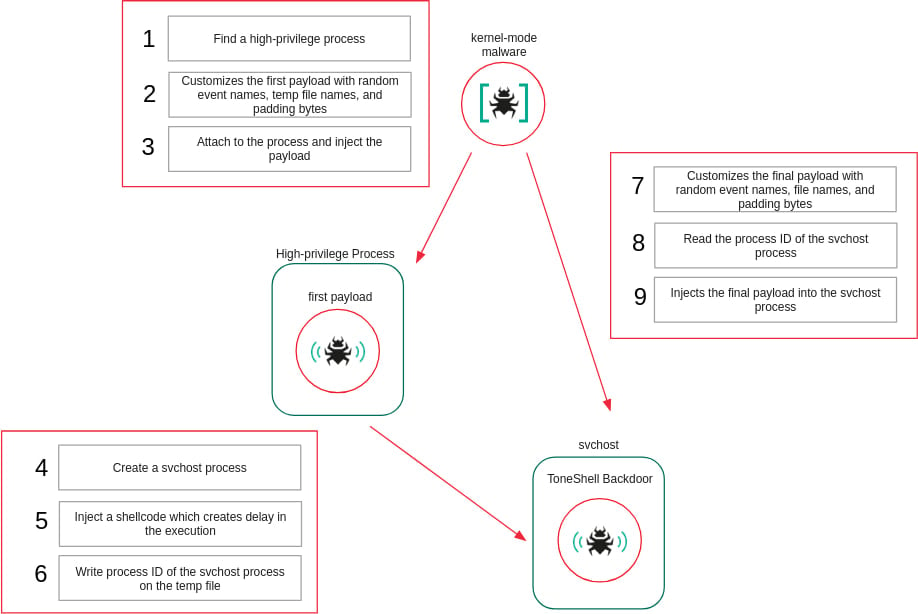
The most alarming aspect of this campaign is the introduction of a kernel-mode loader, ProjectConfiguration.sys, which functions as a sophisticated rootkit. Operating in kernel mode means this driver runs at the highest privilege level within the Windows operating system, directly interacting with the core components of the OS. This grants it unparalleled control over system functions and allows it to operate largely undetected by security software confined to user mode.

The ProjectConfiguration.sys driver is deployed as a mini-filter driver, a legitimate component of the Windows file-system I/O stack typically used by security products, encryption tools, and backup utilities to inspect, modify, or block file operations. By masquerading as such a legitimate component, the malicious driver gains a foothold deep within the OS architecture. Its signing with a stolen or leaked certificate, valid between 2012 and 2015 and issued to Guangzhou Kingteller Technology Co., Ltd., adds a layer of deceptive legitimacy. The use of an older, potentially revoked, or compromised certificate highlights the attackers’ efforts to bypass basic trust checks, though modern systems might flag such certificates. However, the initial compromise and installation could have occurred in environments with less stringent certificate validation or during periods when the certificate was still considered valid.
The rootkit’s stealth mechanisms are multifaceted:
- Runtime API Resolution: To evade static analysis, the driver does not directly import kernel APIs. Instead, it resolves necessary functions at runtime by enumerating loaded kernel modules and matching function hashes. This technique makes it significantly harder for security tools to identify its malicious intent through static code analysis or by scanning for known API import tables.
- Self-Protection: The driver is engineered to protect itself from removal or tampering. It registers as a mini-filter driver and actively intercepts file-system operations targeting its own files (e.g., deletion, renaming), blocking these requests to ensure its persistence on the system. Furthermore, it registers a registry callback to deny attempts to create or open its service-related registry keys, thereby safeguarding its configuration and startup entries.
- Antivirus Evasion: A critical capability of the rootkit is its ability to interfere with host-based security products. It achieves this by modifying the configuration of Microsoft Defender’s
WdFilterdriver, preventing it from loading into the I/O stack. This effectively disables a fundamental layer of Microsoft’s native endpoint protection. Additionally, the rootkit strategically selects a mini-filter altitude above the antivirus-reserved range. In the Windows filter manager architecture, altitude determines the order in which filter drivers process I/O requests; a higher altitude means the malicious driver processes requests before security products, allowing it to hide its activities or block security scans before they can detect it. - Payload Protection: The rootkit maintains a dynamic list of protected process IDs. When user-mode shellcodes (embedded within its
.datasection and executed as separate threads, injected into user-mode processes) are active, the driver denies handle access to these processes. This prevents security tools or forensic investigators from inspecting or terminating the injected payloads, only removing protection once execution completes, making live analysis extremely challenging.
This deep level of integration and control in the kernel fundamentally alters the defensive calculus. Traditional user-mode monitoring solutions are largely blind to such operations, as the rootkit operates below their visibility layer, effectively creating an invisible operational space for the threat actors.
Campaign Overview and Targeting
The campaign has been active since at least February 2025, primarily targeting government organizations in Myanmar, Thailand, and other countries across Asia. Evidence suggests that compromised entities often exhibited prior infections with older ToneShell variants, PlugX malware, or the ToneDisk USB worm—all tools previously attributed to Chinese state-sponsored actors. This pattern indicates either a sustained, multi-stage compromise strategy, where initial, less sophisticated malware paves the way for more advanced tools, or a re-compromise of previously breached networks with enhanced capabilities. The geographic focus aligns perfectly with Mustang Panda’s historical targets, reinforcing the attribution. The use of a kernel-mode rootkit in these sensitive environments signifies a desire for long-term, stealthy espionage, likely aimed at acquiring critical geopolitical or economic intelligence.
Implications for Global Cybersecurity and Defensive Strategies
The deployment of a kernel-mode rootkit by a prominent state-sponsored actor represents a critical inflection point in the cyber arms race. The implications are profound:
- Elevated Detection Difficulty: Kernel-mode threats are notoriously difficult to detect and remediate. They bypass conventional user-mode security controls and often require specialized tools and deep system visibility, including memory forensics and kernel-level integrity monitoring.
- Enhanced Persistence: By operating at the core of the OS and actively protecting itself, the rootkit ensures high persistence, making eradication a complex and resource-intensive task, often requiring full system re-imaging.
- Undermined Trust in Security Software: The ability to disable or circumvent endpoint security solutions at the kernel level erodes the fundamental trust placed in these defensive tools, necessitating a re-evaluation of security architectures.
- Increased Resource Investment by Attackers: Developing and maintaining kernel-mode malware requires significant technical expertise and resources, indicative of a well-funded and highly capable state-sponsored program. This suggests a long-term commitment to high-stakes cyberespionage.
- Supply Chain Vulnerability: The use of stolen or leaked certificates for code signing highlights potential vulnerabilities within the software supply chain or certificate authority ecosystem, which adversaries can exploit to lend legitimacy to their malicious code.
To counter such sophisticated threats, organizations, particularly those in critical infrastructure and government sectors, must adopt a multi-layered and proactive defense strategy:
- Advanced Endpoint Protection: Deploying next-generation endpoint detection and response (XDR/EDR) solutions with kernel-level visibility, behavioral analytics, and robust anti-rootkit capabilities is paramount. These systems should focus on detecting anomalous kernel activity, driver integrity, and unusual process injection.
- Memory Forensics and Threat Hunting: Regular and in-depth memory forensics is crucial for uncovering kernel-mode infections that hide their activity from file-system and process monitors. Proactive threat hunting, utilizing indicators of compromise (IoCs) and behavioral anomalies, can help identify subtle traces of compromise.
- Strict Code Signing Policies: Implement stringent policies for driver signing and integrity checks. Regularly audit and monitor certificates used within the environment, and establish robust mechanisms to detect the use of compromised or revoked certificates.
- Patch Management and System Hardening: Maintain rigorous patch management for operating systems, drivers, and all applications to minimize exploitation opportunities. Harden systems by disabling unnecessary services, implementing application whitelisting, and enforcing the principle of least privilege.
- Network Segmentation and Monitoring: Segment networks to limit lateral movement and implement deep packet inspection (DPI) and behavioral analytics on network traffic to identify obfuscated C2 communications, even those mimicking legitimate protocols like TLS.
- User Awareness Training: Continue to educate users about spear-phishing tactics and social engineering, as these remain primary initial access vectors for even the most sophisticated campaigns.
- Incident Response Preparedness: Develop and regularly test comprehensive incident response plans specifically tailored to address kernel-mode rootkits, ensuring capabilities for rapid containment, eradication, and recovery.
The latest evolution of Mustang Panda’s TTPs underscores the escalating nature of state-sponsored cyber threats. The deployment of kernel-mode rootkits to achieve unparalleled stealth and persistence in high-stakes cyberespionage campaigns demands a fundamental recalibration of defensive strategies. As adversaries continue to innovate, the cybersecurity community must adapt with equally advanced detection, prevention, and response capabilities to safeguard critical information and infrastructure from these increasingly sophisticated and covert operations.